Cisco IOS-XE-oriented Web command injection vulnerability detection method
A technology of command injection and vulnerability detection, which is applied in the field of vulnerability detection, can solve the problems of inapplicability of simulation, easy false positives, and low efficiency of vulnerability detection, and achieve the effect of improving code coverage, efficiency, and vulnerability detection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
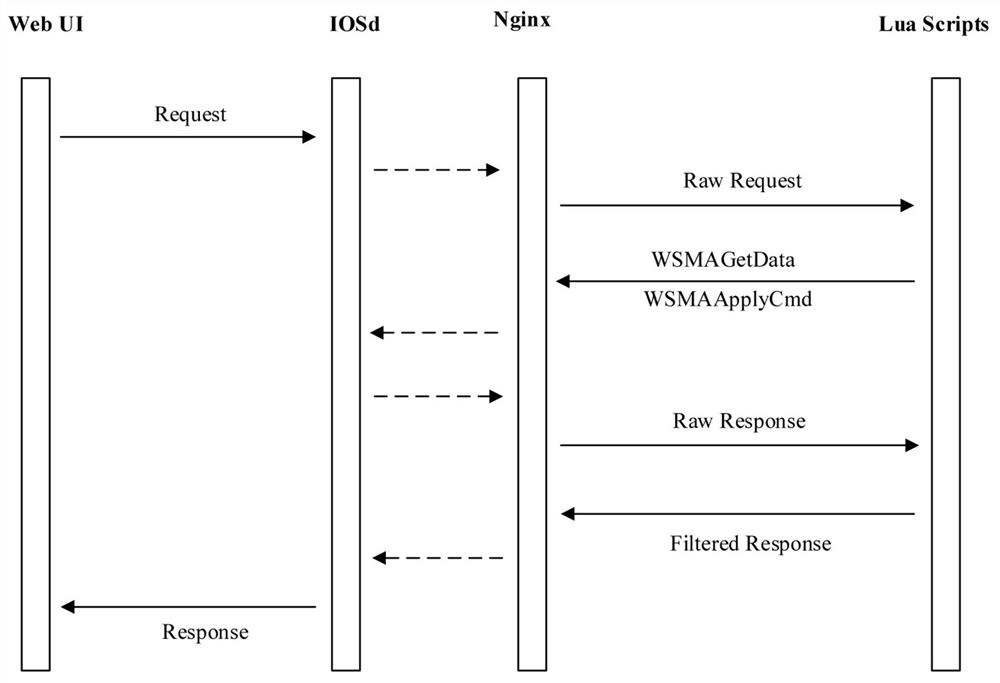
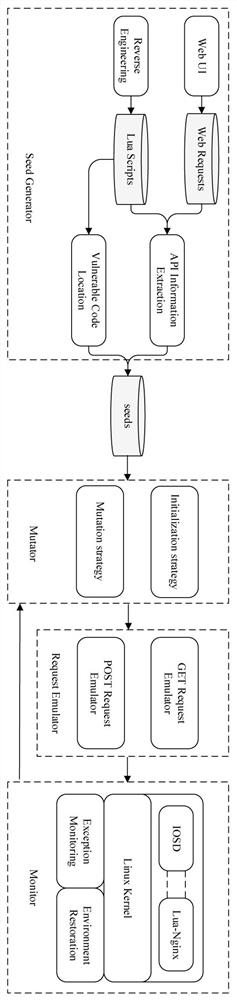
[0053] Embodiment 1: This embodiment provides a Cisco IOS-XE-oriented Web command injection vulnerability detection method. The method uses the fuzzing framework CRFuzzer for Cisco IOS-XE system Web management services to perform vulnerability detection. The CRFuzzer system structure is as follows: figure 2 shown. The method mainly includes the following:
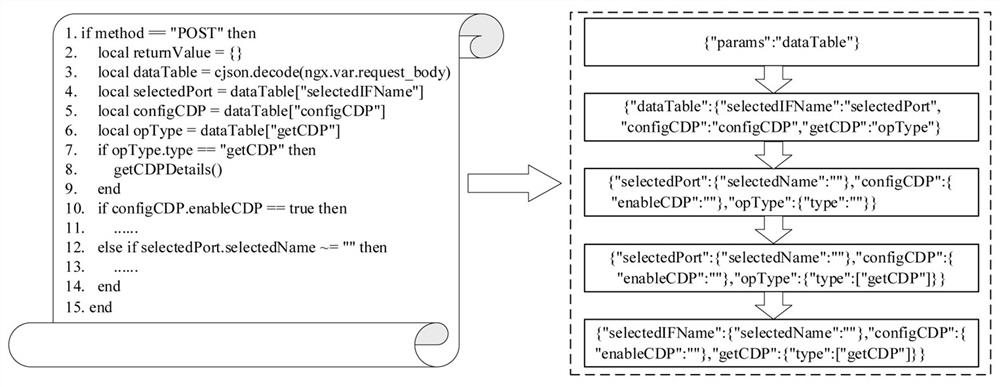
[0054] 1. Seed generation: extract API information from front-end web requests and back-end Lua programs, and combine command injection vulnerability features to find vulnerable code segments that may have vulnerabilities, and generate initial seeds for fuzz testing;
[0055] 1.1 API information extraction
[0056] (1) Extract the API from the front-end request:
[0057] Like some existing IoT fuzzing methods, CRFuzzer extracts API information from front-end requests. During the extraction process, CRFuzzer parses and stores the request header and parameter information. The URL in the header and its structure informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com