Vulnerable watermark method for protecting electronic signet
A technology of electronic seals and fragile watermarks, applied in electrical components, image communications, encoding/decoding devices, etc., can solve problems such as embedding formulas and tampering with classification rules without success, and achieve the effect of ensuring integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
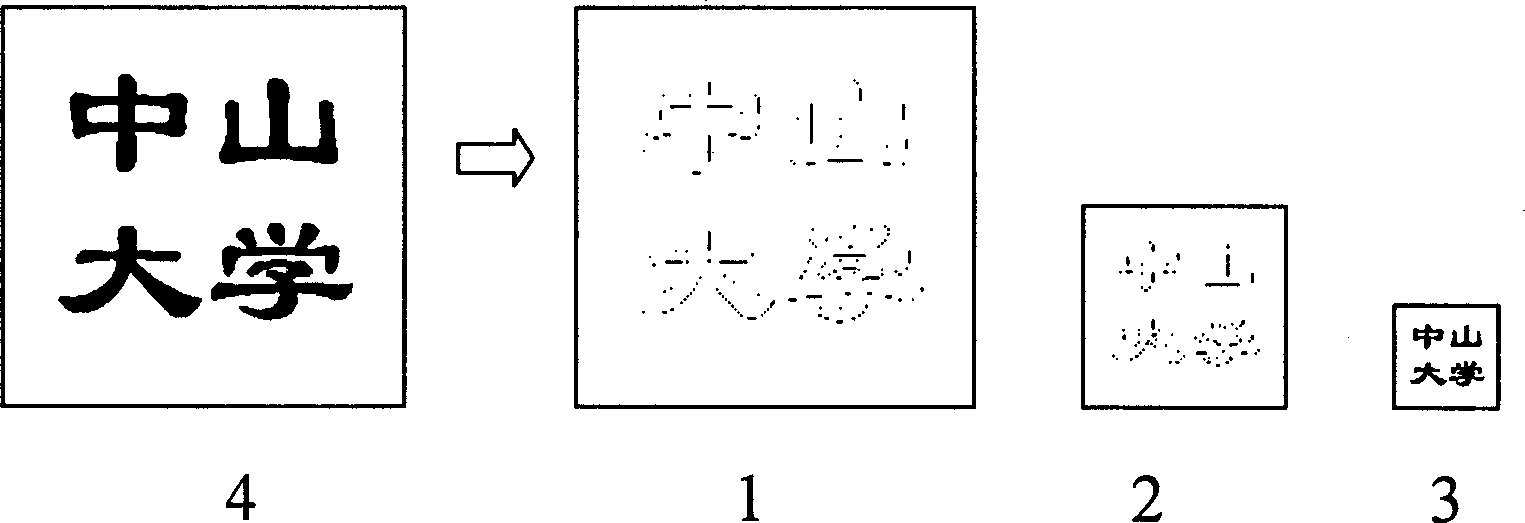
[0064] figure 1 Among them, the original watermark 4 is a binary image, which is divided into three levels of 1, 2, and 3 after the resolution decreasing operation.
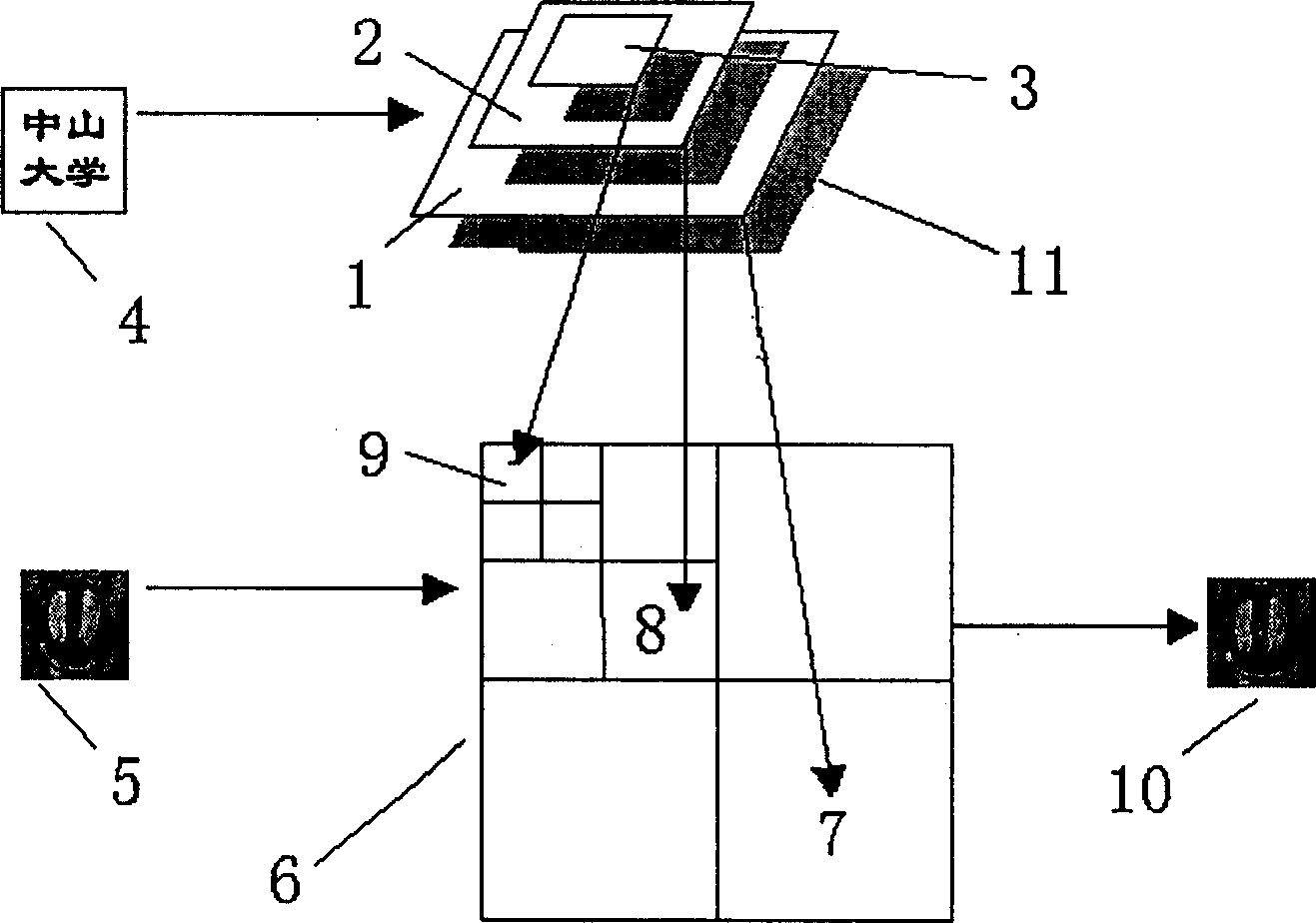
[0065] figure 2 Example for watermark embedding. figure 2 Among them, the original watermark 4 is a binary image, which is divided into three levels 1, 2, and 3 of the watermark pyramid 11 after the resolution decreasing operation; the original image 5 is a grayscale image, and the wavelet coefficient 6 is decomposed by the three-level wavelet, according to In the aforementioned embedding scheme, one layer of the watermark pyramid 11 is embedded in the diagonal direction of the first-level wavelet decomposition (HH 1 subband) coefficient 7, embedding 2 layers of the watermark pyramid 11 in the diagonal direction of the second wavelet decomposition (HH 2 subband) coefficient 8, embedding the 3 layers of the watermark pyramid 11 into the low frequency (LL 3 Subband) coefficient 9, after the embedding is compl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com