System and method of preventing network account from stolen
A technology of network account and anti-theft method, which is applied in the field of network account anti-theft system, and can solve problems such as inconvenient use, refusal to log in, misalignment of clocks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
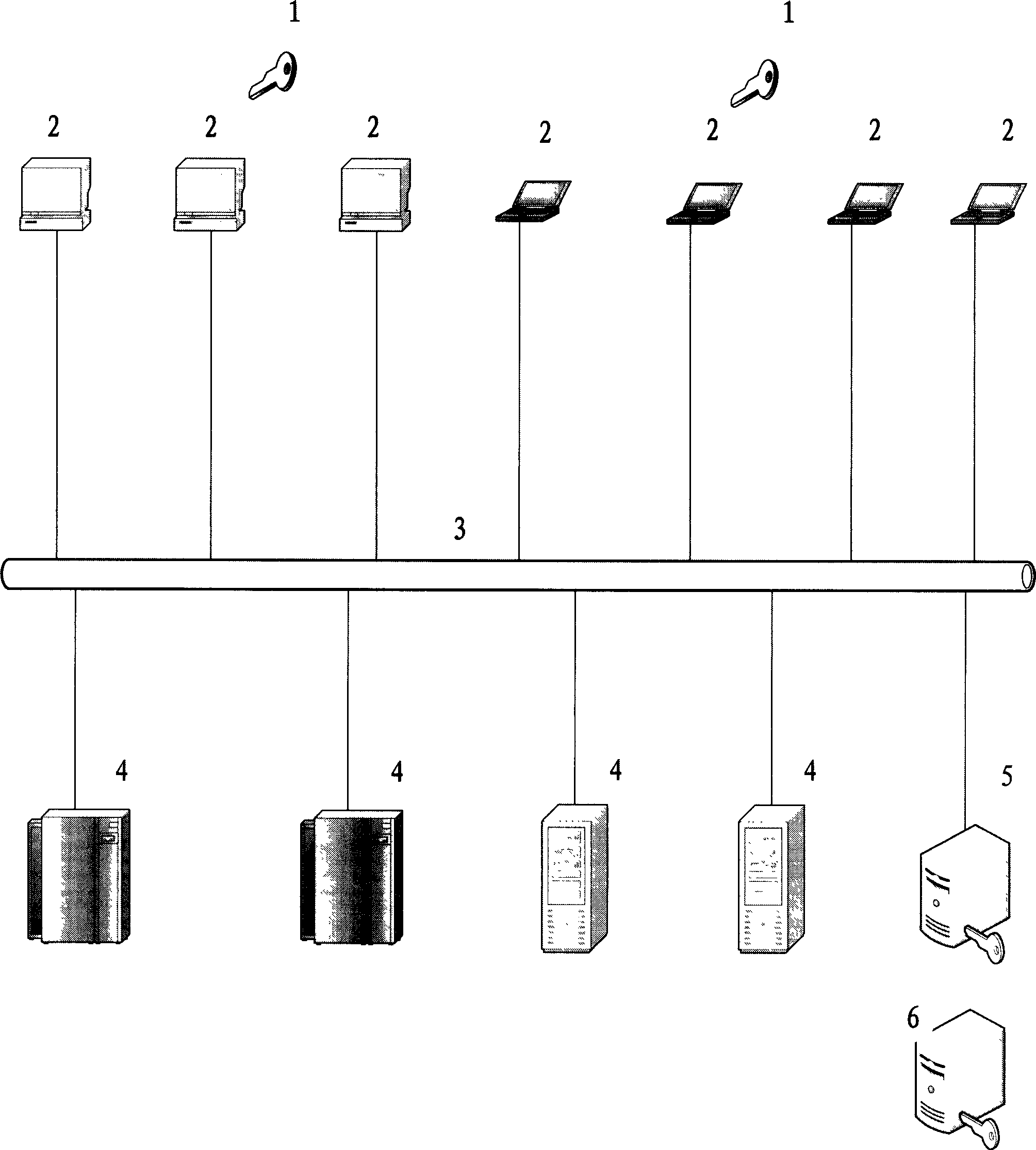
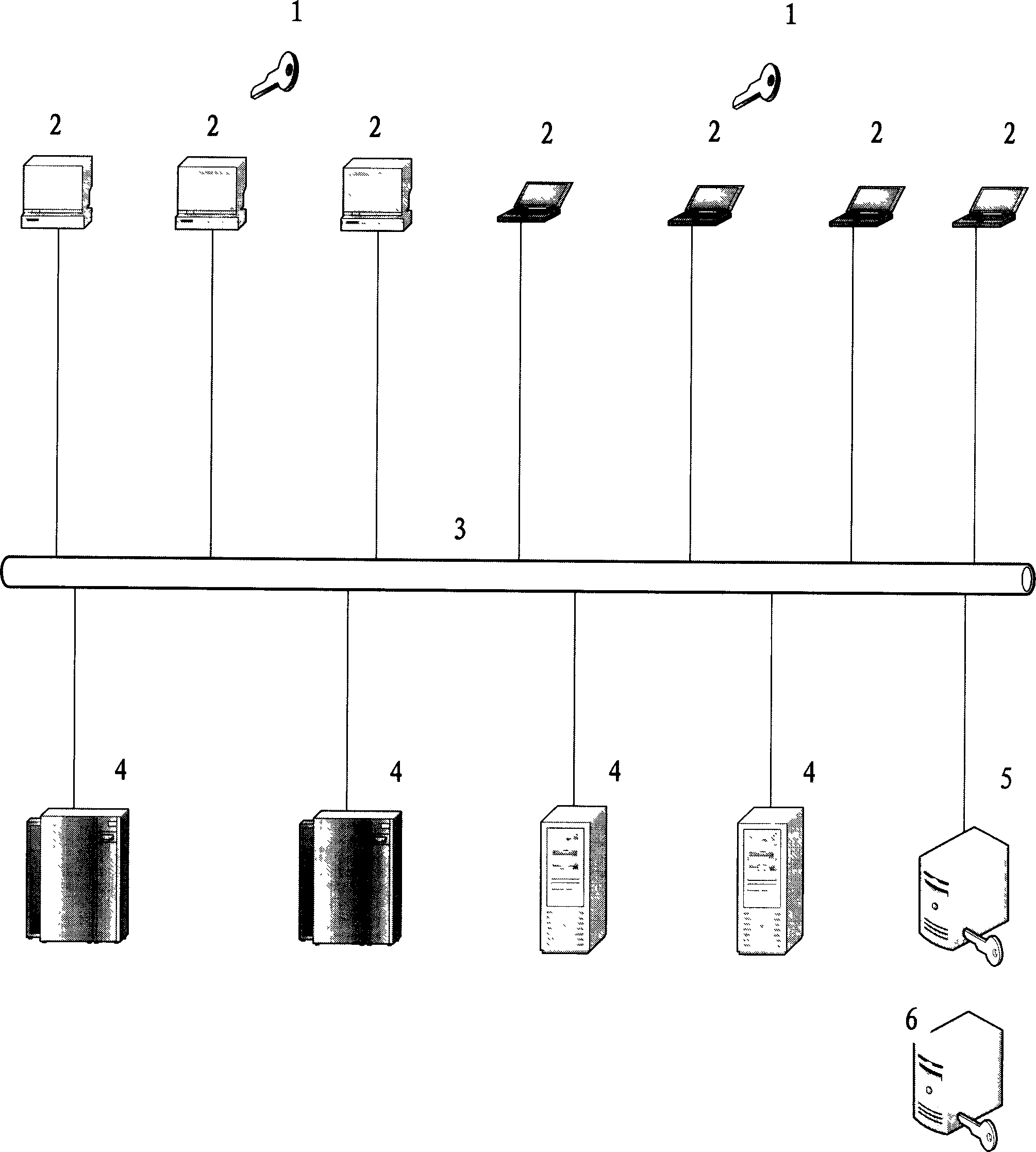
[0088] As shown in Figure 1: network account anti-theft system of the present invention comprises: external network account anti-theft device 1, client 2, application server 4, network authentication management server 5, programming equipment 6, described external network account anti-theft device and client It is connected through various communication interfaces such as USB, serial port, infrared, bluetooth, etc., and the client is connected with the application server and the network authentication management server through the network 3 (Internet, local area network, wireless network, etc.).
