Security chip communication method and device based on third-party key management node
A key management and security chip technology, applied in the field of security chip communication methods and devices, can solve problems such as easy cracking and data leakage, and achieve the effect of improving the difficulty of cracking and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
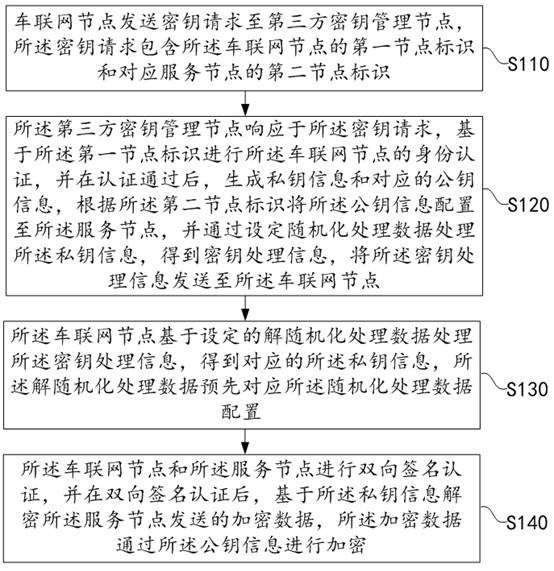
[0038] figure 1 A flowchart of a third-party key management node-based security chip communication method provided in Embodiment 1 of the present application is given. The third-party key management node-based security chip communication method provided in this embodiment can be used by the Internet of Vehicles. The business service system is executed, the car networking business service system can be implemented by means of software and / or hardware, and the car networking business service system can be composed of two or more physical entities.
[0039] The following description will be given by taking the Internet of Vehicles business service system as the subject of executing the third-party key management node-based security chip communication method as an example. refer to figure 1 , the security chip communication method based on the third-party key management node specifically includes:
[0040] S110. The IoV node sends a key request to a third-party key management no...
Embodiment 2
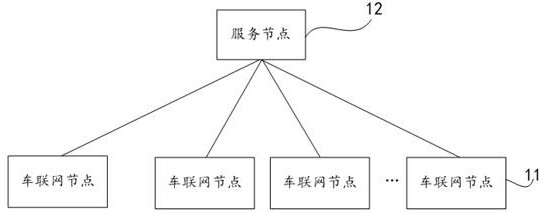
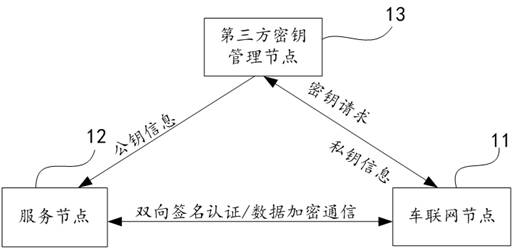
[0086] On the basis of the above-mentioned embodiment, Figure 5 This is a schematic structural diagram of a security chip communication device based on a third-party key management node provided in Embodiment 2 of the present application. refer to Figure 5 , the security chip communication device based on the third-party key management node provided by this embodiment specifically includes: a request module 21 , a configuration module 22 , a processing module 23 and a decryption module 24 .
[0087] The request module 21 is configured to send a key request to a third-party key management node through the IoV node, where the key request includes the first node identifier of the IoV node and the second node identifier of the corresponding service node;
[0088] The configuration module 22 is configured to respond to the key request through the third-party key management node, perform identity authentication of the IoV node based on the first node identifier, and generate priv...
Embodiment 3
[0097] The third embodiment of the present application provides an electronic device, refer to Image 6 , the electronic device includes: a processor 31 , a memory 32 , a communication module 33 , an input device 34 and an output device 35 . The number of processors in the electronic device may be one or more, and the number of memories in the electronic device may be one or more. The processor, memory, communication module, input device, and output device of the electronic device may be connected by a bus or in other ways.
[0098] The memory 32, as a computer-readable storage medium, can be used to store software programs, computer-executable programs and modules, such as program instructions / Modules (eg, a request module, a configuration module, a processing module, and a decryption module in a third-party key management node-based secure chip communication device). The memory may mainly include a storage program area and a storage data area, wherein the storage program ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com