A method for inputting private data in network application
An input method and network application technology, applied in the input field of confidential data, can solve problems such as loss of traders, unavoidable data theft, theft of trader's account and password data, etc., to ensure the effect of security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
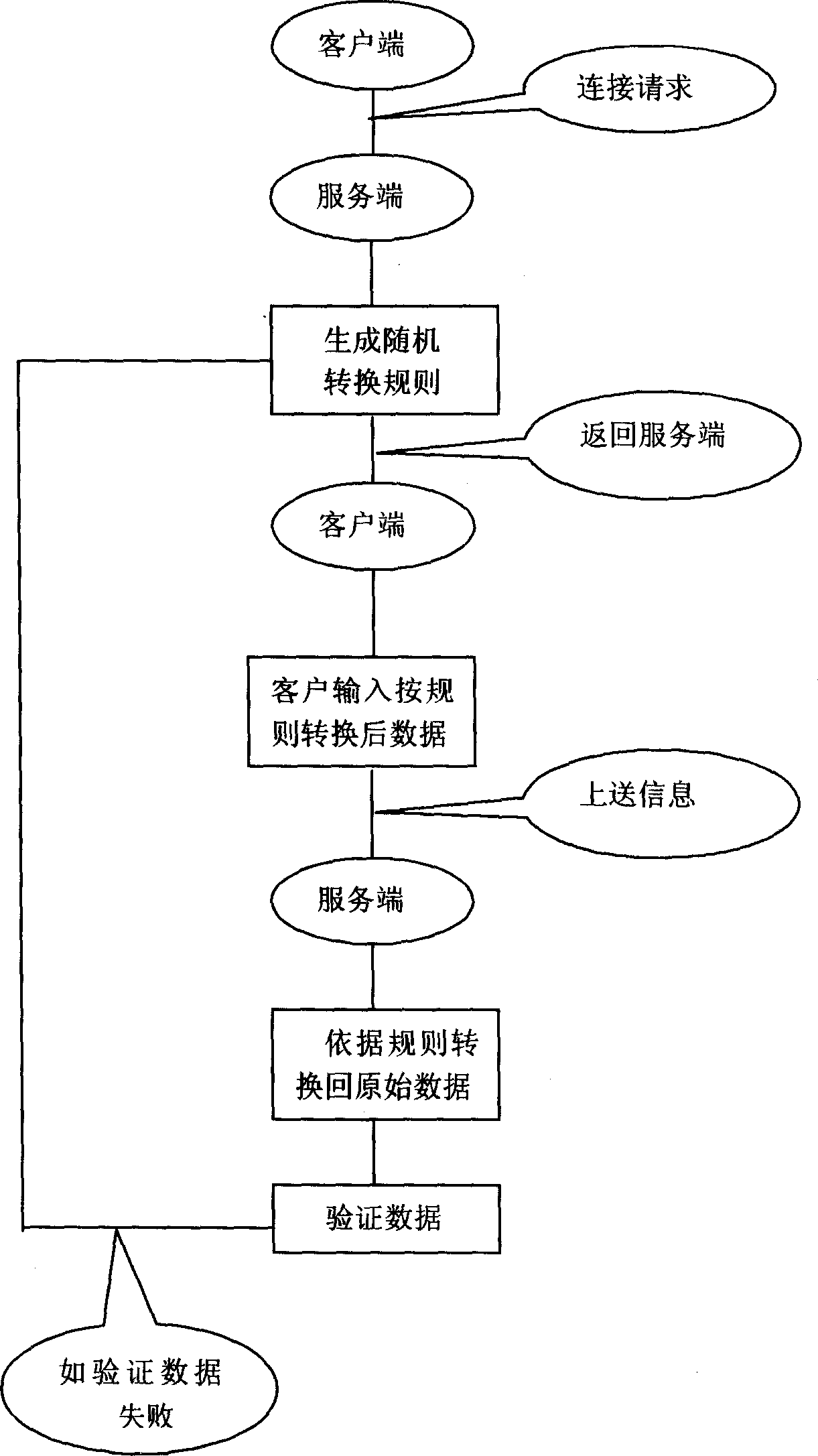
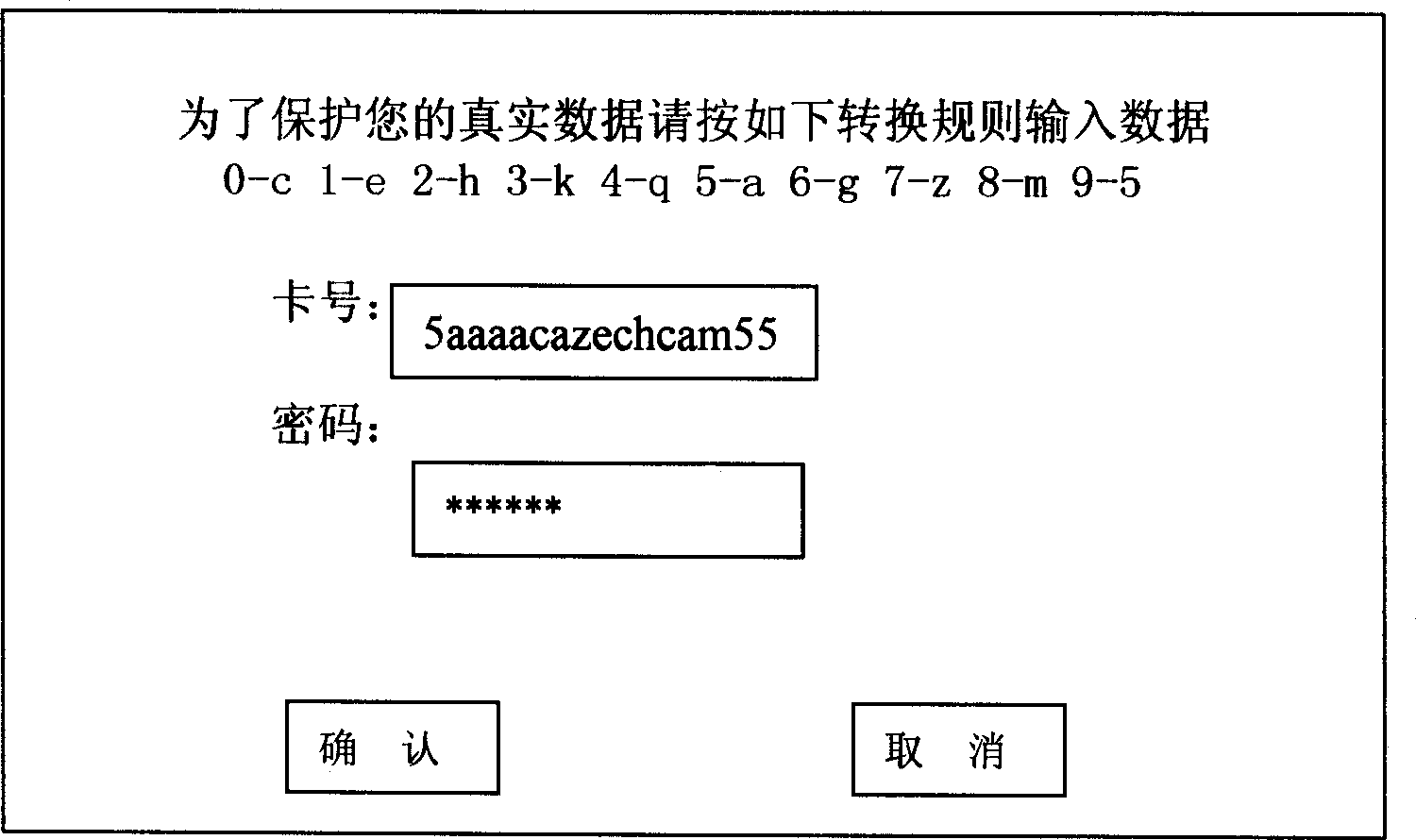
[0017] In online transactions, there are client software such as browsers in the foreground and server software in the background. The method of inputting confidential data in this network application is that when client software such as a browser logs in to the server software of the corresponding website, the server software randomly generates a data input conversion rule and returns it to the client software, and the client software converts the rules to the client software. The data input conversion rules are displayed on the page. According to the data input conversion rules, the client users convert the real data to be input into input data before inputting, instead of directly inputting real data.
[0018] For the operation steps of the input method in the embodiment of the present invention, see figure 1 , the input method includes the following steps:
[0019] 1. The client software logs in to the server software and sends a connection request.
[0020] 2. After rec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com