Vehicle data message secure communication method
A technology of secure communication and vehicle data, applied in the field of vehicle communication, can solve the problems of heavy control logic workload, inability to judge messages, and difficult reverse analysis, etc., to achieve the effect of improving security performance, avoiding playback attacks, and avoiding the risk of eavesdropping
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
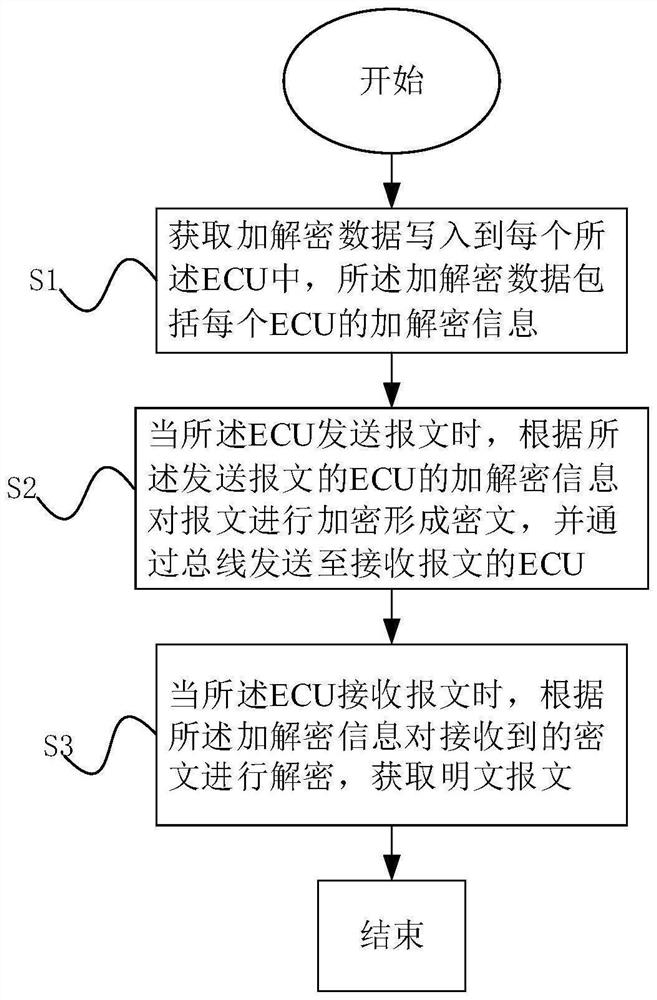
[0049] A method for safe communication of vehicle data messages, used for communication of ECUs of vehicles, where the ECUs of vehicles are connected through a communication bus, such as figure 1 As shown, the communication method includes the following steps:
[0050] S1: Obtain encryption and decryption data and write them into each of the ECUs, where the encryption and decryption data includes encryption and decryption information of each ECU.
[0051] Each ECU is assigned a corresponding encryption and decryption information, and the encryption and decryption information includes source address, identification, key seed and key. In this embodiment, the communication bus adopts the CAN-FD bus, and its corresponding data frames are shown in Table 1 below,
[0052] Table 1 Data segment division of CAN-FD data frame
[0053] source address period Identification segment message segment 1 byte 7 bytes 2 bytes 54 bytes
[0054] Correspondingly, t...
