Hand disk locking and de-locking control scheme based on USB key apparatus
A key device and control scheme technology, applied in the direction of instruments, electrical digital data processing, digital data processing components, etc., can solve the problems of low feasibility, trouble, slow operation speed, etc., and achieve the effect of solving huge workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the accompanying drawings and specific implementation.
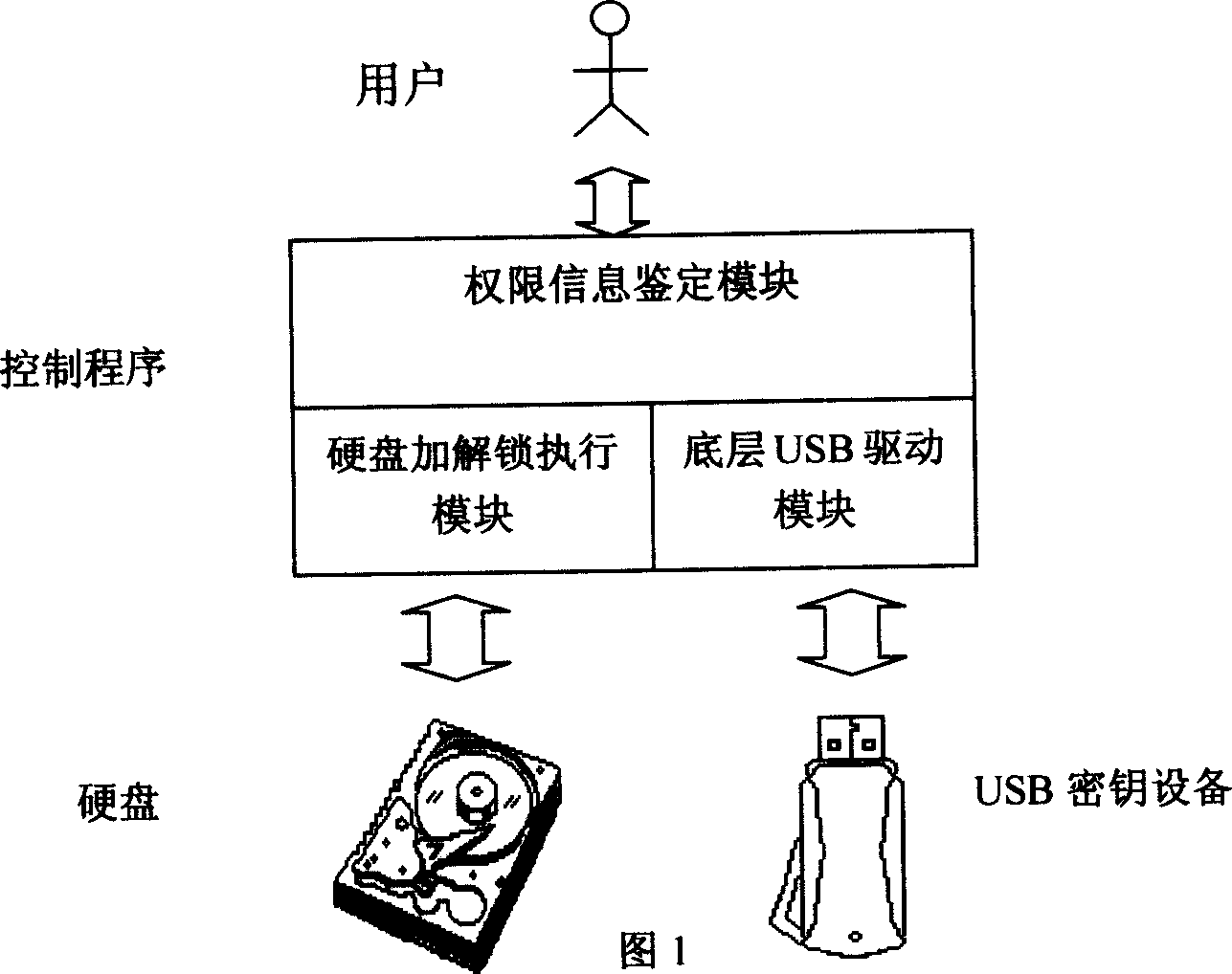
