Malicious code detection method and device and computer readable storage medium
A malicious code detection and malicious code technology, applied in the detection of malicious code, computer-readable storage media, can solve the problem of partially ignoring the interpretation of feature extraction and analysis schemes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
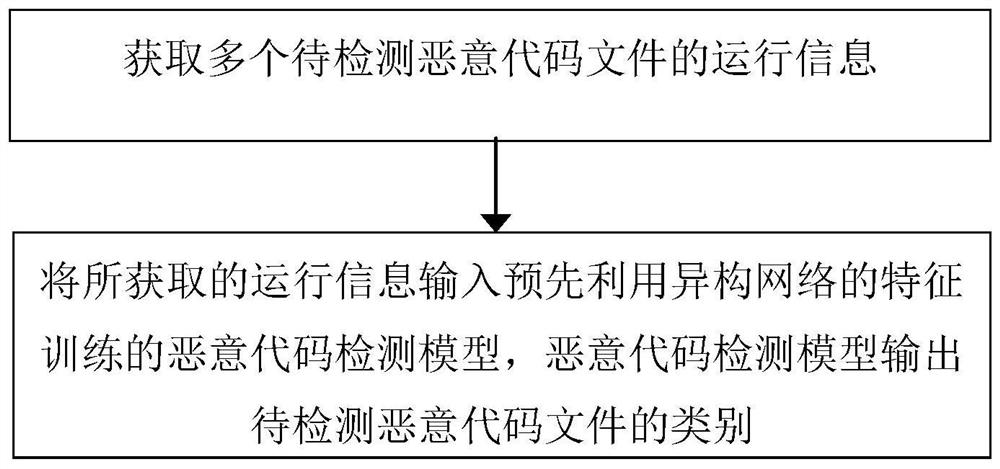
[0048] figure 1 It is a schematic flowchart of a method for detecting malicious code according to an embodiment of the present invention. like figure 1 , a method for detecting malicious code according to an embodiment of the present invention, which is used to detect the category of binary malicious code, including: obtaining the running information of the malicious code file to be detected, the running information including the API calling information of the malicious code file to be detected, or The operation information includes API call information and DLL call information; the obtained operation information is input into the malicious code detection model trained in advance using the characteristics of the heterogeneous network, and the malicious code detection model outputs the category of the malicious code file to be detected.
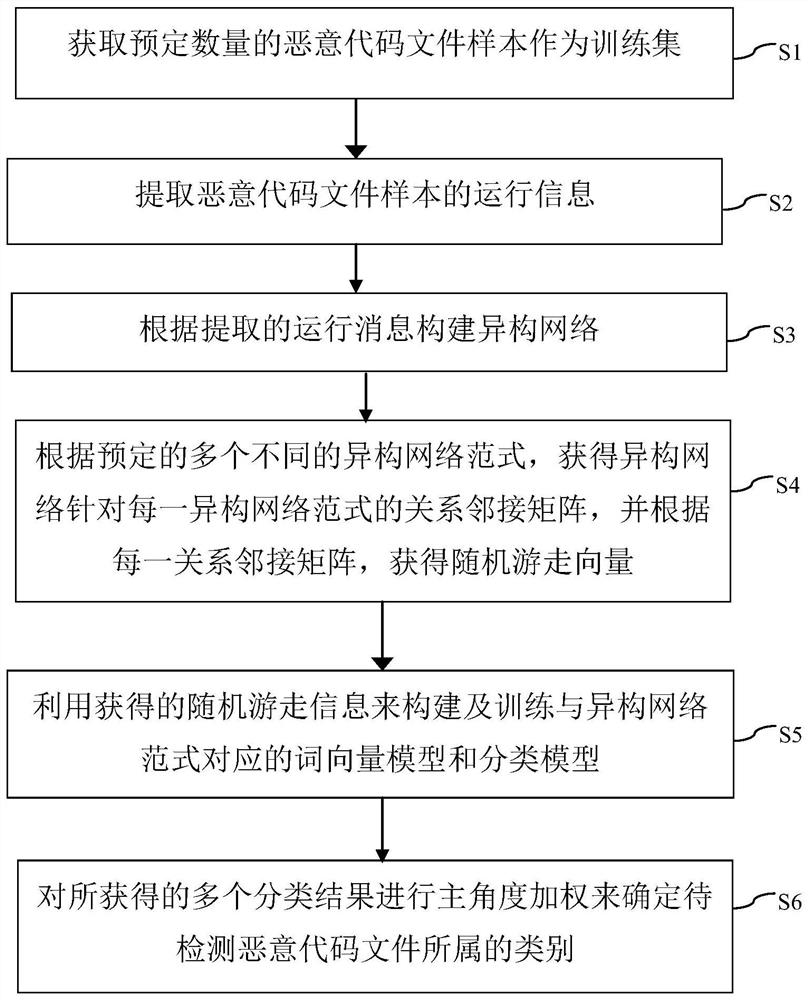
[0049] figure 2 This is a schematic flowchart of training a malicious code detection model in a malicious code detection method accordin...