Embodiment 2
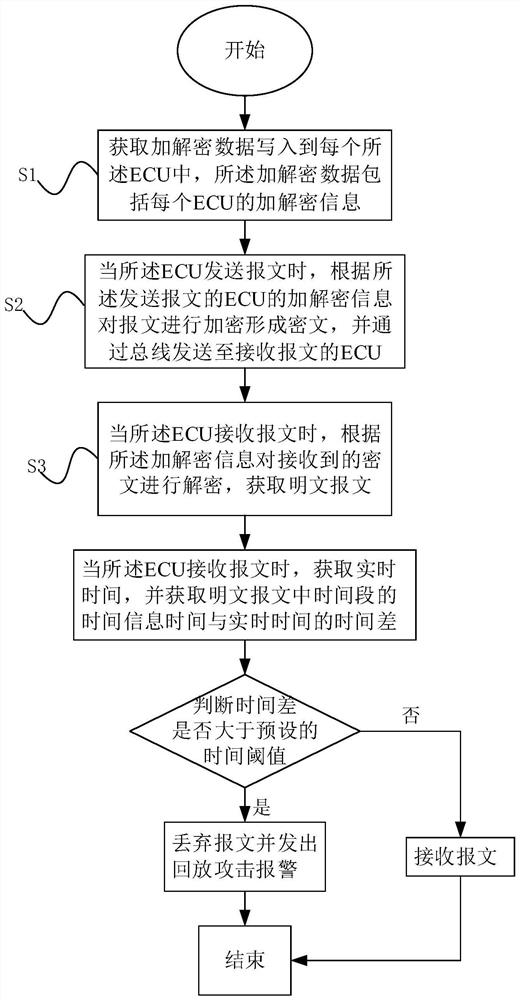
[0066] The difference between this embodiment and embodiment 1 is that, as figure 2 As shown, step S4 is also included:
[0067] When the ECU receives the message, obtain the real time, and obtain the time difference between the time information time of the time period in the plaintext message and the real time, judge whether the time difference is greater than the preset time threshold, if greater, discard the message and send a playback Attack alarm; if less than, receive the message.
[0068] The way to get the real time is:
[0069] The communication module of the vehicle obtains the current time and sends it to the vehicle gateway. The vehicle gateway randomly sends a set of key seeds to all ECUs. The ECU writes the key seeds into the encrypted and decrypted data and starts real-time timing according to the time signal.
[0070] Specifically, in this embodiment, the vehicle gateway will connect all the CAN-FD modules of the vehicle, and there will be a module with 4G c...
Embodiment 3
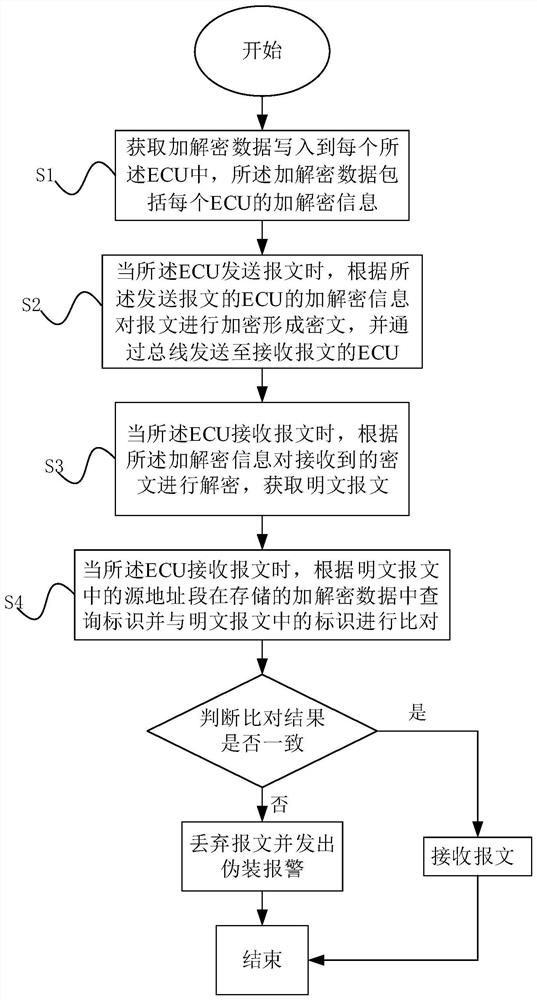
[0075] The difference between this embodiment and embodiment 1 is that, as image 3 As shown, step S4 is also included:
[0076] When the ECU receives the message, it searches the encrypted and decrypted data stored for the identifier according to the source address segment in the plaintext message and compares it with the identifier in the plaintext message. If the comparison is inconsistent, discard the message and issue a camouflage Alarm; if the comparison is consistent, receive the message. Specifically, the receiving ECU finds the corresponding identification parameters in its own ECU source address, identification, key seed and key through the source address segment parameters, and compares them with the identification parameters in the plaintext to see if they are the same, if not, then explain The signal may be spoofed and discarded with a spoofed alarm.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com