Strategy and method for realizing minimum privilege control in safety operating system
An operating system and privilege technology, applied in the field of security information systems, which can solve the problems of inability to solve the isolation and dynamic requirements of privileged control domains, the complexity of privilege management, and the growth of system risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
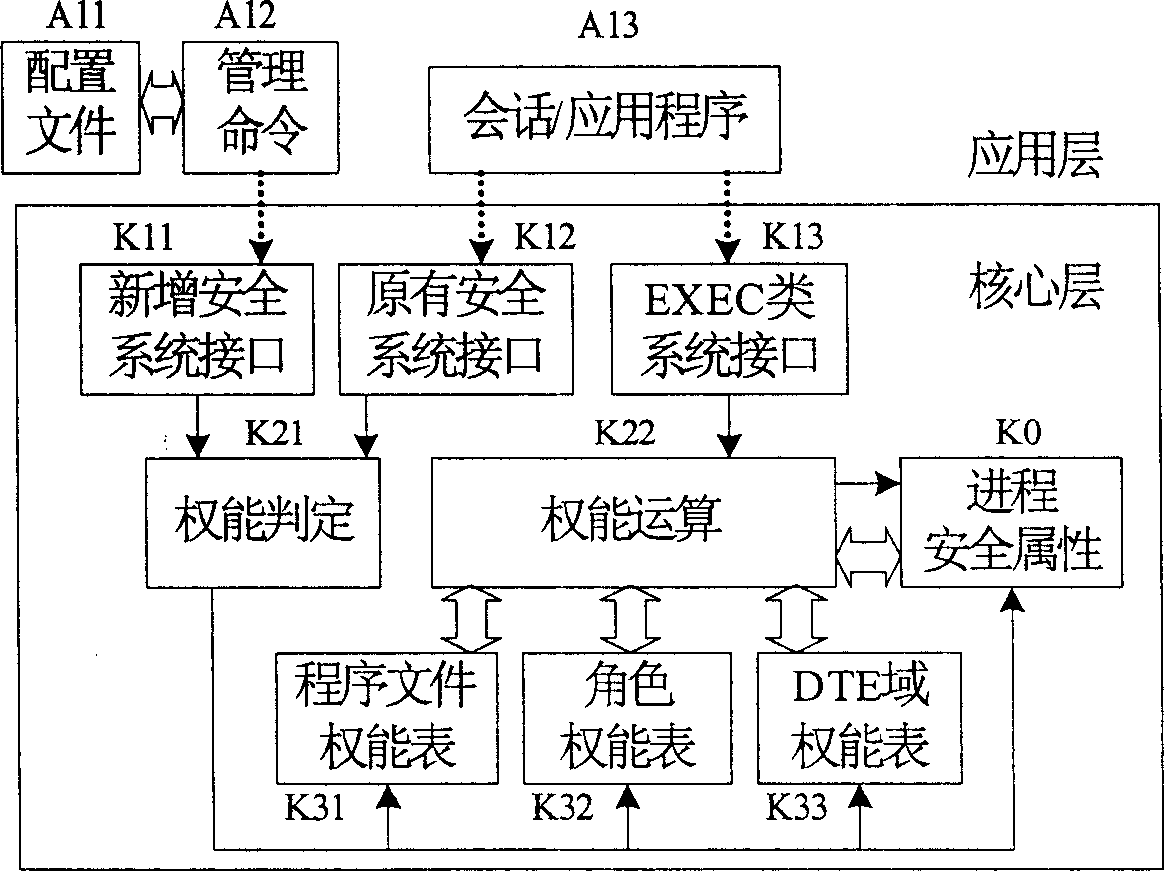
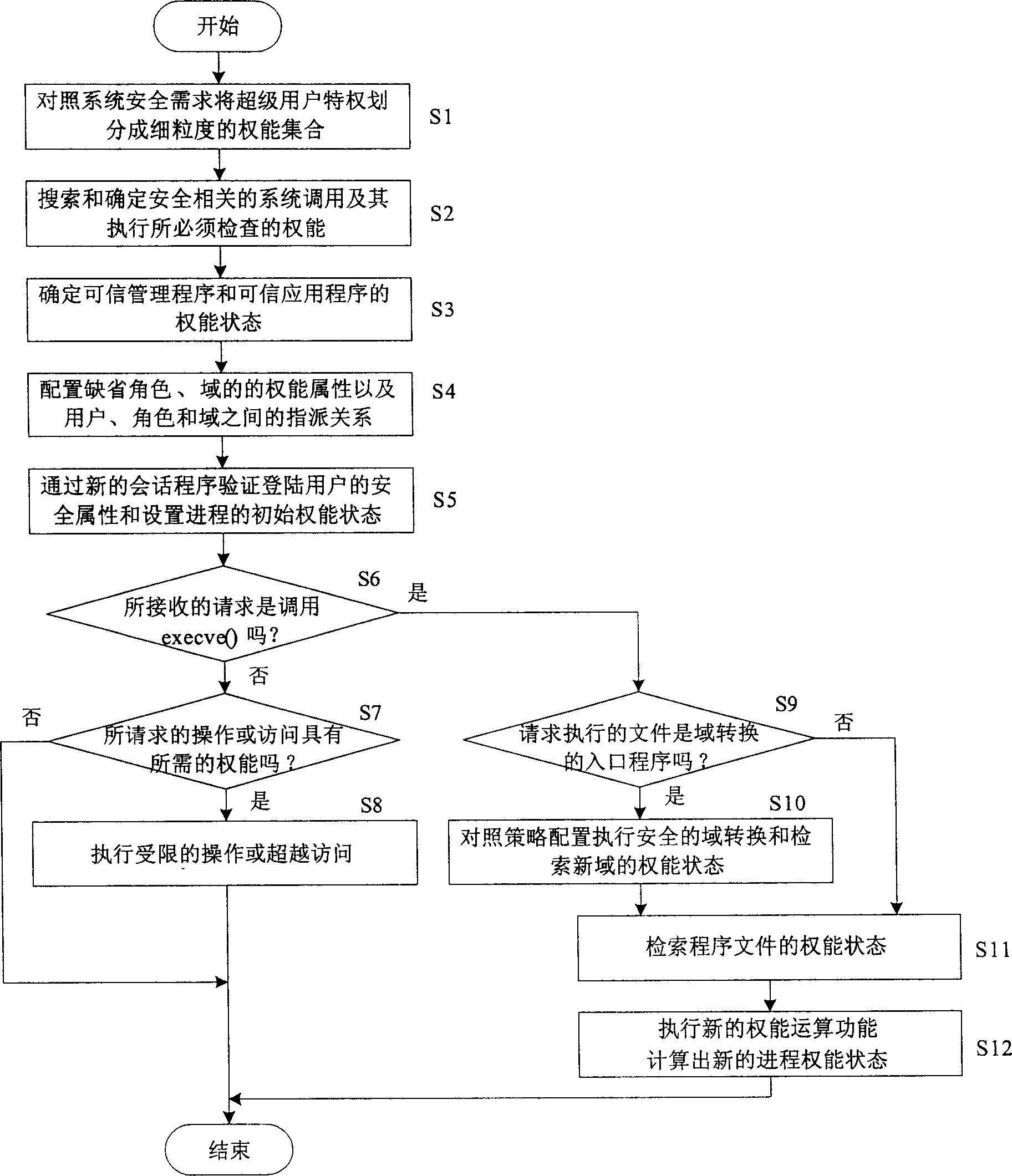
[0027] According to the above technical solution, an example of the implementation of the present invention in a LINUX-based security operating system is given below.
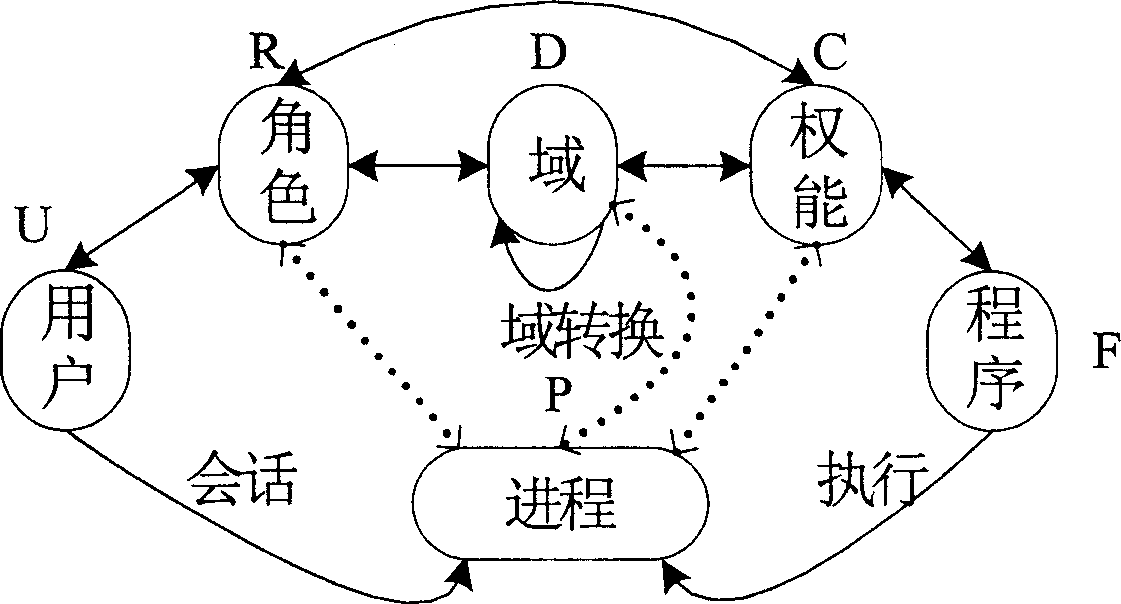
[0028] figure 1 Indicates the mapping relationship between authorized entities involved in the privilege control strategy. The specific technical steps of these relationships in the secure LINUX system are as follows:
[0029] 1. Define the capability set C, that is, divide the original system superuser privileges into several fine-grained capabilities. The current design supports the definition of 64 capabilities (the original LINUX system only supports the definition of 32 capabilities). This design requires that when defining capabilities, the security requirements of the system must be clarified, based on the security mechanisms to be implemented by the system, such as autonomous access control (DAC ), Mandatory Access Control (MAC) and Domain Enforcement (DTE) technologies to find out all security-related...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com