Safety management method of network comprehensive switch on equipment
A technology for access equipment and security management, applied in data exchange networks, user identity/authority verification, digital transmission systems, etc., can solve problems such as cost accounting, soft switch equipment attacks, and inability to manage IAD uniformly, and achieve management efficiency High, security assurance, the effect of preventing illegal and counterfeit equipment from accessing the network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
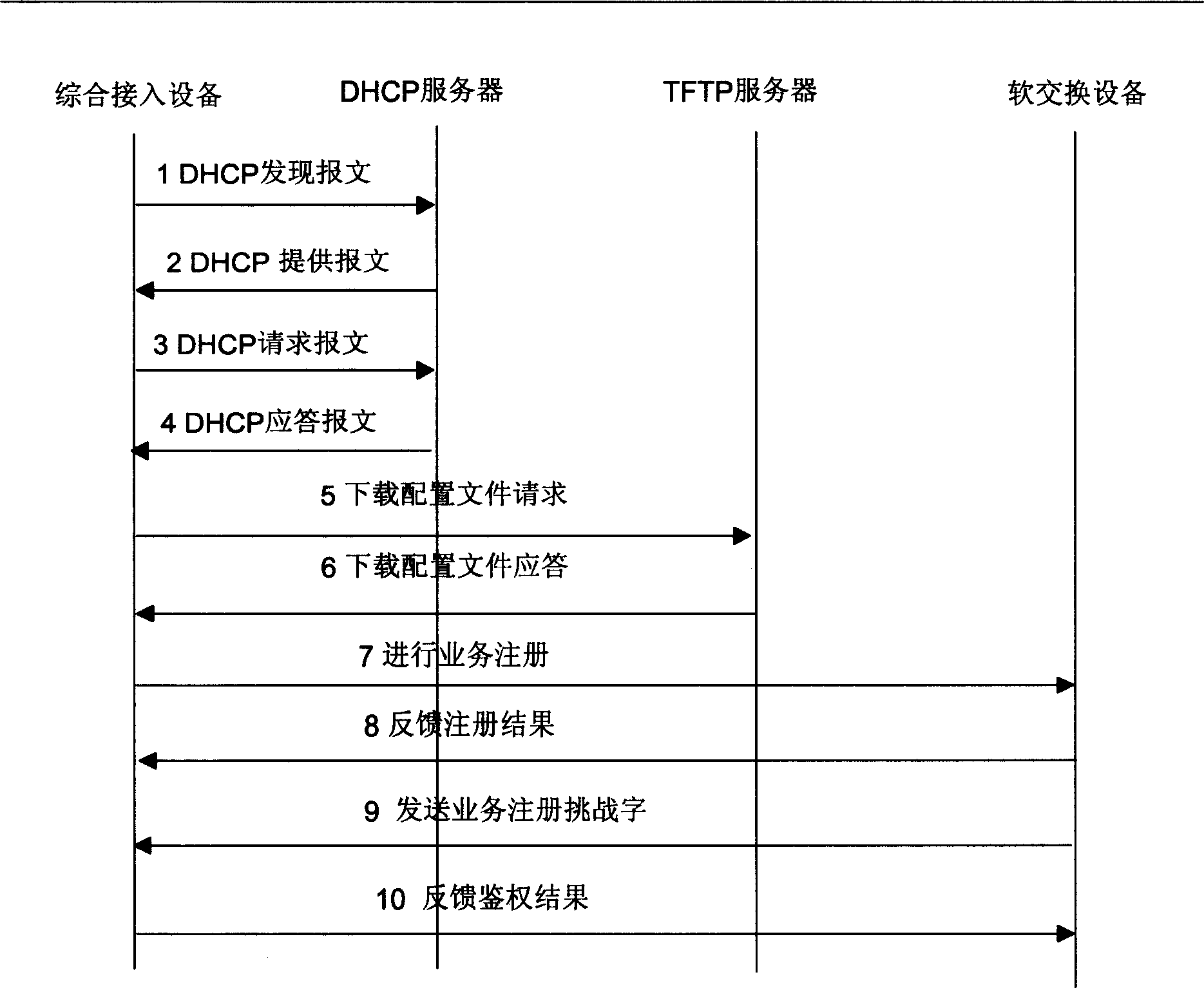
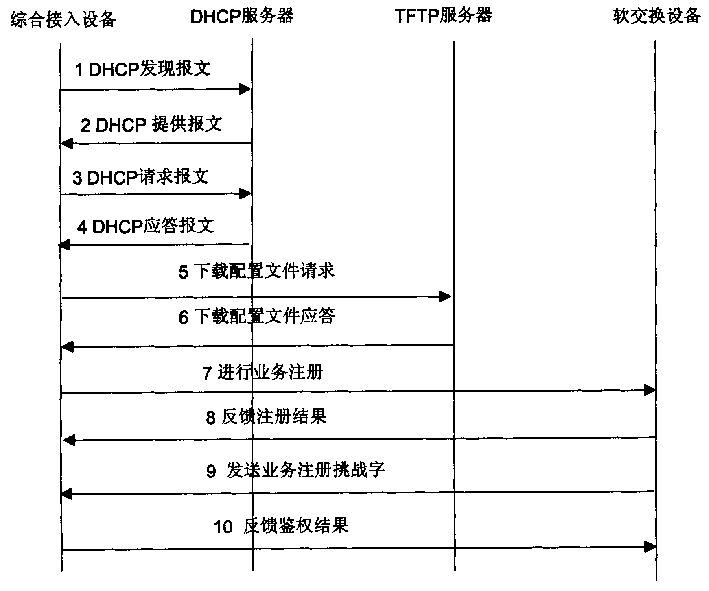
[0017] In the current network structure, the management of the IAD is implemented by the IADMS, and the SoffSwitch completes the security authentication and service control of the IAD. The IAD can manage the IAD only after completing the management registration with the IADMS and the service registration with the SoftSwitch respectively.
[0018] An example of a specific IAD security management method provided by the present invention includes the following processes:
[0019] 1. Account opening process: Before using the IAD, the user must open an account with the operator, and write the necessary information such as the device identification code in the IAD as the basis for realizing security management;
[0020] 2. Service registration process: After IAD completes the management registration, it registers the service with SoftSwitch, and the service can be used after the verification is passed;
[0021] 3. Periodic authentication process: During the normal use of services b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com