Embedded security module system
A security module and embedded technology, applied in response to error generation, digital data authentication, digital data protection, etc., can solve the problems of embedded devices or systems with poor risk resistance, and achieve strong resistance to power consumption analysis and electromagnetic analysis Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
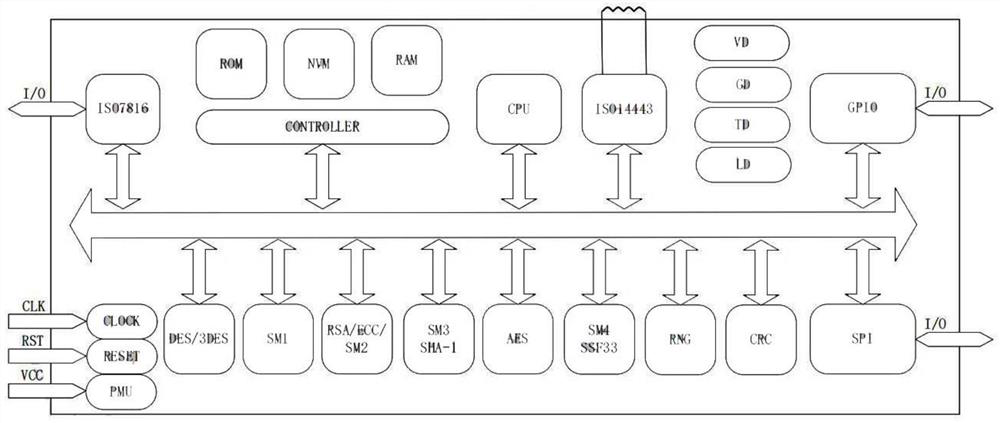
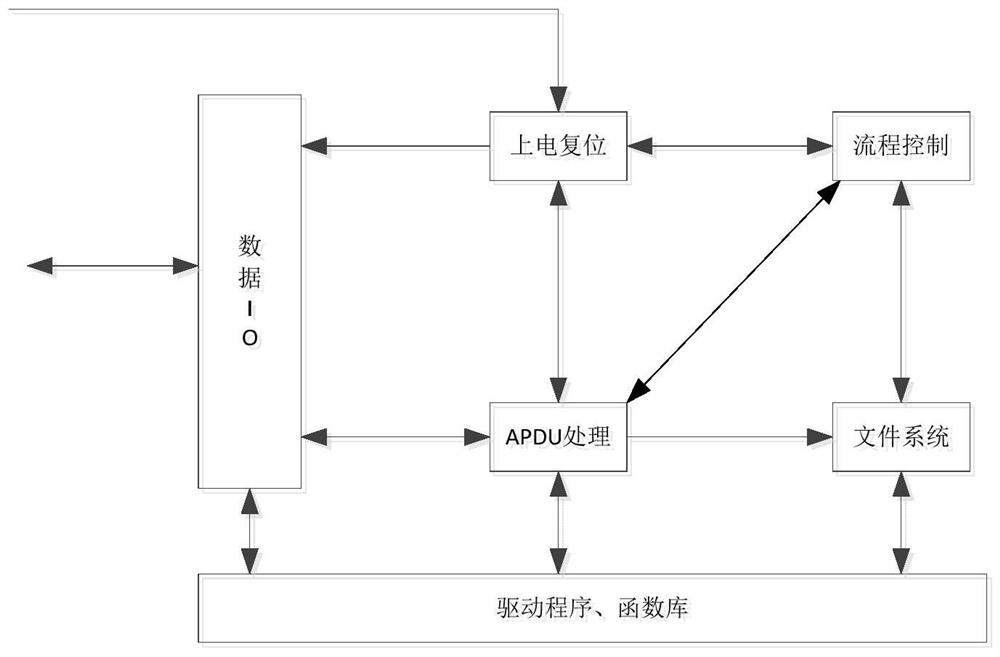
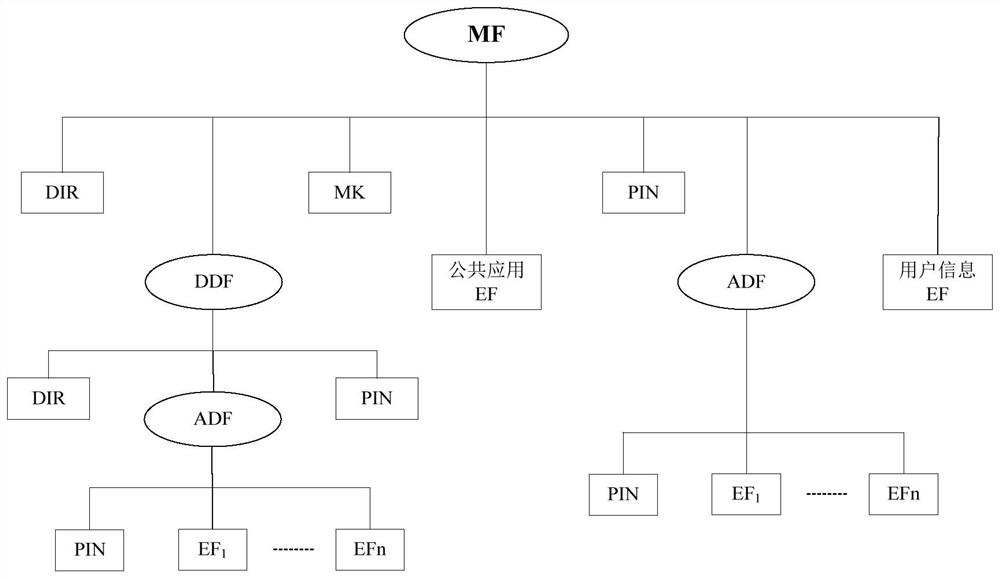
[0027] This embodiment discloses an embedded security module system, the security module of the system has functions such as file system, data I / O, data encryption and decryption, data signature and verification, key generation, true random number generator, etc. The security function of the module can be invoked externally through the APDU command, which can provide security protection for information transmission in the field of regional comprehensive energy management and energy Internet of Things.
[0028] The HRT6701 embedded security module adopts a 32-bit CPU core with high security, high performance and low power consumption. The maximum operating clock supports 67.5MHz, the operating voltage is 1.62V-5.5V, the maximum operating current is less than 7mA, and the sleep current is less than 80uA. Configure 384K ROM as the storage of infrequently changing data such as driver programs and function libraries, and have 192KB EEPROM storage space for storing COS codes and data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com