Computer attack information storage method and device and electronic equipment
An information storage and computer technology, applied in the field of network security, can solve the problems of being unable to trace the source of the attack, unable to reproduce the attack method, etc., and achieve the effect of increasing the difficulty of identification, increasing the difficulty of destroying, and reducing the possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
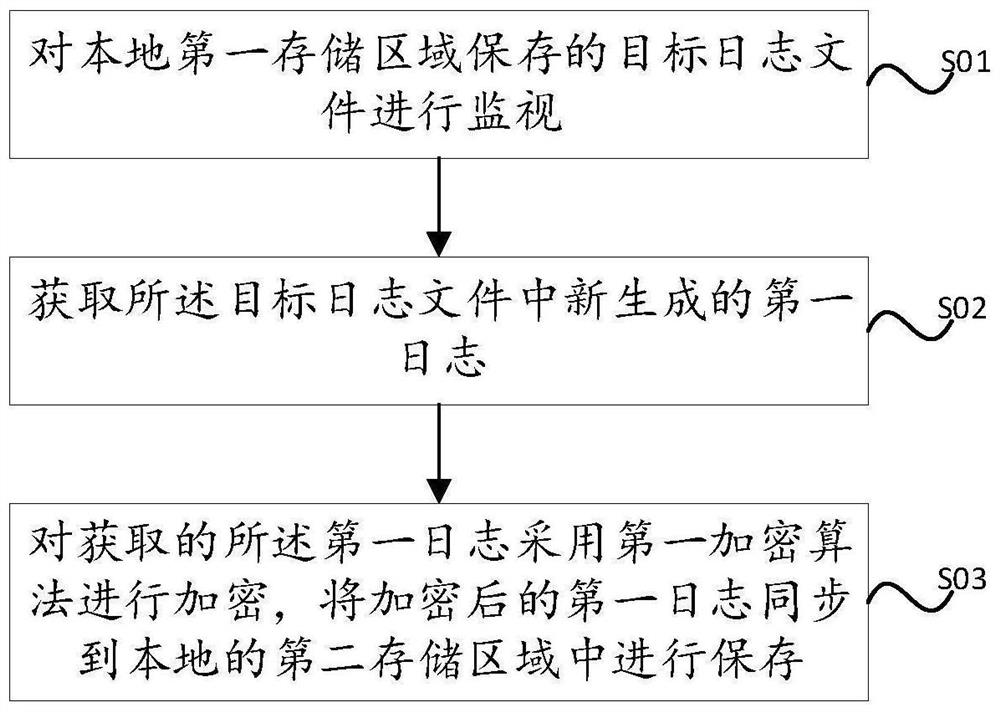
[0025] see figure 1 As shown, a computer attack information storage method provided by an embodiment of the present invention includes:
[0026] S01. Monitor the target log file stored in the local first storage area.
[0027] The local refers to the local computer (or client computer).
[0028] The first storage area refers to a preset storage area of the local storage hard disk.
[0029] Log files are files that record events that occur during the operation of an operating system or other software, or messages between different users of communication software. The target log file refers to the log file that can be used to trace the source of the attack and reproduce the attack method when a network security attack event occurs locally, such as the local system and process behavior logs.
[0030] S02. Obtain the newly generated first log in the target log file.
[0031] S03. Encrypt the acquired first log using a first encryption algorithm, and synchronize the encrypted...
Embodiment 2
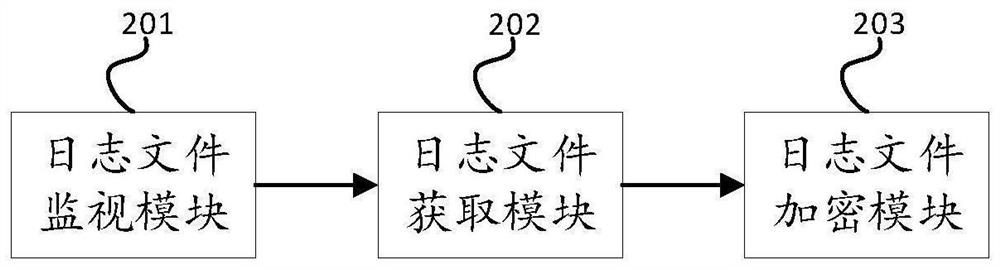
[0050] see figure 2 As shown, the embodiment of the present invention provides a computer attack information storage device, including: a log file monitoring module 201, configured to monitor the target log files stored in the local first storage area; a log file acquisition module 202, configured to acquire the The newly generated first log in the target log file; the log file encryption module 203 is used to encrypt the obtained first log using the first encryption algorithm, and synchronize the encrypted first log to the second local storage Save in the area.
[0051] An embodiment of the present invention provides a computer attack information storage device. The first log of the target log file stored in the first storage area is encrypted by the log file encryption module 203, which increases the difficulty of identifying the target log file. By encrypting the encrypted The first log is synchronized to the second storage area for storage, so that the second storage are...
Embodiment 3
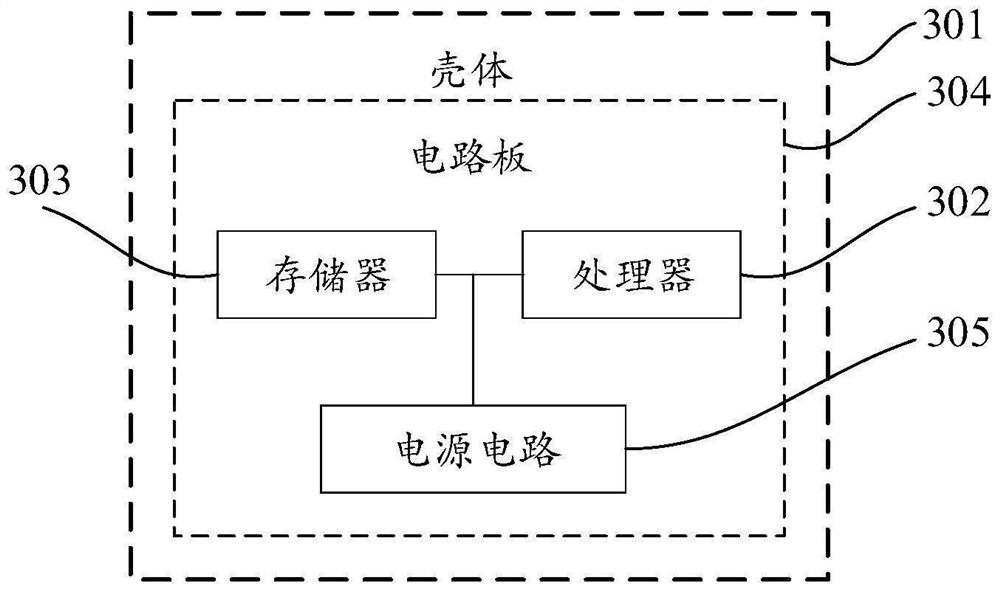
[0061] see image 3 As shown, the embodiment of the present invention provides an electronic device, the electronic device includes: a housing 301, a processor 302, a memory 303, a circuit board 304 and a power supply circuit 305, wherein the circuit board 304 is placed in the housing 301 Inside the enclosed space, the processor 302 and the memory 303 are arranged on the circuit board 304, and the power supply circuit 305 is used to supply power for each circuit or device of the above-mentioned electronic equipment; the memory 303 is used to store executable program code; the processor 302 passes The executable program code stored in the memory 303 is read to run a program corresponding to the executable program code, which is used to execute the data transmission method described in any one of the foregoing first aspects.
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap