Differential power consumption analysis shield circuit for DES encrypted chip
A technology for differential power analysis and shielding circuits, which is applied in the field of information security and can solve problems such as increasing noise, increasing circuit power consumption, and increasing circuit noise.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028]Further describe the present invention below in conjunction with accompanying drawing.
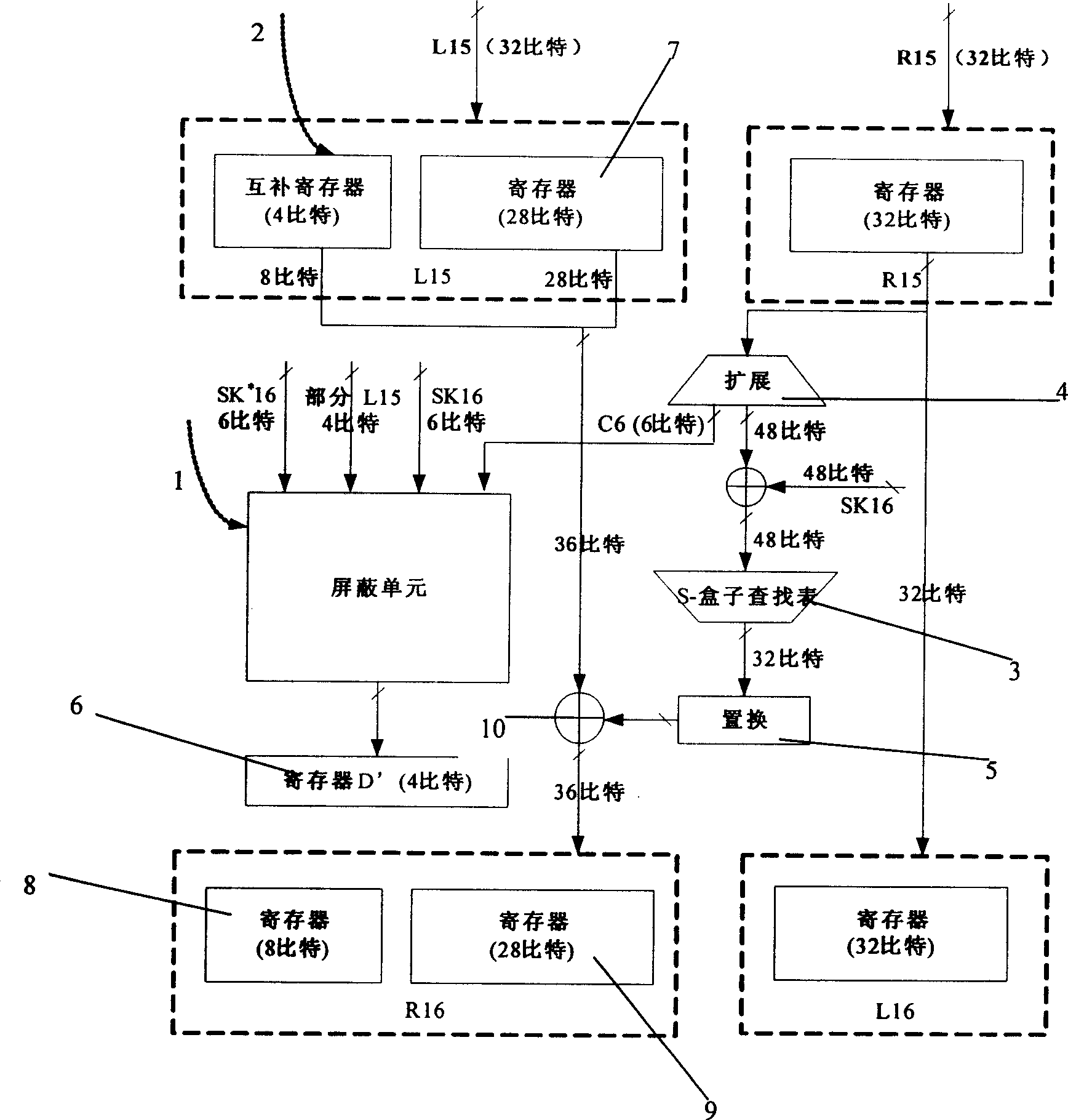
[0029] The DES encryption process is divided into three stages. First, after an initial permutation of the 64-bit plaintext, bit rearrangement produces the permuted input. The next stage consists of 16 loops over the same function, which itself contains both permutation and replacement functions. The 64-bit output of the last cycle (the 16th round) is a function of the input plaintext and the key, and its left and right parts are exchanged to obtain the pre-output. Finally, a 64-bit ciphertext is generated by a permutation inverse to the initial permutation.
