Terminal to terminal encryption method of cell phone voice and data
An encryption method and voice technology, applied in the usage of multiple keys/algorithms, secure communication, near-field transmission system using transceivers, etc., can solve problems such as insecurity, achieve good security, and reduce development and production costs , the effect of good marketing value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
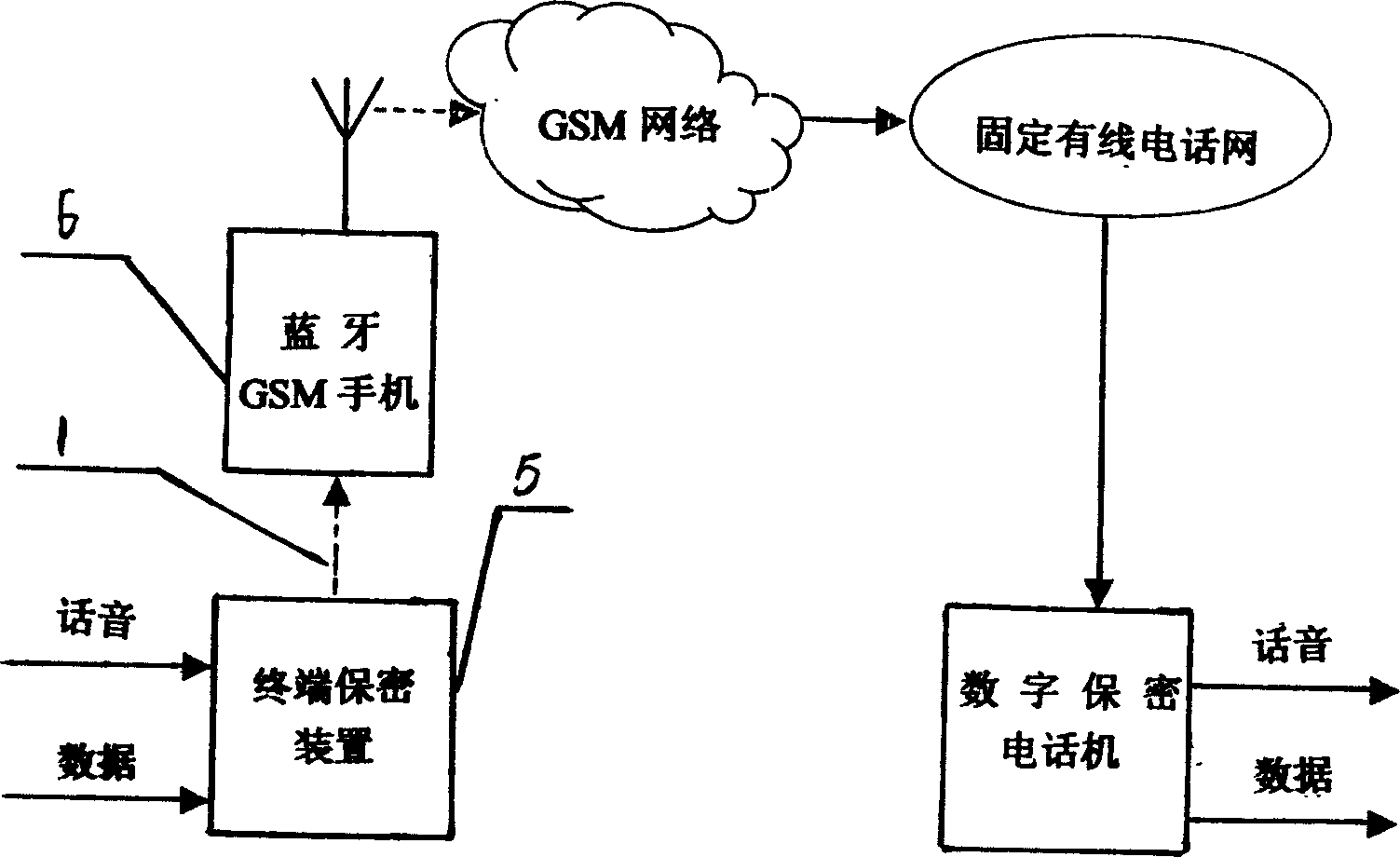
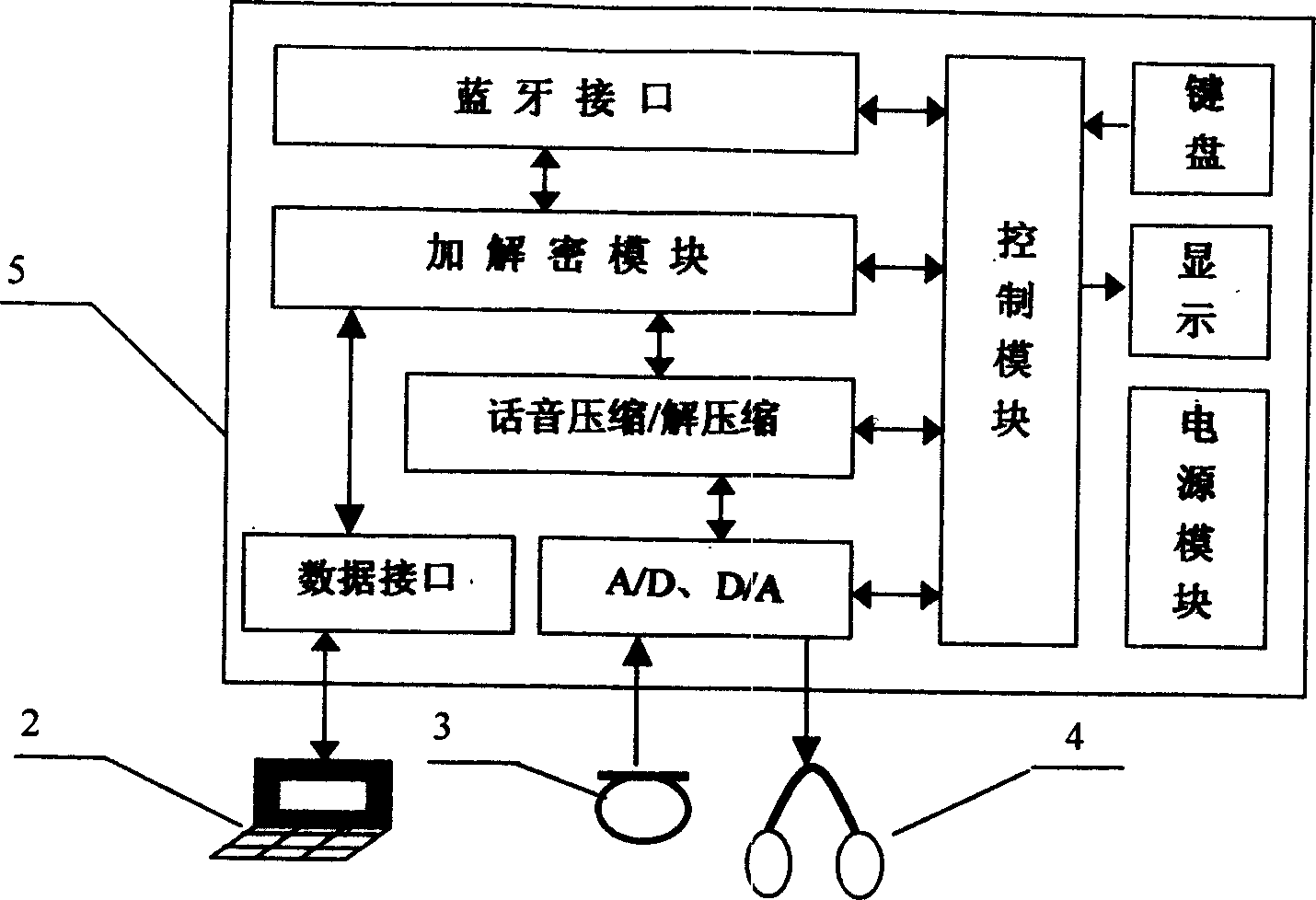
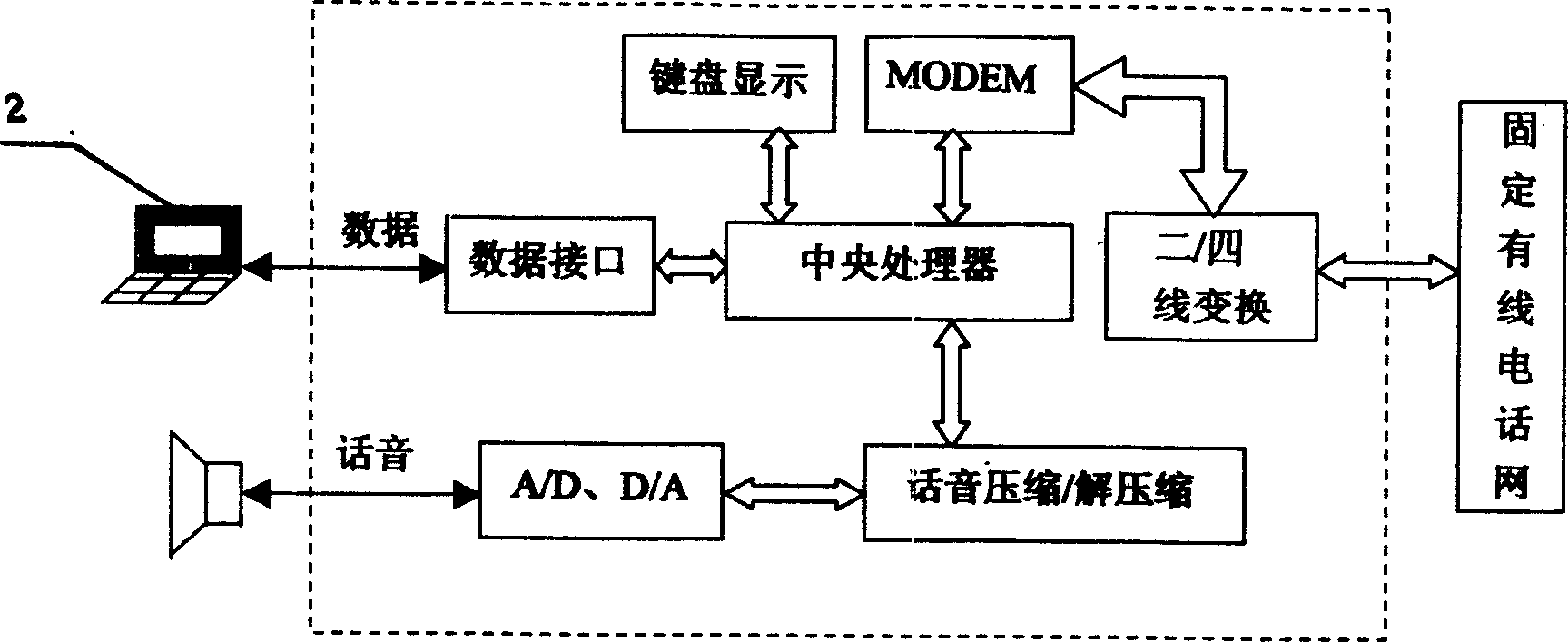
[0037] The terminal security device of the present invention is at least composed of a Bluetooth interface module, an encryption and decryption module, a voice compression / decompression module, A / D, D / A modules, a data interface module and a control module, and is characterized in that: the Bluetooth interface module Complete the wireless connection between the terminal security device and the Bluetooth mobile station; the encryption and decryption module is connected with the voice compression / decompression module, the Bluetooth interface module, and the data interface module respectively to complete the encryption / decryption processing of voice and data signals; A / D, D The / A module is connected with the voice compression / decompression module to complete voice analog / digital, digital / analog conversion and compression / decompression processing; the data interface module completes the connection between the terminal security device and the data terminal; the control module and th...
Embodiment 2
[0041] The composition and function of each component of terminal security device 5 are further described below:
[0042] The A / D and D / A modules are implemented by a single-chip integrated circuit integrating A / D, D / A conversion and voice codec functions, so as to reduce the size of the printed board and the overall volume of the terminal security device 5 . The A / D and D / A modules complete the A / D conversion and voice coding functions of the analog voice signal picked up by the microphone 3 at the sending end, and complete the voice decoding and D / A conversion functions at the receiving end, and convert the restored analog voice signal Give the headset 4.
[0043] The data interface module adopts TTL level and RS232 level conversion integrated circuit to realize. The data interface module completes the signal level conversion (from RS232 level to TTL level) from the data terminal 2 to the internal encryption and decryption module of the terminal security device 5 at the sen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com