Cryptographic method for mobile phone communication
A technology of mobile phone and security method, which is applied in the directions of electrical components, wireless communication, security communication devices, etc., can solve the problems of wasting time, forgetting to encrypt data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
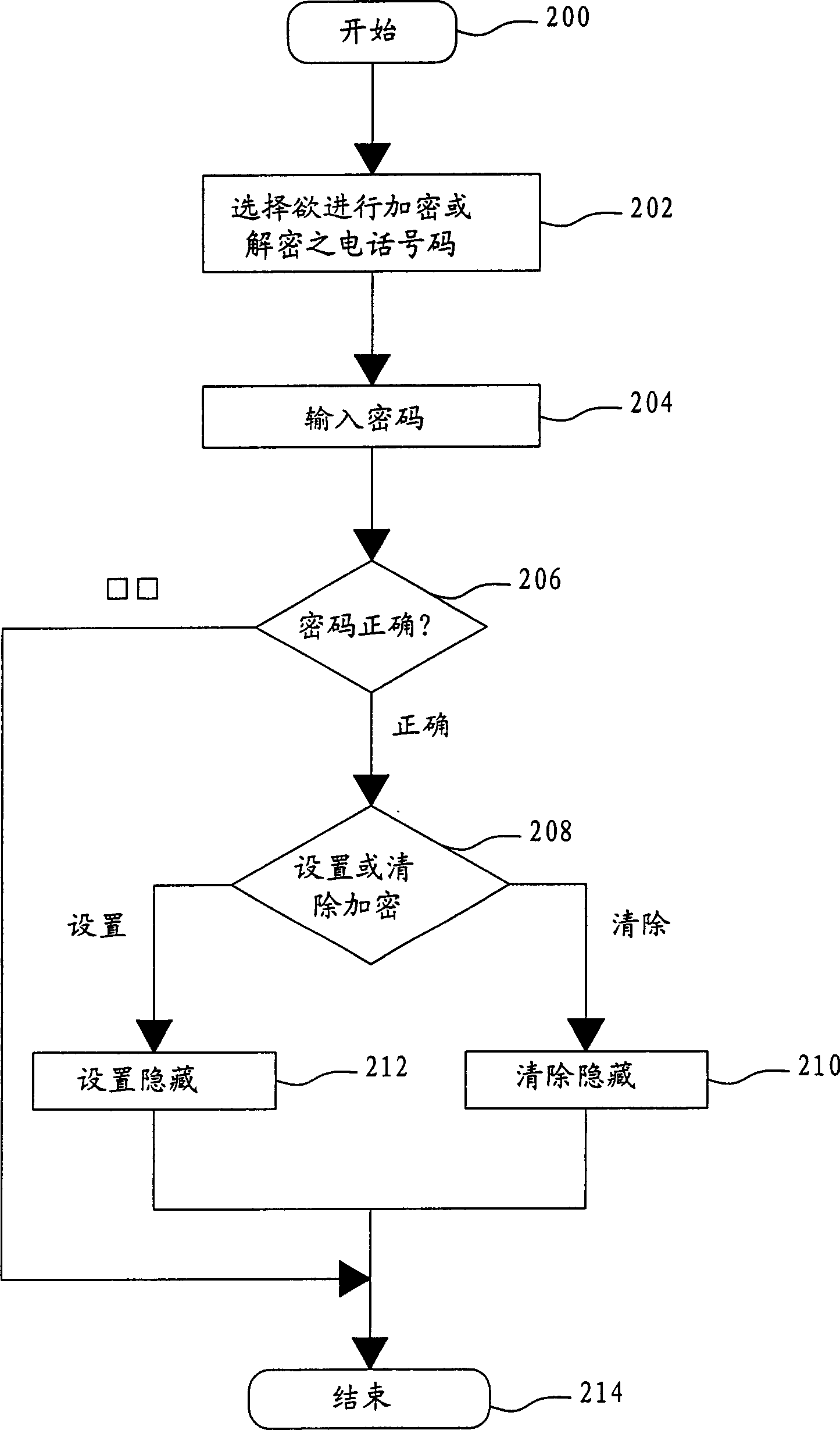
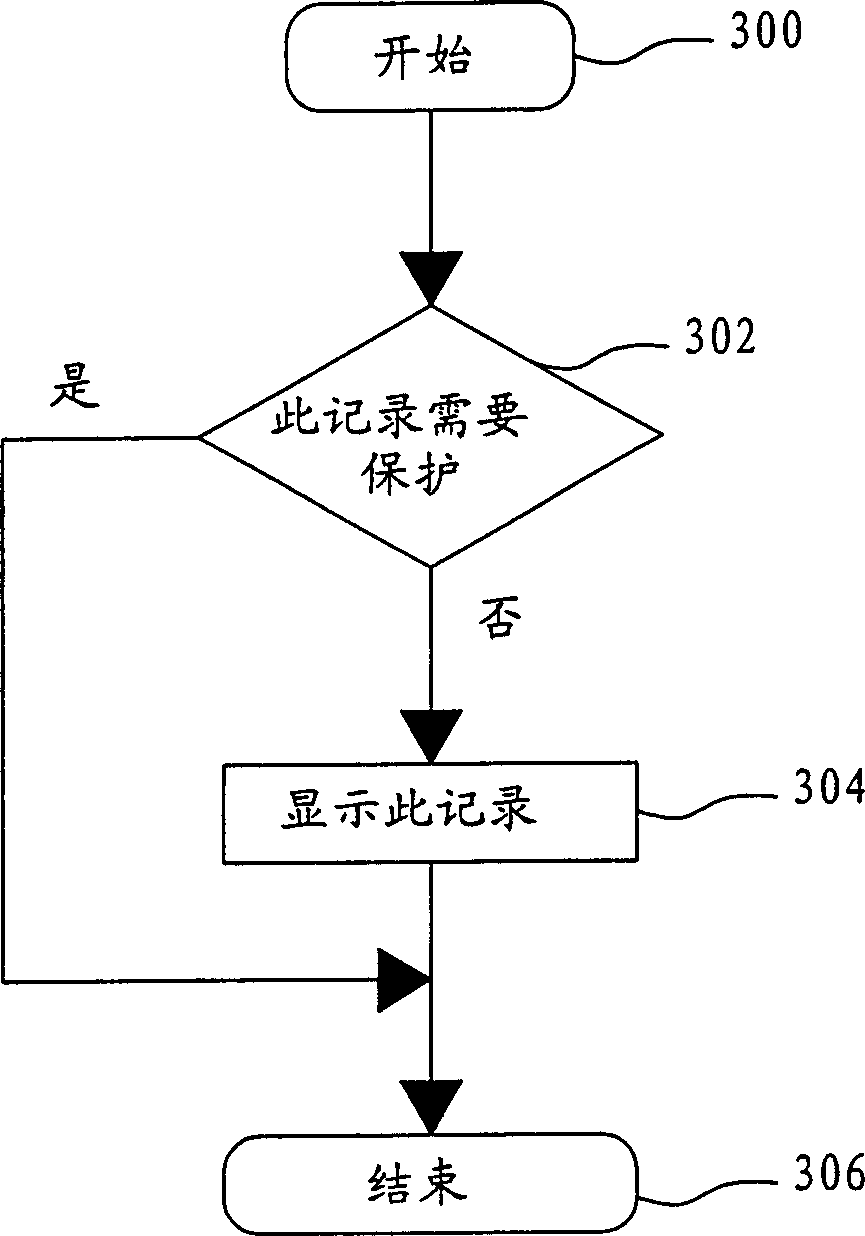
[0014] Without limiting the spirit and scope of application of the present invention, the implementation of the present invention is described below with an embodiment; those who are familiar with the technical field, after understanding the spirit of the present invention, can apply the encryption method of the present invention