Method for making message flow limitation by adopting token leakage cylinder
A leaky bucket and packet technology, applied in the field of packet current limiting based on token leaky buckets, can solve problems such as low efficiency, save system resources, improve efficiency, and reduce operating load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
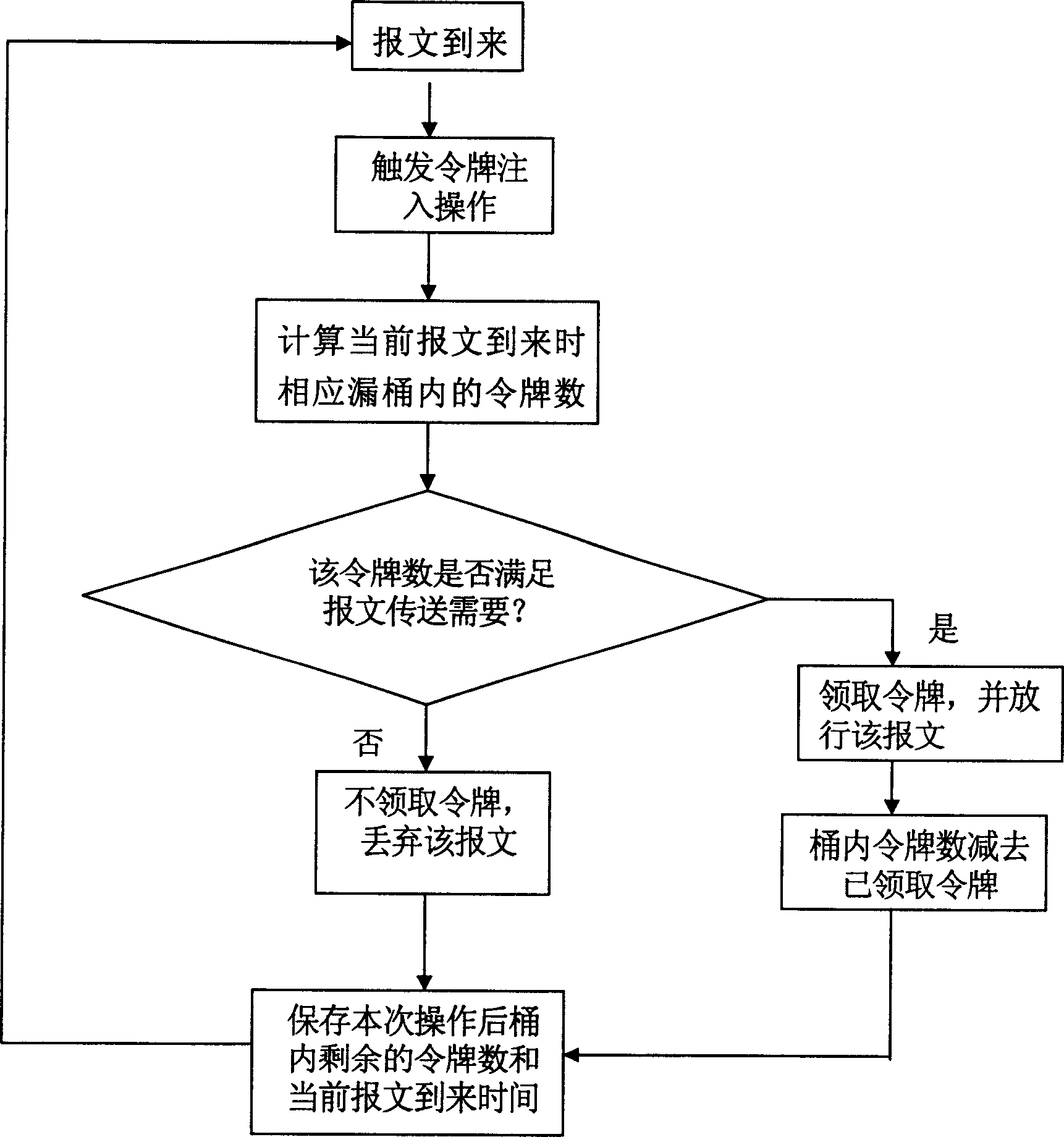
[0015] refer to figure 2 A preferred implementation of the packet current limiting method of the present invention is described.
[0016] In this embodiment, the present invention, as mentioned above, uses a new trigger mechanism for injecting tokens in order to prevent the network processor from using timed interrupts to inject tokens, that is, the arrival of a message is used as a trigger to inject token. This scheme will be described in detail below.
