Automatic verification method for security of communication software
An automatic verification and communication software technology, applied in the field of communication security verification, can solve problems such as leakage of real information and potential safety hazards, and achieve the effects of ensuring normal use, improving accuracy, transparency and openness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
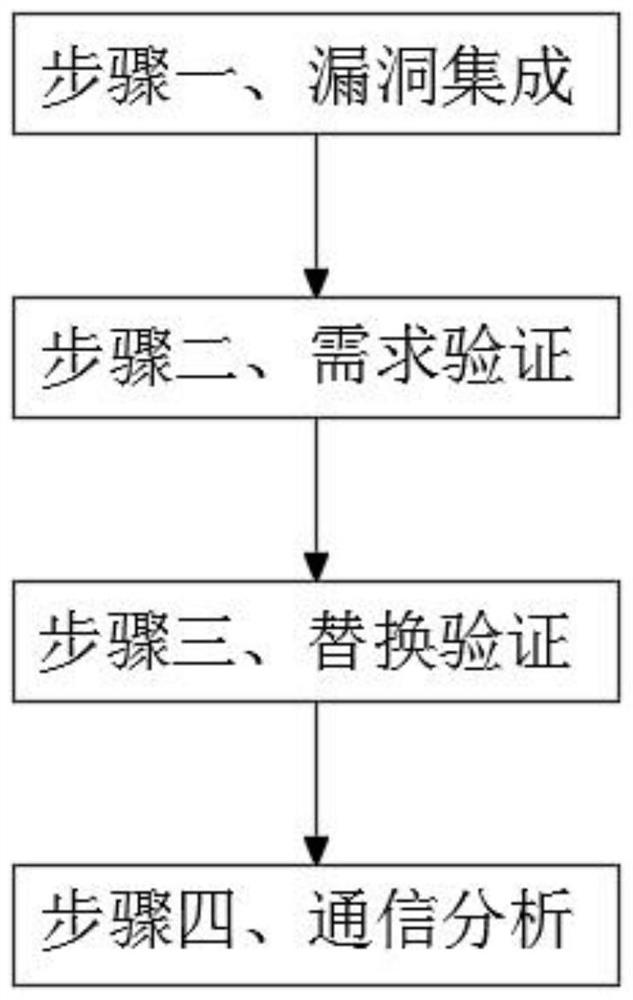
[0045] An automatic verification method for communication software security, which specifically includes the following steps:
[0046]Step 1. Vulnerability integration: Summarize and classify the currently discovered vulnerability principles and vulnerability patterns through the vulnerability integration unit 1, summarize and classify the patterns according to the frequency of security vulnerability patterns, and summarize the needs for judging various vulnerabilities. relevant information and discrimination mode;
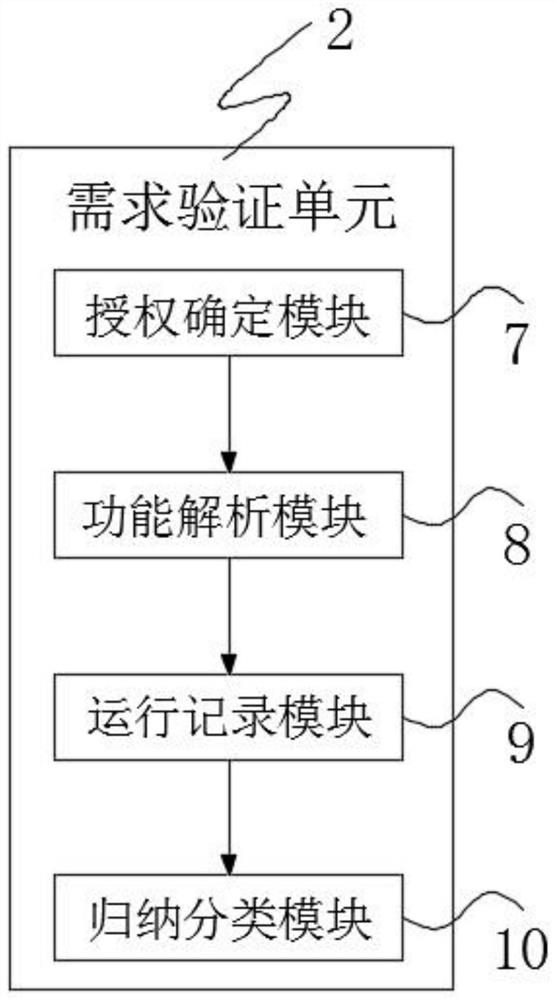
[0047] Step 2. Requirement verification: The required authority for the operation of the communication software is displayed to the user through the requirement verification unit 2, and the authority determined by the user to grant the communication software is recorded as a comparison standard, and the authority after the authorization of the user is analyzed. The user displays it in detail, and at the same time records the transmission data during the operation ...