Embodiment 2
[0058] overall design
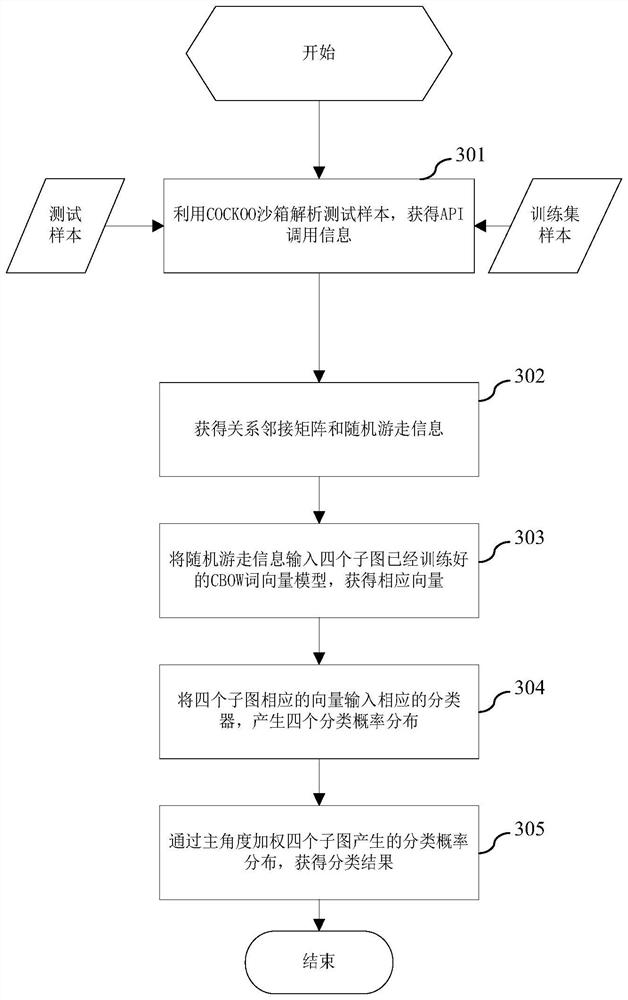
[0059] image 3 It is a schematic diagram of an overall design flow of a malicious code detection method according to another embodiment of the present invention. like image 3 , in this embodiment, the data to be used is obtained by analyzing the malicious code test sample in the Cuckoo sandbox, and the obtained information includes API information, dynamic link DLL information, relevant text information, and the like. The detection method of this embodiment mainly involves the content of random walk scheme, word vector training, classifier design and so on.
[0060] In the detection method of the embodiment of the present invention, a malicious code test sample is input, and the category to which the sample belongs is output. The malicious test code test sample is an executable file. like image 3 , the detection method of the embodiment of the present invention comprises:
[0061] Step 301, use the cuckoo sandbox to parse the test sample to ob...
Embodiment 3
[0102] The invention also provides a detection device for malicious code, such as Figure 14 As shown, the apparatus includes a processor 1401, a memory 1402, a bus 1403, and a computer program stored in the memory 1402 and executable on the processor 1401, the processor 1401 including one or more processing cores, a memory 1402 is connected to the processor 1401 through the bus 1403, and the memory 1402 is used for storing program instructions. When the processor executes the computer program, the steps in the above method embodiment of the first embodiment of the present invention are implemented.
[0103] Further, as an executable solution, the device for identifying microplastics may be a computer unit, and the computer unit may be a computing device such as a desktop computer, a notebook computer, a palmtop computer, and a cloud server. The computer unit may include, but is not limited to, a processor, a memory. Those skilled in the art can understand that the compositio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com