Network asset value evaluation method and system, medium, equipment and terminal
A network asset and value assessment technology, applied in the field of cyberspace security risk assessment, can solve problems such as not giving specific methods, not being able to distinguish value, not considering the importance of asset business, etc., to reduce deviation and reduce the influence of subjective factors Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
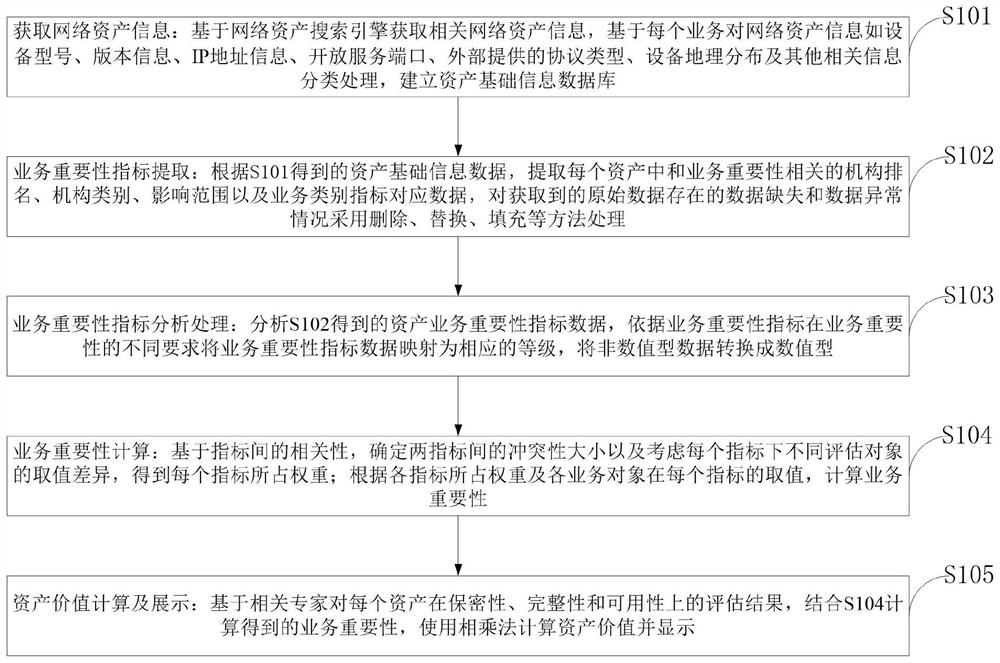
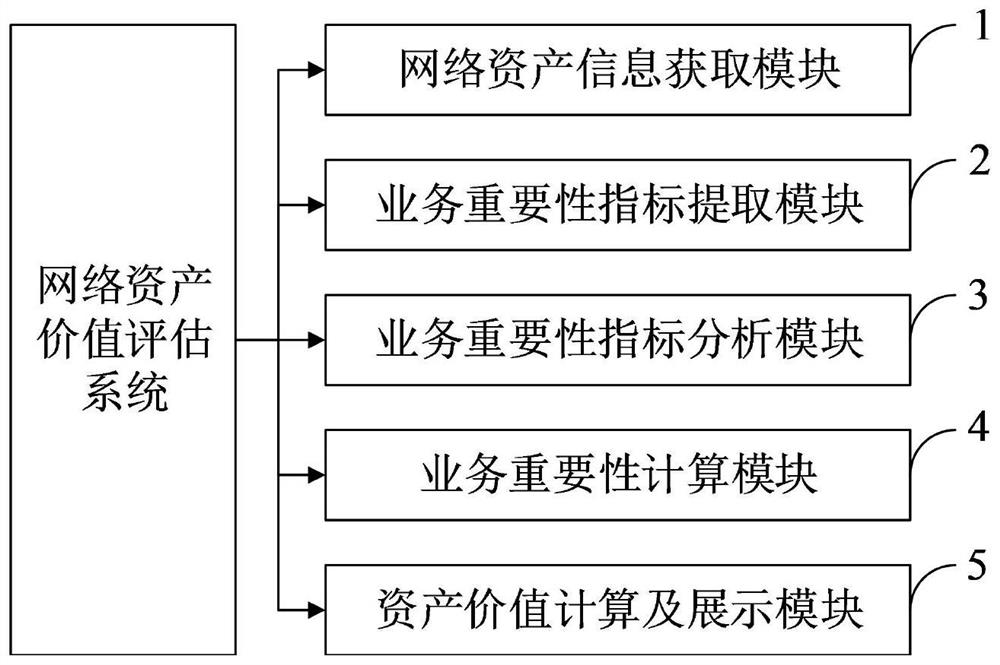
[0088] The purpose of the present invention is to provide a network asset value evaluation system and method, which can effectively meet the needs of risk evaluation and risk management. The network asset value evaluation system includes a network asset search engine, a business importance index extraction module, a business importance index analysis module, a business importance calculation module, and an asset value calculation and display module.
[0089] In order to achieve the above purpose, the method for evaluating the value of network assets provided by the present invention includes the following steps in order:
[0090] 1) The S1 stage of acquiring network asset information: based on the network asset search engine to obtain relevant network asset information, and based on each service, the network asset information such as device model, version information, IP address information, open service ports, externally provided protocol types, The geographical distribution ...
Embodiment 2
[0125] The network asset value evaluation system provided by the embodiment of the present invention includes a network asset search engine, a business importance index extraction module, a business importance index analysis module, a business importance calculation module, and an asset value calculation and display module.
[0126] The present invention will be further described in conjunction with an example of bank network asset value evaluation. The evaluation method based on the network asset value evaluation system provided by the embodiment of the present invention includes the following steps performed in order:
[0127] 1) The S1 stage of acquiring network asset information: based on the network asset search engine to obtain relevant network asset information, and based on each service, the network asset information such as device model, version information, IP address information, open service ports, externally provided protocol types, The geographical distribution of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com