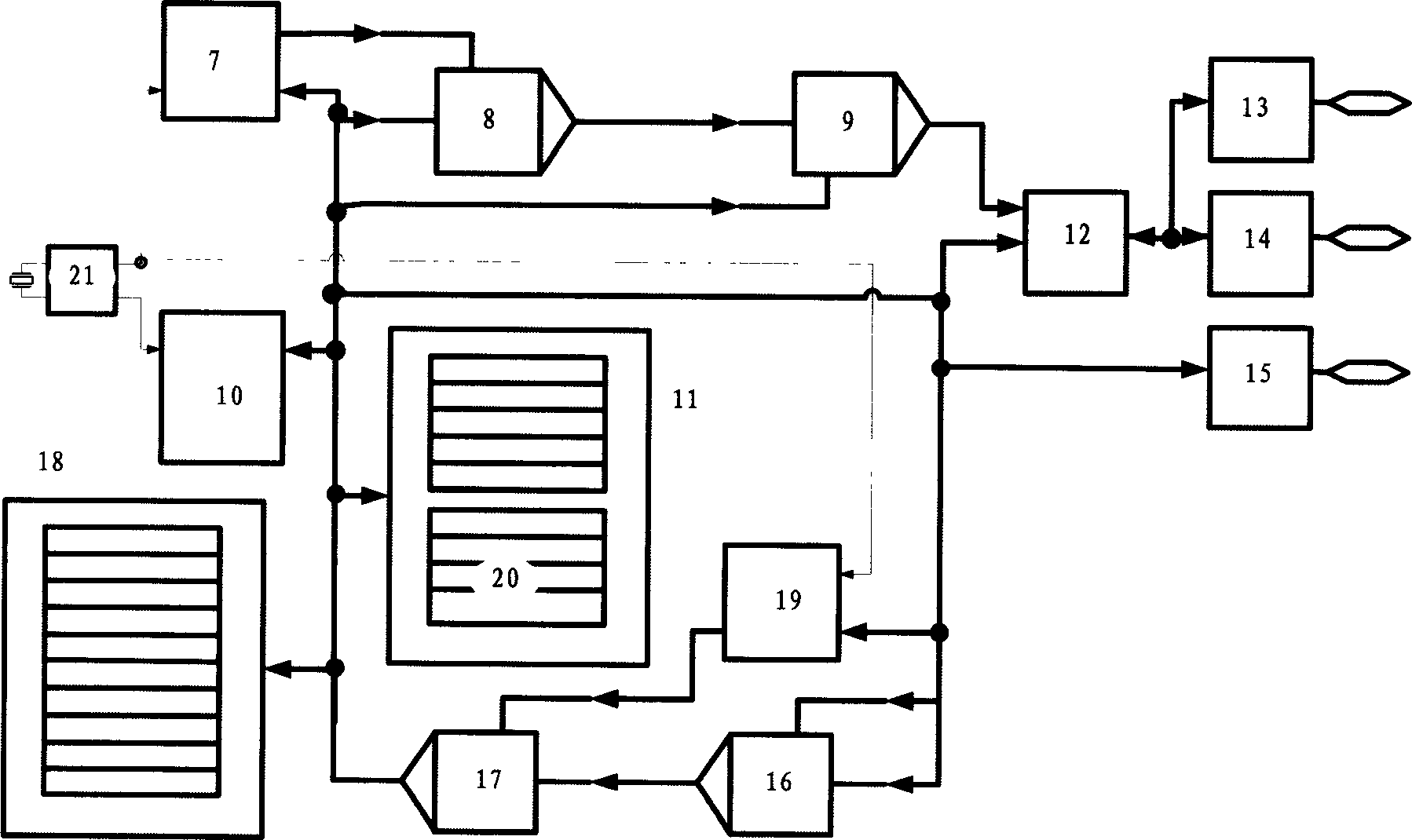
[0089] The external network account anti-theft device, which is connected to the client, is used to verify account information (such as internally stored account user passwords (generally high-strength passwords or secondary passwords of account users), serial numbers, account information, etc. , verification sequence, etc.) After dynamic encryption and public key encryption, the acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com