Embodiment 2
[0051] The present embodiment is an improvement of the first embodiment, an automatic verification method for the security of communication software, which specifically includes the following steps:
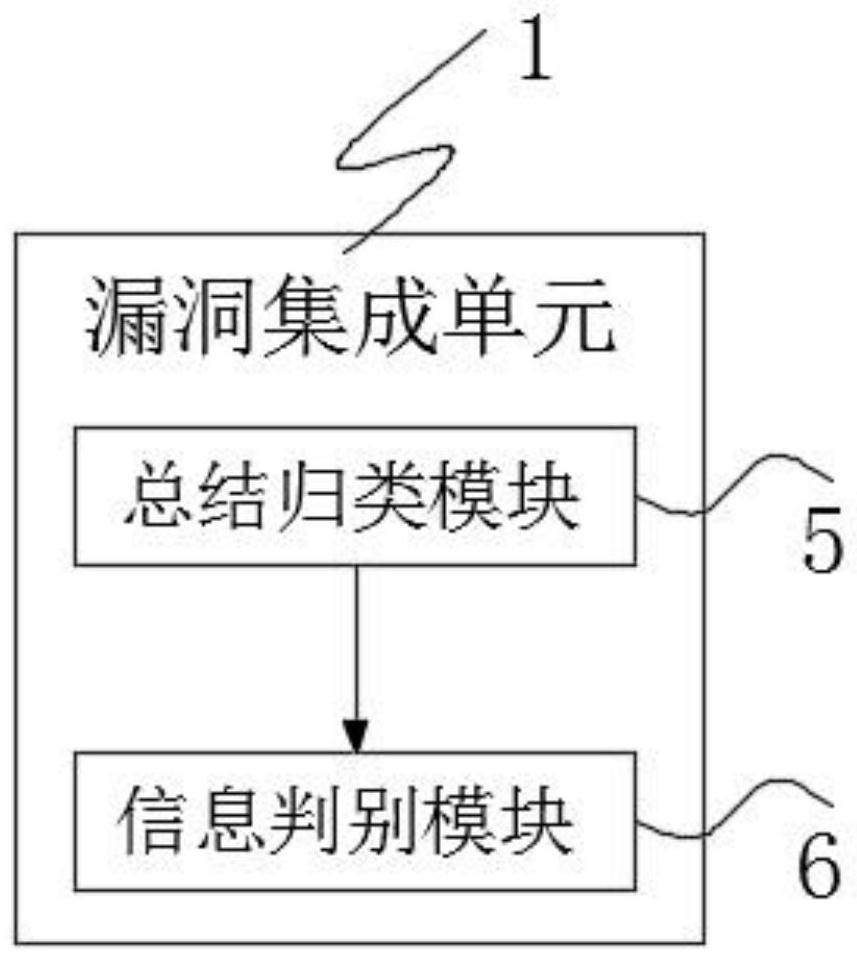
[0052] Step 1. Vulnerability integration: Summarize and classify the currently discovered vulnerability principles and vulnerability patterns through the vulnerability integration unit 1, summarize and classify the patterns according to the frequency of security vulnerability patterns, and summarize the needs for judging various vulnerabilities. The relevant information and discrimination mode of the figure 2 As shown, the vulnerability integration unit 1 includes a summary and classification module 5 and an information identification module 6. The summary and classification module 5 is connected with the information identification module 6. The summary and classification module 5 is used for the current discovered vulnerability principles and vulnerability patterns. Summarize a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com