Method of rejecting service attuck by resisting radio transmission layer safety protocol
A denial of service attack, security protocol technology, applied in the field of intelligent information processing, can solve the problems of consuming memory resources, exhausting server computing resources, consuming computing resources, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
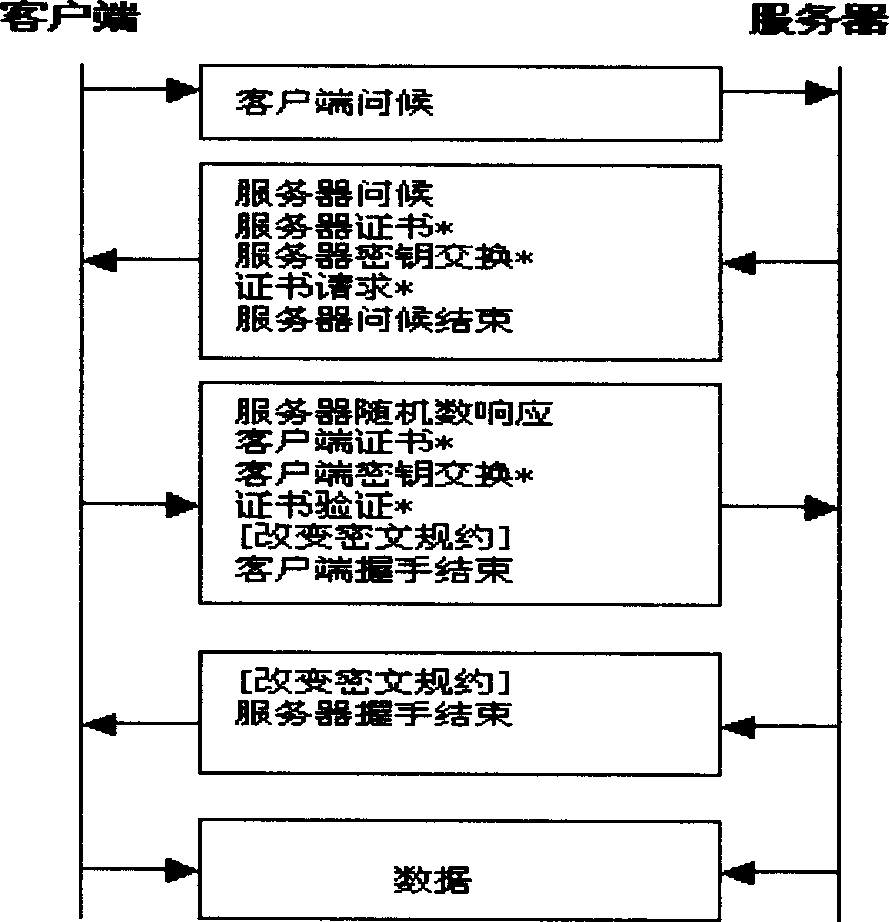
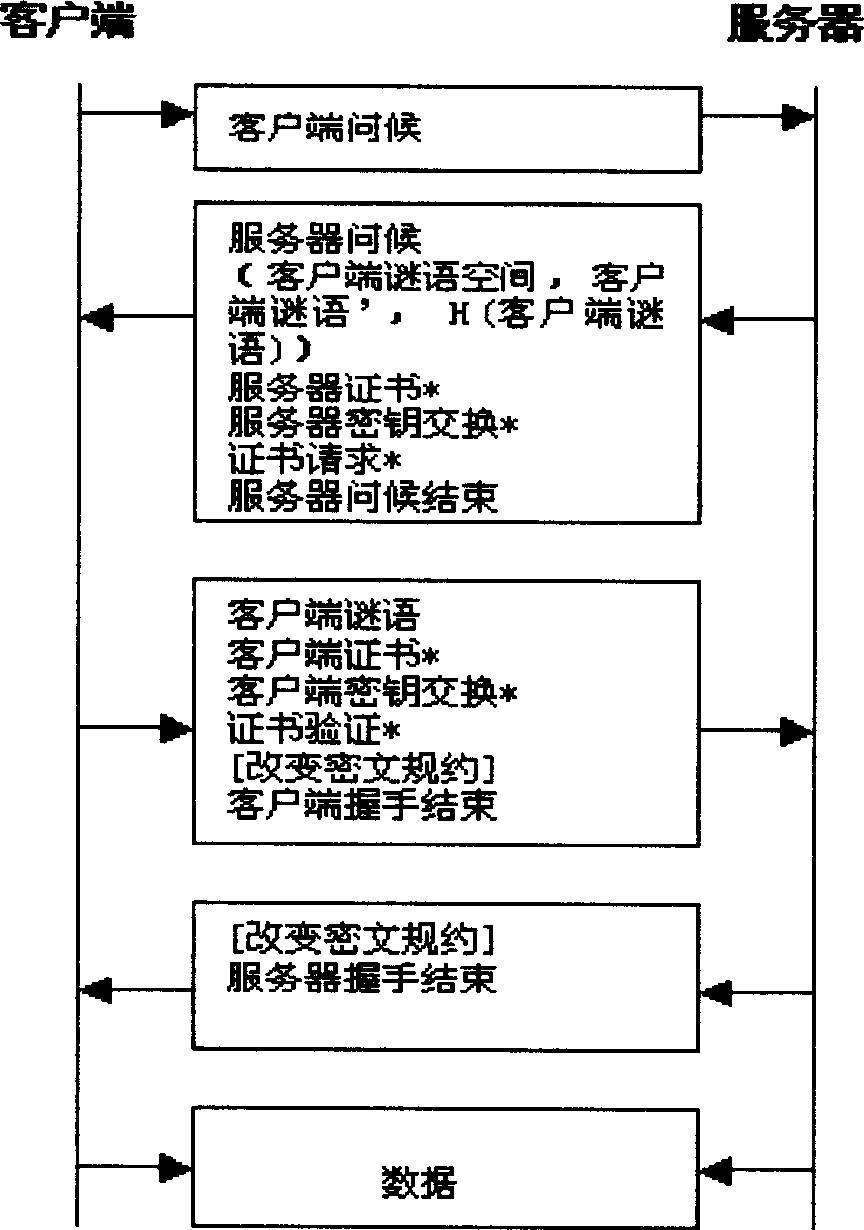
[0024] When the client sends a client greeting message and requests to establish a secure connection with the server, the server first checks whether the number of secure connections established by the IP address of the client has exceeded the specified quota according to the access control mechanism. If it has exceeded the quota, Then reject the client's secure connection request, otherwise, send a server greeting message, and check the number of exponent operations and the number of wrong exponent operations per unit time of the IP address of the client. According to these two values, it is decided to use figure 1 handshake is still figure 2 The handshake method, if using figure 2 The size of the corresponding client riddle space k can be determined according to the above two values. if used figure 1 When sending the server hello message, the server will also send the server certificate*, server key exchange*, certificate request*, server hello end message (messages with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com