Access control method and system based on atlas
An access control and graph technology, applied in the field of graph-based access control methods and systems, can solve problems such as the incompatibility of the open Internet, and achieve the effect of overcoming inflexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
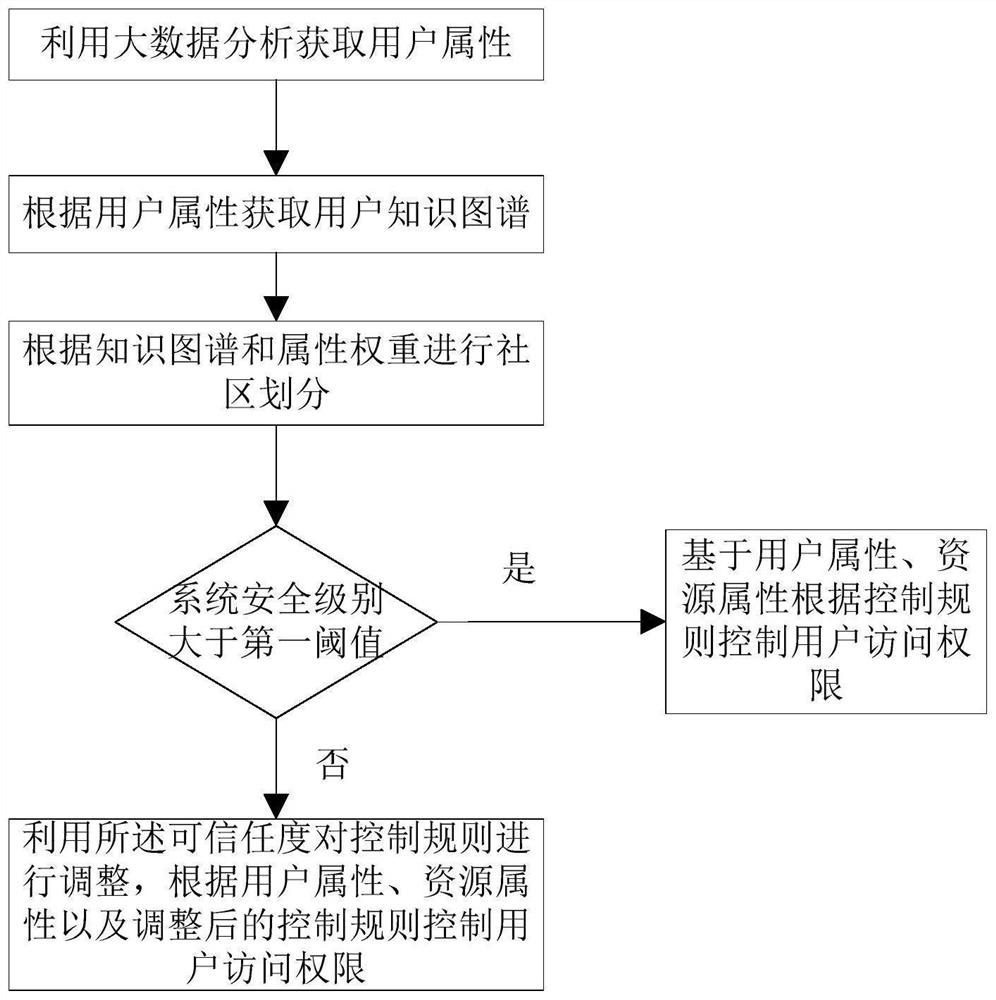
[0038] like figure 1 As shown, the present invention provides a graph-based access control method, the method includes the following steps:
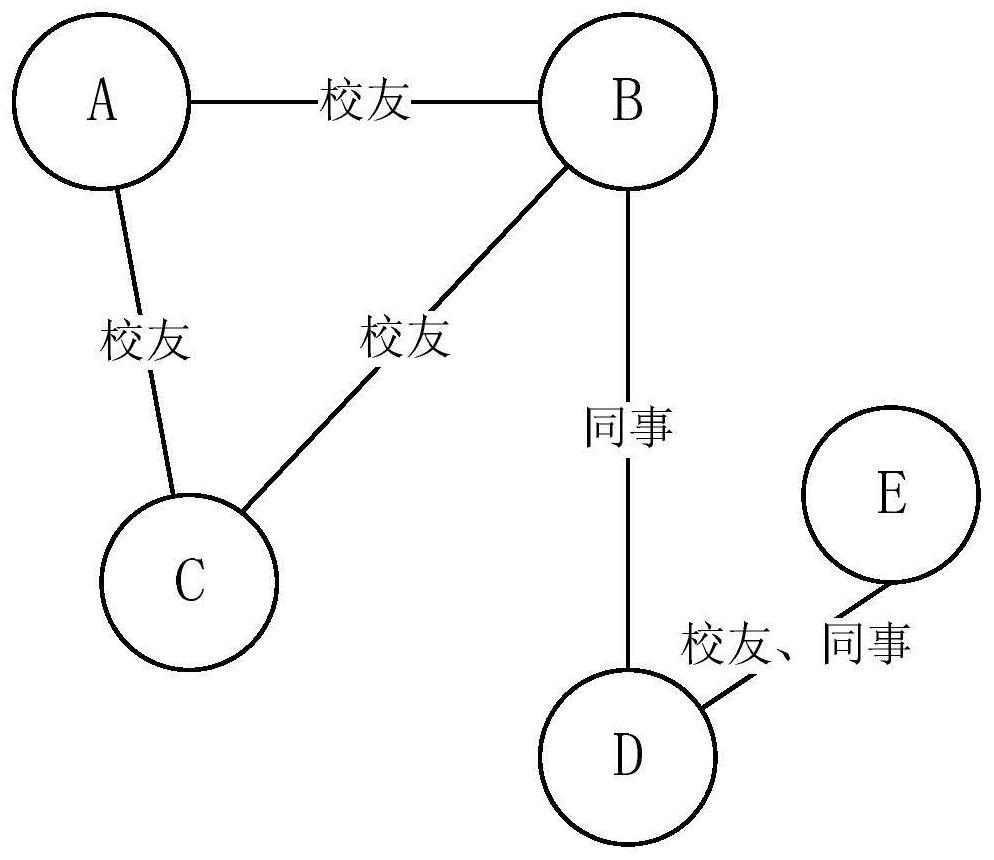
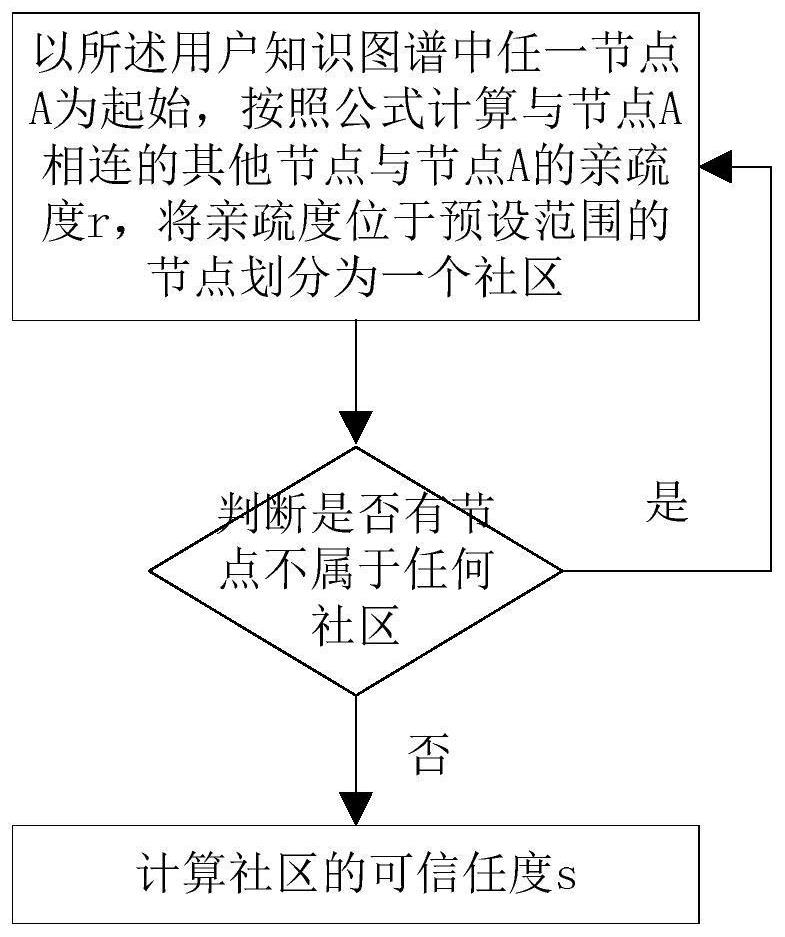
[0039] S1, set a data source for big data analysis, analyze the structured, semi-structured, and unstructured data in the data source to obtain user attributes, build a user map based on the user attributes, according to the user map and the set Attribute weight value, divide users into communities, and calculate the trustworthiness of the community;
[0040] The users of different systems are different. The users of the enterprise resource system are the employees of the enterprise, and there may also be some sellers and consumers. For the shared resource websites of the open Internet, the users are mainly netizens. Different systems also have different ways of acquiring user attributes. When using the access control method provided by the present invention, it is necessary to set a data source for big data analysis according to the syst...
Embodiment 2
[0067] image 3 The architecture diagram of the present invention is shown. The present invention also provides a graph-based access control system. When a user accesses a resource, first obtains the user's community, and then judges whether to allow access to the resource according to the control rules. The system includes the following modules:
[0068] The user community division module is used to set the data source for big data analysis, analyze the structured, semi-structured, and unstructured data in the data source to obtain user attributes, and build a user map based on the user attributes. User graphs and set attribute weights, divide users into communities, and calculate community trustworthiness;
[0069]The access control module is used to adjust the system risk level according to the environment attribute, the environment attribute includes the resource utilization rate of the host where the resource is located, and the number of attacks per unit time; if the sy...
Embodiment 3
[0079] The present invention also provides a computer-readable storage medium for storing computer program instructions, the computer program instructions implementing the method according to the first embodiment when executed by a processor.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com