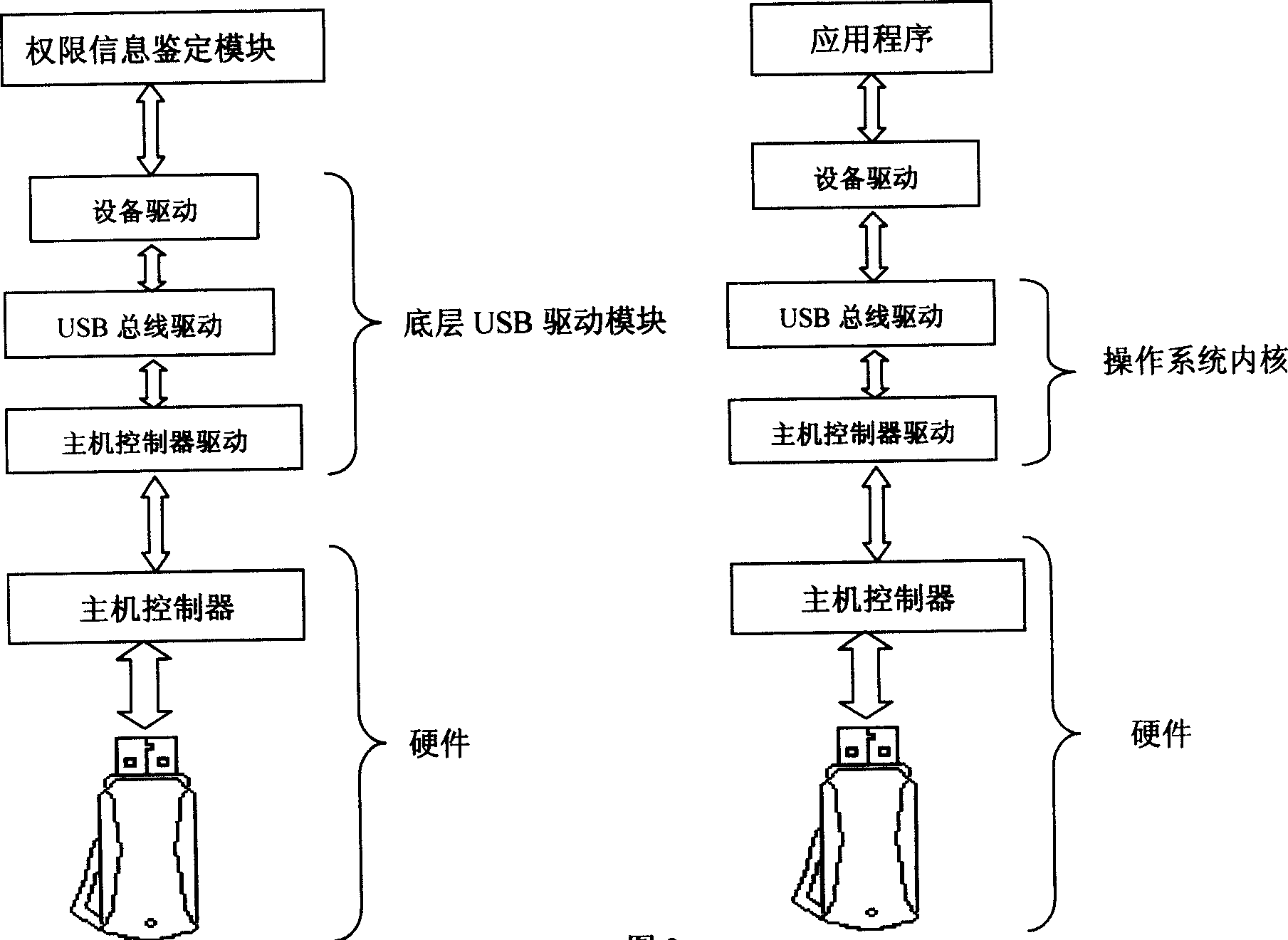
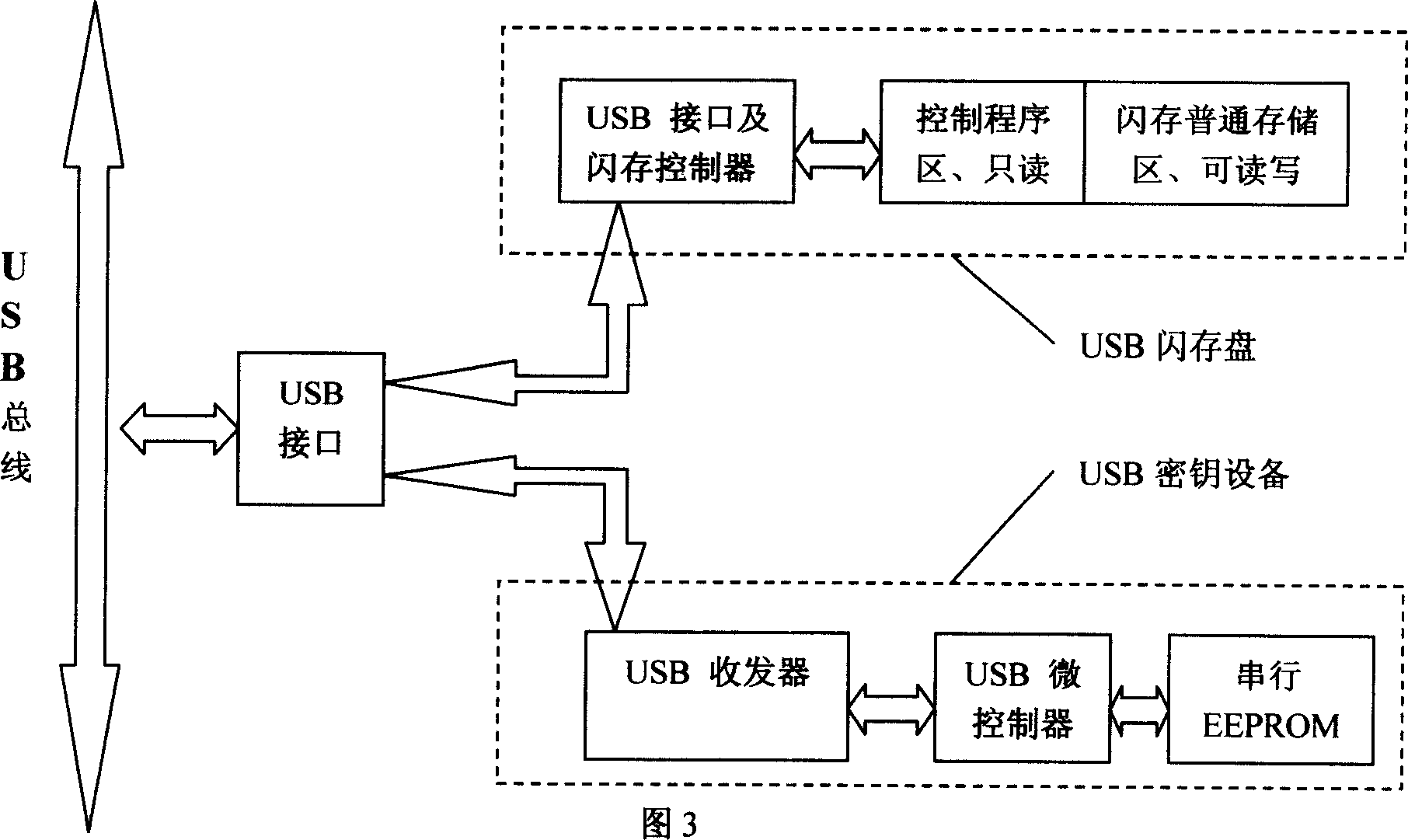
[0031] Figure 1 shows the architecture of the program and the interaction of each part. After the user puts forward a lock and unlock request, the "authority information identification module" requires the user to insert the "USB key device" and enter the user name and password, and then the "authority information identification module" will call the "bottom USB driver module" to read out the "USB key device". After checking and authenticating the user's identity, the "authority information authentication module" will call the "hard disk lock and unlock execution module" to complete the hard disk lock and unlock. The control program is the core of the whole scheme, and all the affairs in the scheme are scheduled by the control program. The authority information authentication module provides a graphical input interface to the user, and disp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com