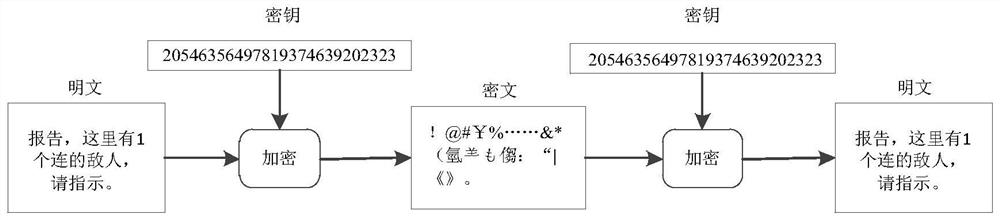
Key synchronization method and system
A key synchronization and time synchronization technology, applied in the field of communication, can solve the problems of increasing the encryption and decryption process, increasing risks, etc., to achieve the effect of resisting interception and decoding, efficient and correct encryption and decryption operations, and efficient transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
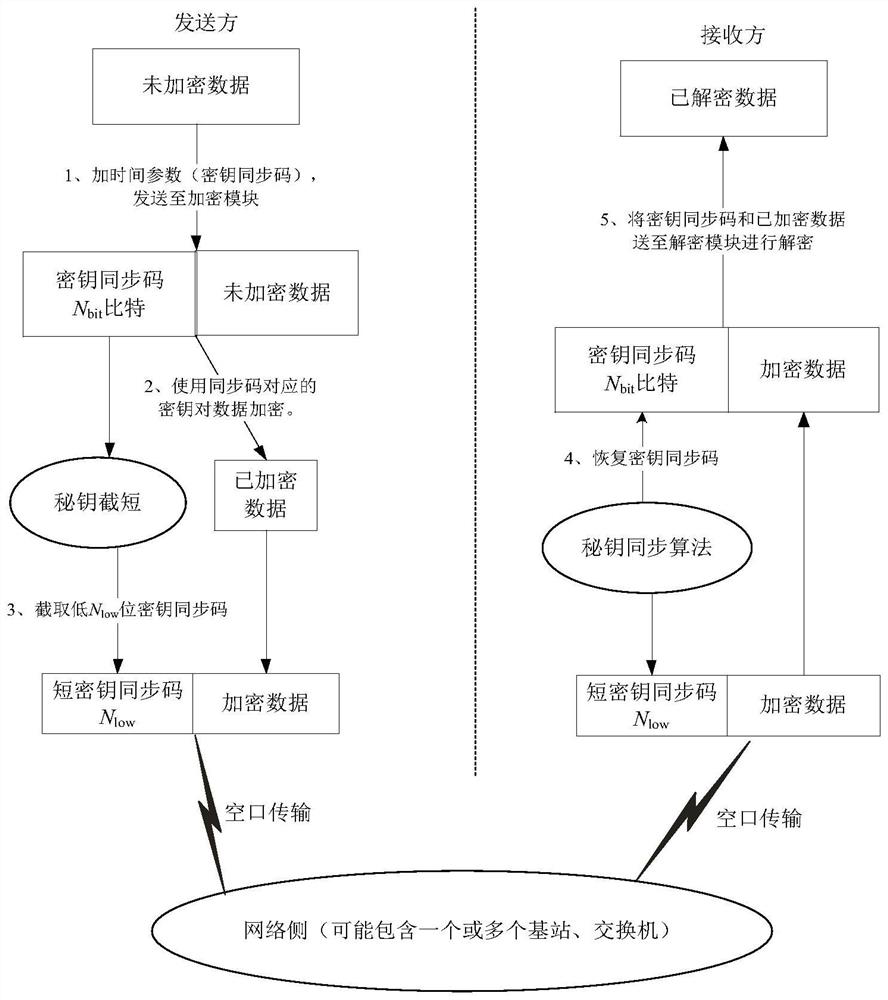
[0062] like image 3 As shown, a key synchronization method, the method includes the following steps:
[0063] S1: The sender reads the local time and adds N to the unencrypted data bit The bit time synchronization information is used as the key synchronization code, and forms a data frame with the unencrypted data;
[0064] S2: Encrypt the unencrypted data with the corresponding key according to the key synchronization code; bit Bit key synchronization code performs key interception operation; in a specific embodiment, described key interception operation refers to N bit bit key synchronization code truncating its N low Bit key synchronization code.
