Two-stage image robust reversible information hiding method based on singular value decomposition
A singular value decomposition and information hiding technology, which is applied in the field of two-stage image robust and reversible information hiding, can solve problems such as decoding failure, and achieve the effect of improving feasibility, wide application prospect and reducing distortion.
Pending Publication Date: 2022-03-11
江苏水印科技有限公司
View PDF0 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
However, the robust feature used by the classic robust reversible watermarking algorithm is related to the position of the pixel, which leads to the failure of decoding for geometric attacks.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment
[0098] 1. When the embedded watermark bit is 0 or 1, the proof of the formula for extracting the watermark from the watermarked image under attack.
[0099] Suppose when the watermark bit w i = 1,
[0100]
[0101] Let Δ=2k,
[0102] When the watermark bit w i = 0,
[0103] J w The fractional part of is
[0104]
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
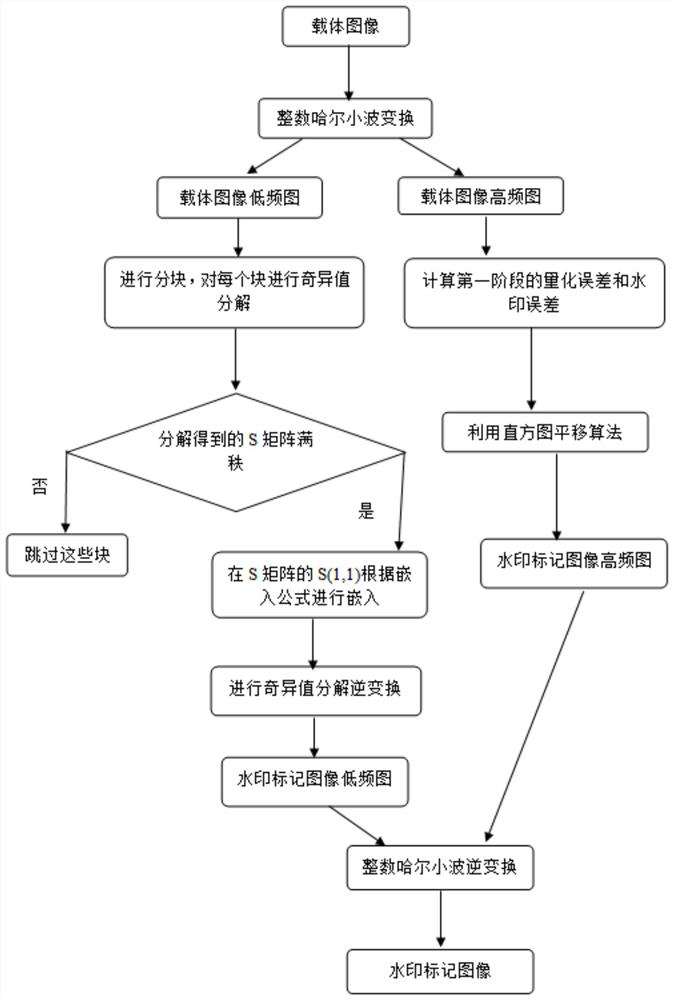
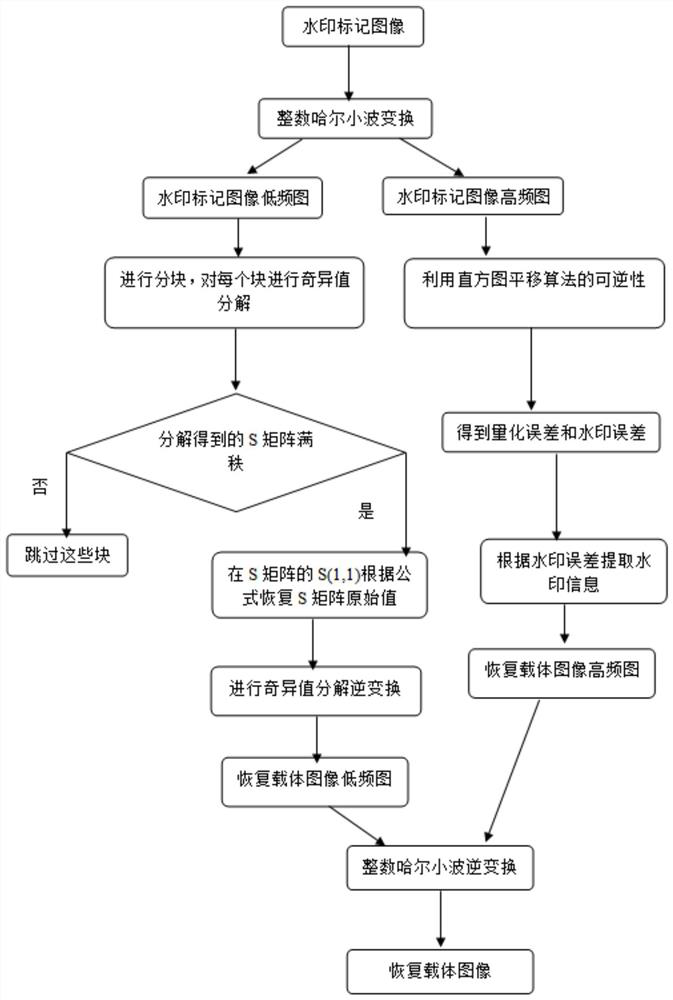
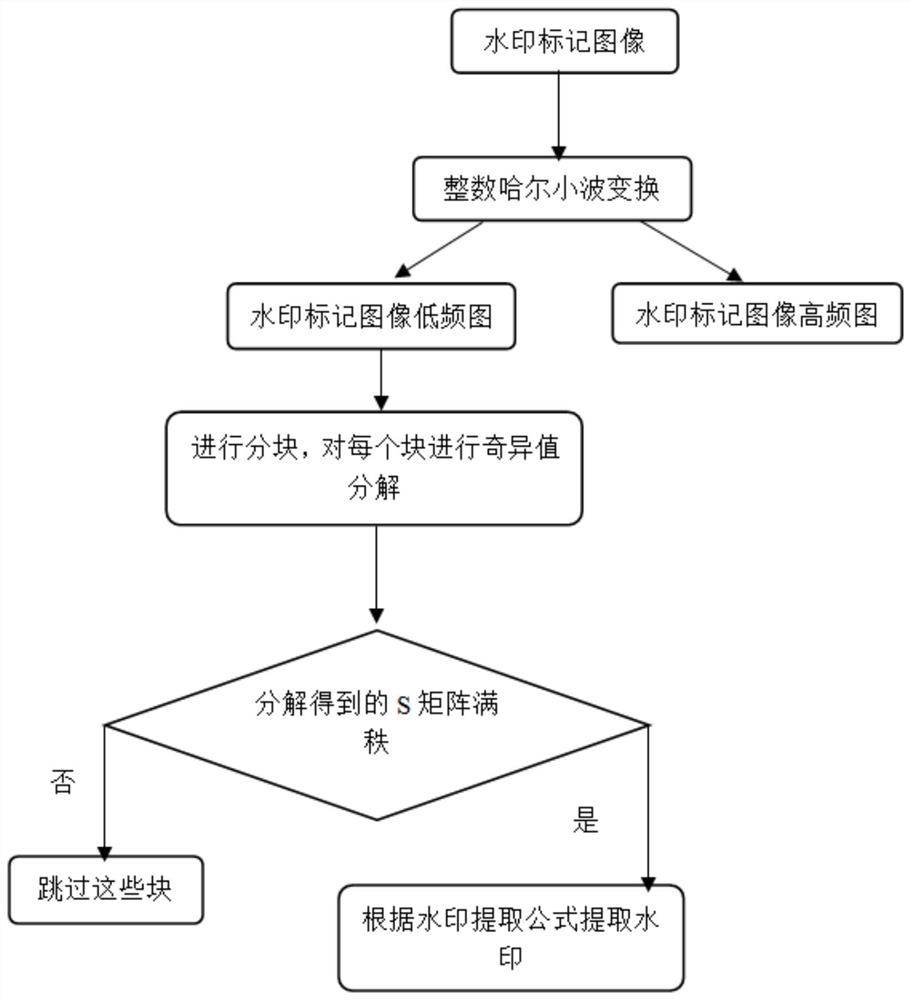
The invention discloses a two-stage image robust reversible information hiding method based on singular value decomposition, which comprises the steps of embedding a watermark and extracting the watermark, and when the watermark is extracted, the watermark is extracted in different ways according to whether an image is attacked or not. According to the method, the watermark is embedded into the maximum value in the S matrix which is not easy to change even when attacked through singular value decomposition, and compared with a classical robust reversible