Restoring method for source string of enhanced multiple Hash in use for system of intrusion detection
An intrusion detection system and hash function technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problem of high computational complexity, difficulty in restoring the original string information by multi-hash methods, and reversibility of hash algorithms. Not good and other problems, to achieve the effect of small alarm error, high restoration accuracy, and timely response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
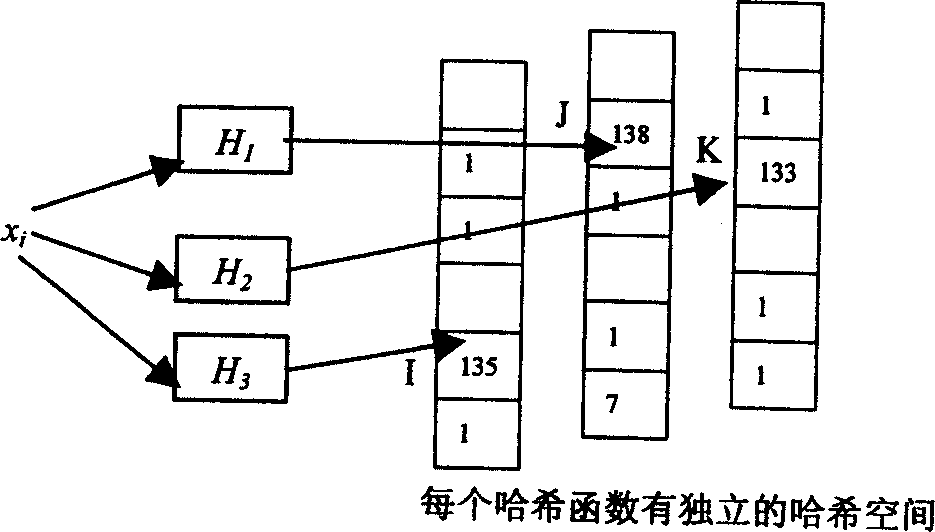
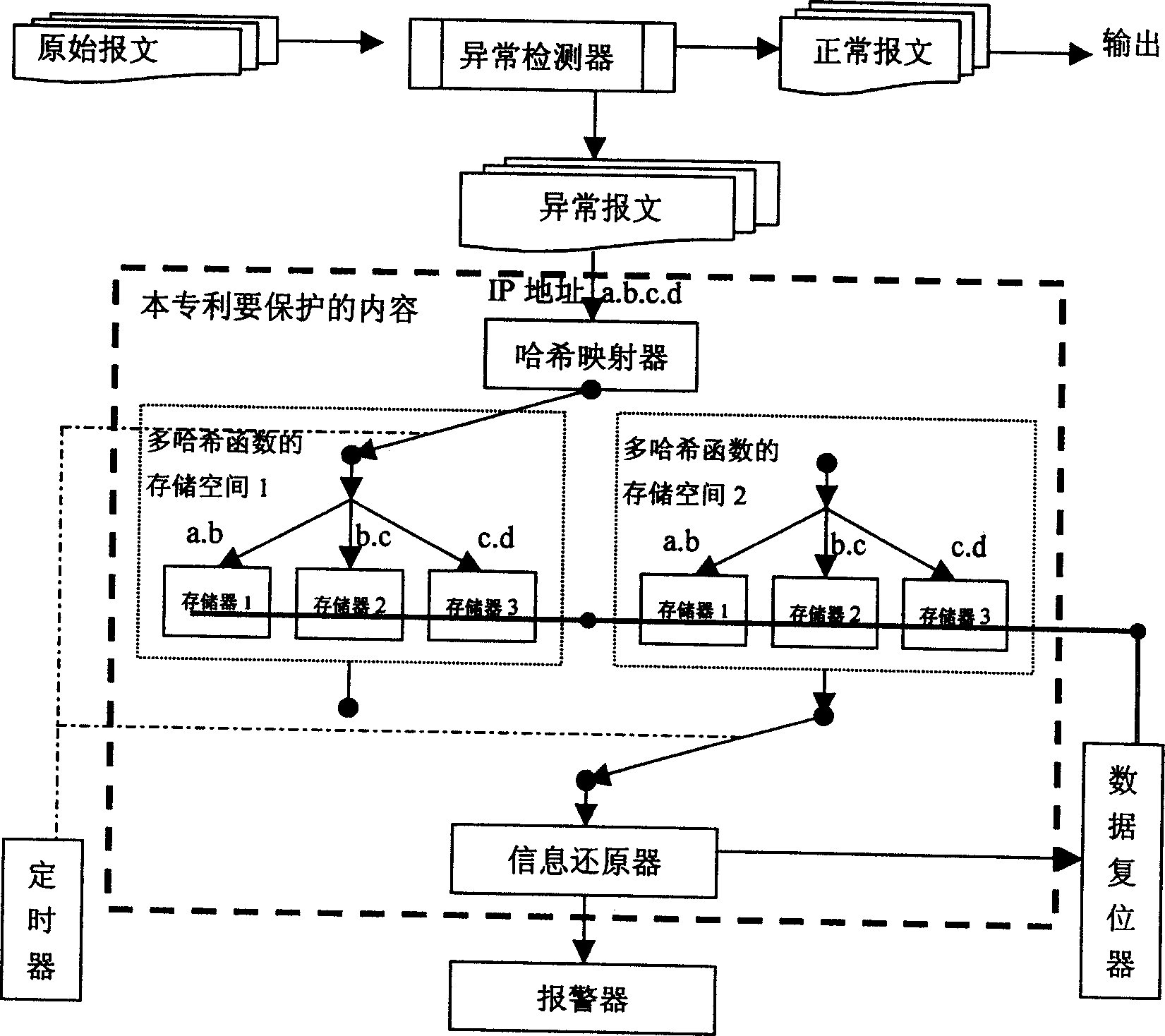
[0032] An enhanced multi-hashing source string restoration method for intrusion detection systems used to detect computer network monitoring and analysis:
[0033] 1. After the original message is detected by the anomaly detector, the original message is divided into normal message and abnormal message, the normal message is output, and the IP address of the abnormal message is used as the input for information restoration;
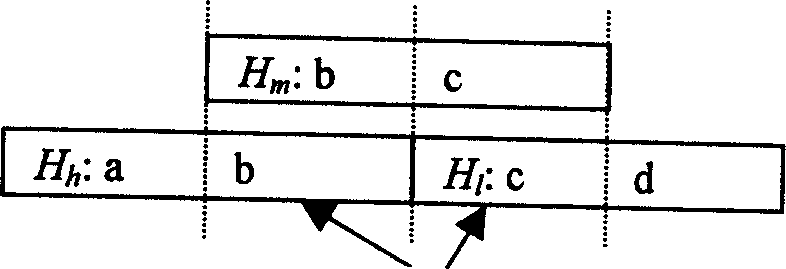
[0034] 2. The IP address information of the abnormal message is mapped to one of the two multi-hash method structures by the hash function mapper. If the IP address is a.b.c.d, and a, b, c, and d all represent values between 0-255, then The hash function that takes the upper 16 bits of the IP address is called the first hash function, denoted as H h (a.b); the hash function with the middle 16 bits is called the second hash function, denoted as H m (b.c); the hash function with the lowest 16 bits is called the third hash function, denoted as H l (c.d),...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com