to each different mobile phones. The encryption method according to the present invention does not need to encrypt each piece of data, but can encrypt and protect the data related to this subject at the same time for a specific subject, which can not only increase efficiency, but also avoid failure to perform due to human negligence. Encryption, while leaking data. The encryption method of the present invention can be used in various mobile communication tools and is not limited to the preferred embodiments described below.
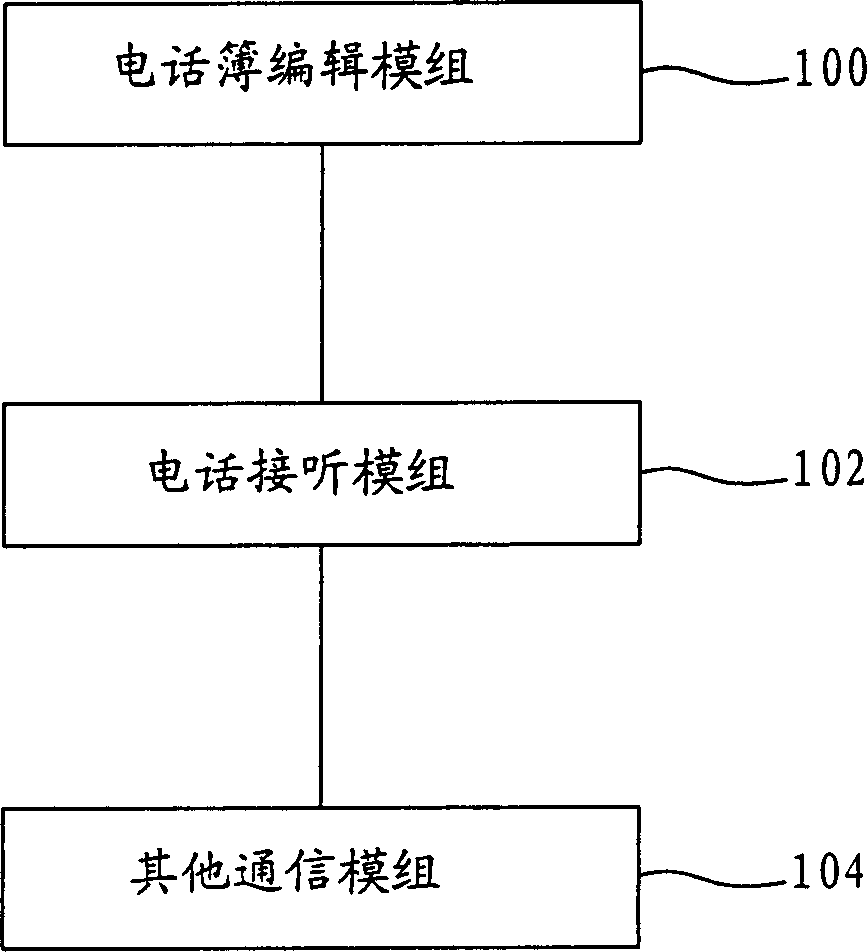
[0015] first reference figure 1 Shown is a schematic diagram of related modules used for encryption in the mobile phone, incl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com