Fully homomorphic block chain privacy protection method based on Shamir threshold secret sharing
A threshold secret and privacy protection technology, which is applied in the field of Internet privacy protection, can solve the problems of difficulty in taking into account the availability of blockchain, the confidentiality of private information, and the difficulty of satisfying the verifiability and computability of ciphertext at the same time, so as to improve the effectiveness and The effect of privacy, meeting confidentiality, and guaranteeing availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0079] This embodiment discloses a fully homomorphic blockchain privacy protection method based on Shamir threshold secret sharing.
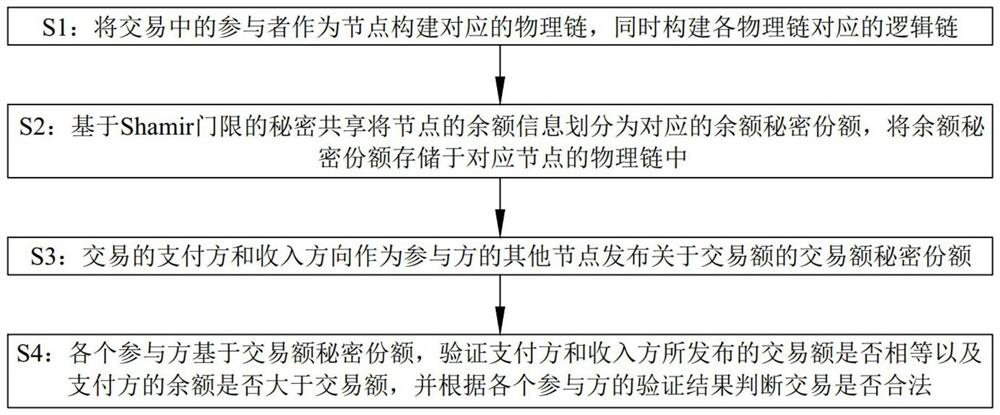
[0080] like figure 1 As shown, a fully homomorphic blockchain privacy protection method based on Shamir threshold secret sharing, including:
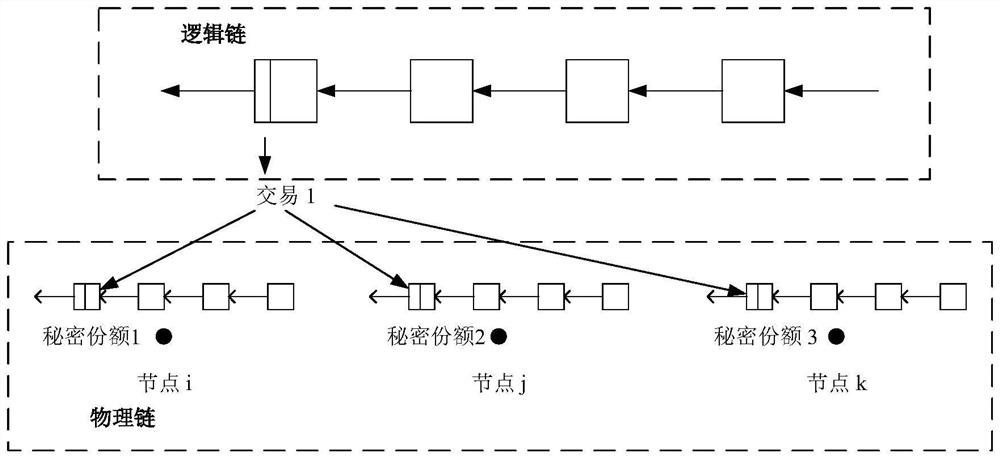
[0081] S1: Use the participants in the transaction as nodes to build the corresponding physical chain, and at the same time build the logical chain corresponding to each physical chain;
[0082] S2: The balance information of the node is divided into corresponding balance secret shares based on Shamir threshold secret sharing, and the balance secret share is stored in the physical chain of the corresponding node; in this embodiment, the local physical chain of each node stores all nodes The balance of the secret share.
[0083] S3: The payer and the earner of the transaction publish the secret share of the transaction amount about the transaction amount to other nodes as participants;
[0084] S4: Base...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com