Safety storage application
A storage device and security data technology, applied in computer security devices, preventing unauthorized use of memory, instruments, etc., can solve the problems of enterprises’ hesitation in using storage applications, and achieve the effect of protecting privacy and integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
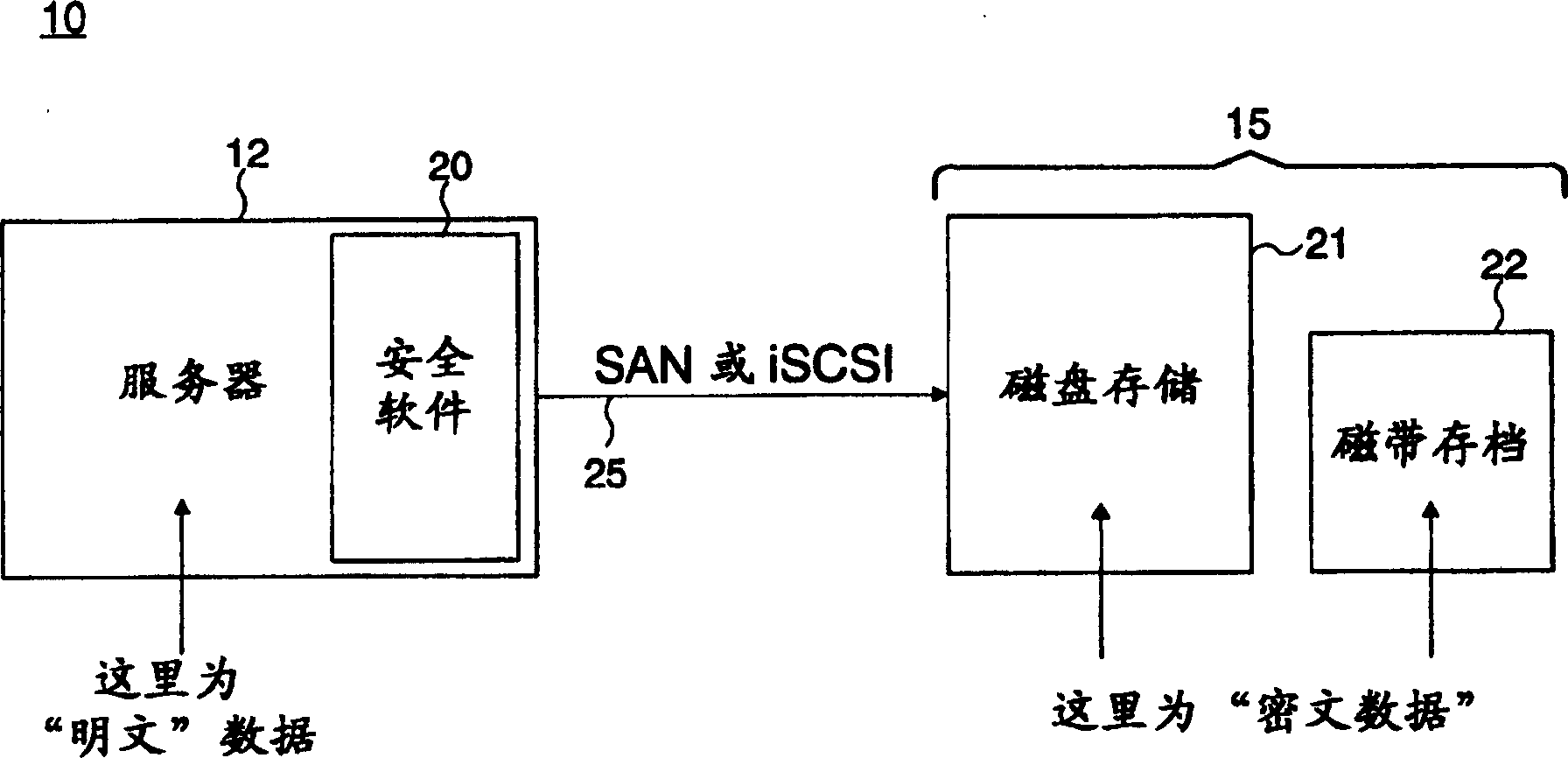
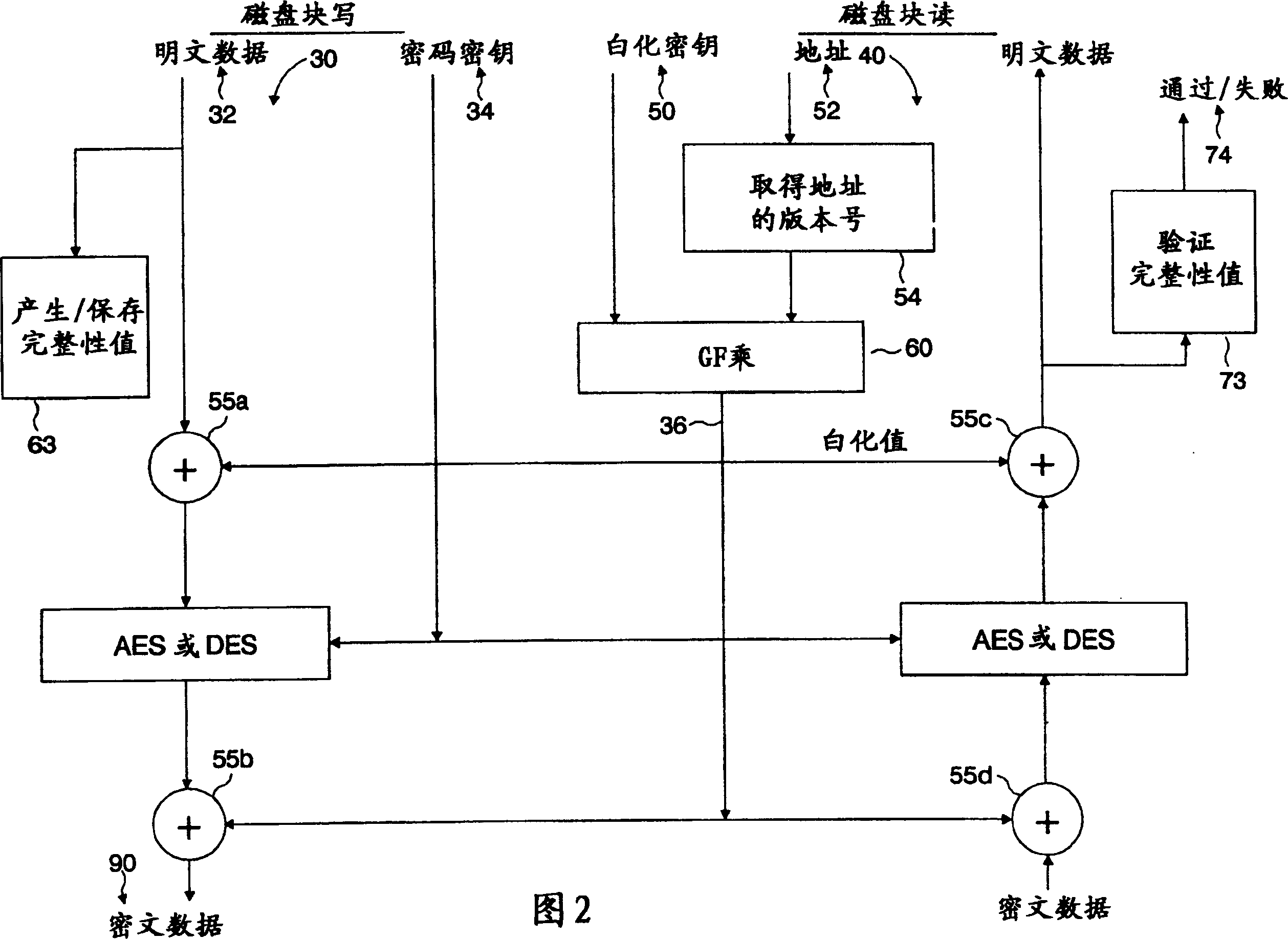
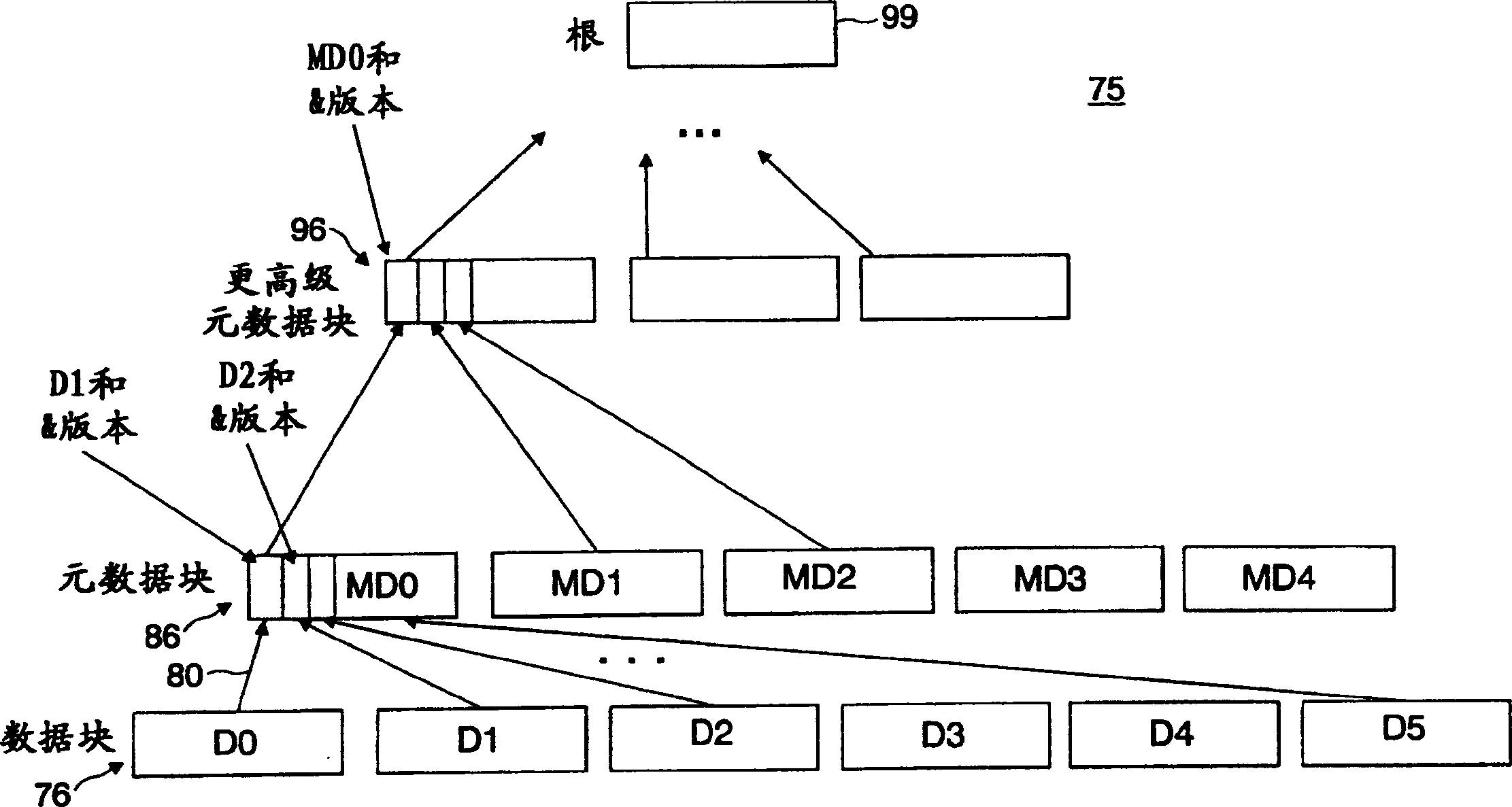
[0015] figure 1 A secure storage area network system 10 implementing the storage application of the present invention is shown. like figure 1 As shown, the data sources providing the plaintext data to be stored in the storage application 15 (implementing storage media, eg disk 21 and tape 22 ) are located eg in the server device 12 . It will be appreciated that other non-volatile types of storage media may be implemented, such as optical disks, magnetic disks, compacts, flash drives, etc., as well as volatile storage media. The data blocks to be written out to the storage application are encrypted according to the processing provided by the security software program 20 , which is executed on the server device 12 in order to generate the ciphertext stored in the storage application 15 . In one embodiment, server device 12 provides a network interface to operate on server device 12 according to a storage area network communication standard, such as Fiber Channel or iSCSI, over...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com