[0065] S3: The encrypted data and the truncated key synchronization code are formed into the air interface data of the sender;
[0066] S4: the receiver receives the air interface data, and uses the local time synchronization information to restore the truncated key synchronization code in the air interface data to the same...
Embodiment 2
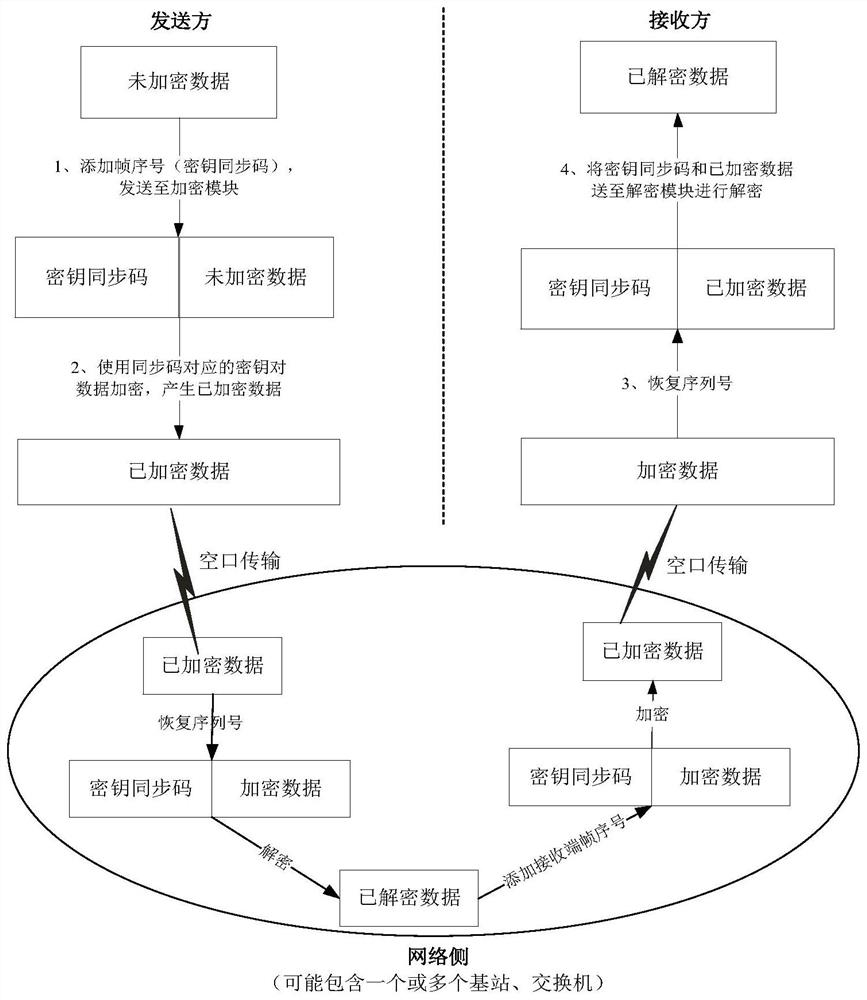
[0100] A system of key synchronization method, the sending end is used to add N in unencrypted data bit The bit time synchronization information is used as the key synchronization code, and forms a data frame with the unencrypted data; according to the key synchronization code, the encryption module uses the corresponding key to encrypt the unencrypted data; bit The key synchronization code of bits performs the key interception operation, and the encrypted data and the truncated key synchronization code are formed into the air interface data of the sender;
[0101] The receiving end uses the local time synchronization information to restore the truncated key synchronization code to the same complete key synchronization code as the sender; according to the key synchronization code algorithm, the decryption module uses the corresponding key to encrypt the encrypted data. data is decrypted. In a specific embodiment,
[0102] The encrypted data frame sent by the sender to the en...
Embodiment 3
[0120] A computer-readable storage medium on which a computer program is stored, and when the computer program is executed by a processor, the method steps implemented are as follows:
[0121] S1: Sender adds N to unencrypted data bit The bit time synchronization information is used as the key synchronization code, and forms a data frame with the unencrypted data;
[0122] S2: Encrypt unencrypted data according to the key synchronization code; bit The key synchronization code is used to perform the key interception operation;
[0123] S3: The encrypted data and the truncated key synchronization code are formed into the air interface data of the sender;
[0124] S4: the receiver receives the air interface data, and uses the local time synchronization information to restore the truncated key synchronization code in the air interface data to the same key synchronization code as the sender;
[0125] S5: The receiver decrypts the encrypted data according to the key synchronizati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com