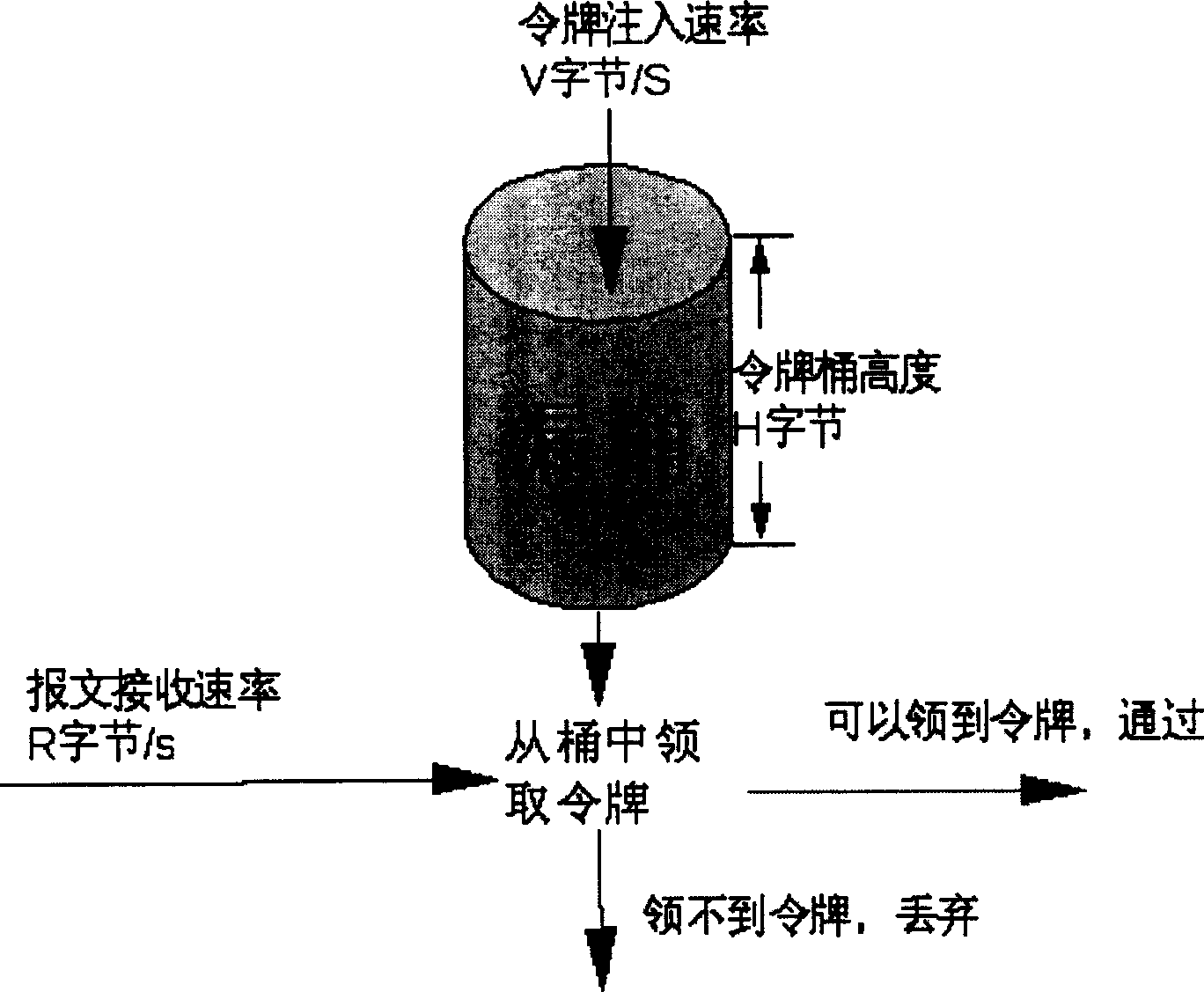
[0017] Let the arrival time of a certain message be Tn, and the time difference between this message and the previous message is set as dT. Then, when the message arrives, the operation of injecting tokens into the bucket is triggered, and the number of tokens injected into the bucket within the time interval dT is calculated. Then, it is judged whether the number of tokens that can be claimed from the bucket is greater than or equal to the number of tokens required by the message length. If the number of tokens in the b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com