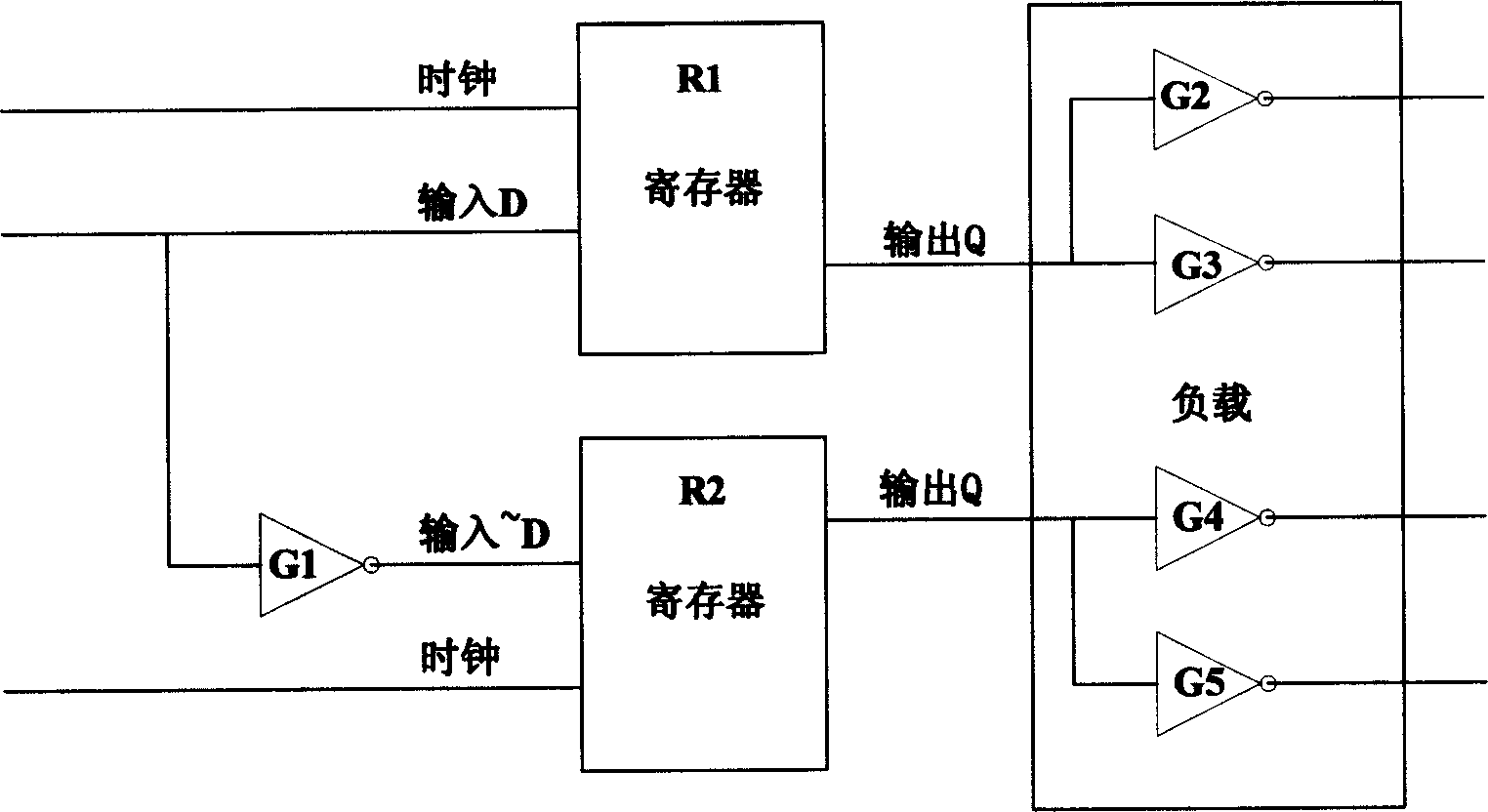
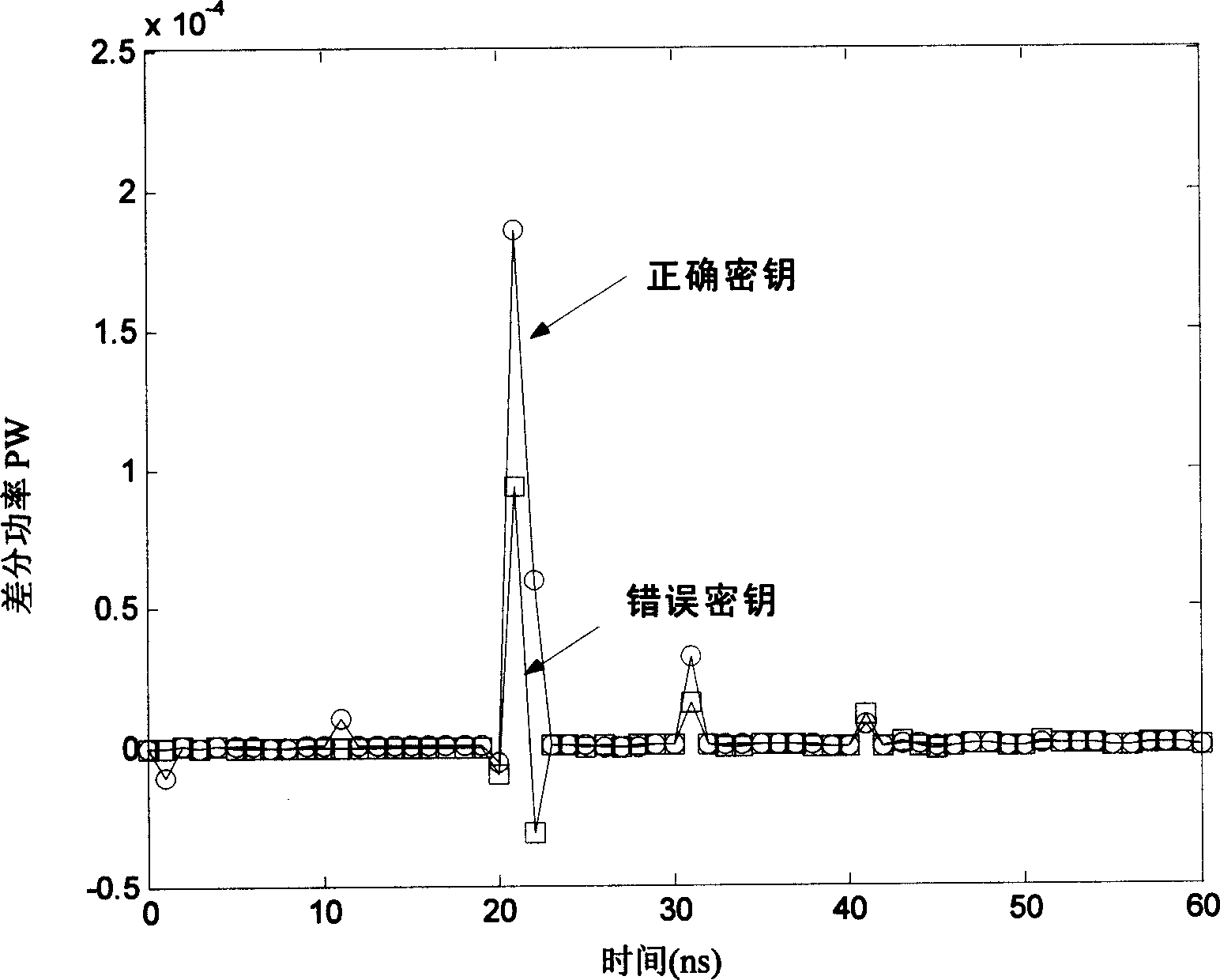
[0030] The attacker using the differential power analysis method selects the decision equation according to the calculation process of the 16th round, and attacks the 16th round key that enters each S box in turn, so as to obtain a total of 48 bits of key information, and then only needs to exhaustively enumerate Obtaining t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com