information hiding algorithm, the method can effectively resist malicious attacks such as JPEG attacks, Gaussian filtering and scaling. In addition, the designed improved quantization watermark algorithm rounds the S value to effectively reduce the auxiliary information embedded in the second stage, and the quantization error and the watermark error in the first stage are used as the auxiliary information embedded in the second stage to improve the feasibility of the reversible embedding amount. The method can be applied to the fields of copyright protection, image protection and the like, and has a wide application prospect.
Description
technical field [0001] The invention belongs to the technical field of image analysis, in particular to a two-stage image robust reversible information hiding method based on singular value decomposition. Background technique [0002] In satellite images, medical images, and micro-images, which have high requirements for image fidelity and robustness, the irreversible loss of robust watermarking and the fragility of reversible watermarking are intolerable, which makes the research The researchers developed a brand new watermarking algorithm: robust reversible watermarking algorithm. In the absence of attack, the robust reversible watermarking algorithm can extract the watermark and recover the cover image at the decoding end. However, when the watermarked image is maliciously attacked, the watermark can also be extracted correctly, but the reversibility is destroyed, making the carrier image irrecoverable. [0003] The early robust reversible watermarking algorithm propose...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): G06T1/00
CPCG06T1/005G06T2201/0065
Inventor 钱阳周洁刘建荣
Owner 江苏水印科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com