UEFI (Unified Extensible Firmware Interface)-based backup and one-key startup item guiding method
A startup item and backup technology, applied in the direction of boot program, program loading/starting, error detection of redundant data in operation, etc., can solve problems such as lack of system backup, reduce the difficulty of use, avoid data leakage, Simple to use effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
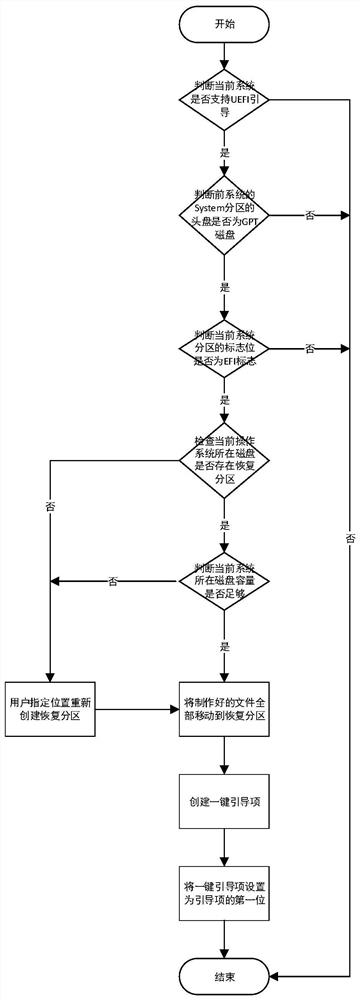
[0056] Such as figure 1 Described, a kind of backup method based on UEFI, comprises the following steps:
[0057] System judgment step: by invoking NtQuerySystemInformation, and obtaining the boot type of the current system through SystemBootEnvironmentInformation query, judging whether the current system supports UEFI boot; if yes, continue, if not, end;
[0058] System partition detection step: detect the System partition of the current system, if it is detected that the first disk where the System partition of the current system is located is a GPT disk, and the flag of the current system partition is the flag of the EFI partition, then keep the symbolic link of the partition; if If not, end;
[0059] Recovery partition detection step: check whether there is a recovery partition on the disk where the current operating system is located, if it exists, go to the next step, if it does not exist, recreate the recovery partition according to the location specified by the user;
...
Embodiment 2
[0100] In the present invention, the specific implementation steps are: a) check whether the current system supports UEFI boot, if not, enter the one-key boot process of Legacy, if it is detected that the head disk where the System partition of the current system is located is a GPT disk, and the current system If the logo of the partition is the logo of the EFI partition, then save the symbolic link of the partition.
[0101] b) Check whether there is a recovery partition on the disk where the current operating system is located. If not, it needs to be created. Check whether the disk where the current operating system is located meets the conditions for creating a recovery partition environment. If not, you need to adjust the partition of the current disk user-specified Create a recovery partition after the size; if there is a recovery partition on the disk where the current operating system is located, the capacity is sufficient to save the system backup image file, no adjust...
Embodiment 3
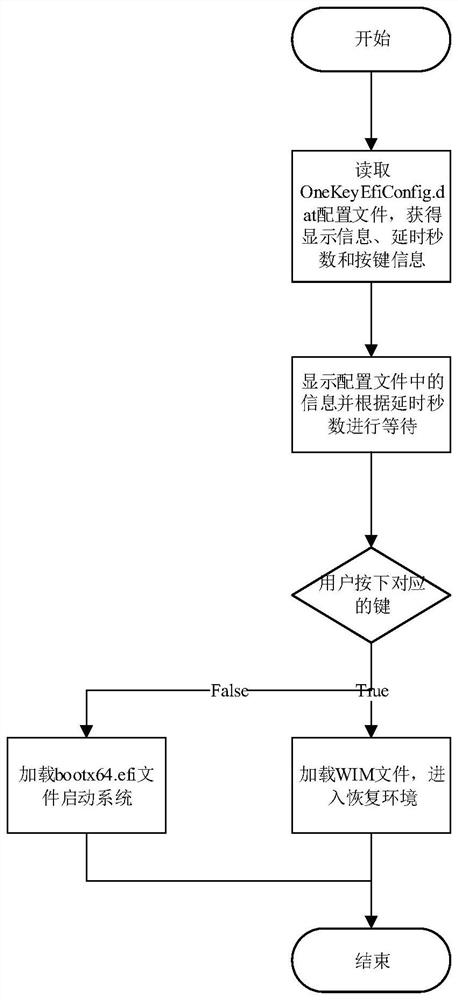
[0114] This embodiment is a further refinement of the second embodiment. The specific process of one-key boot is as follows: 1. According to the above steps, the BIOS can load the AomeiPeLdr.efi program normally. AomeiPeLdr.efi is mainly responsible for two things: 1. Load the WIM file and start the recovery environment; 2. Load the current system’s The bootmgr.efi program starts the current system;
[0115] 2. When the BIOS loads AomeiPeLdr.efi successfully, AomeiPeLdr.efi will read the OneKeyEfiConfig.dat file to read the display information, delay information and button configuration, and AomeiPeLdr.efi will display relevant information according to the display information and delay information. On the screen, if the user presses the button corresponding to the configuration within the delay range, it will enter the recovery environment, and if the corresponding button is not pressed after the timeout, the current operating system will be booted.
[0116] 3. AomeiPeLdr.efi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com