Security event associative analysis method and system
A security event and correlation analysis technology, applied in the field of security event correlation analysis, can solve problems such as lack of practical significance, and achieve the effects of avoiding ambiguity, improving robustness, and improving detection and recognition capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
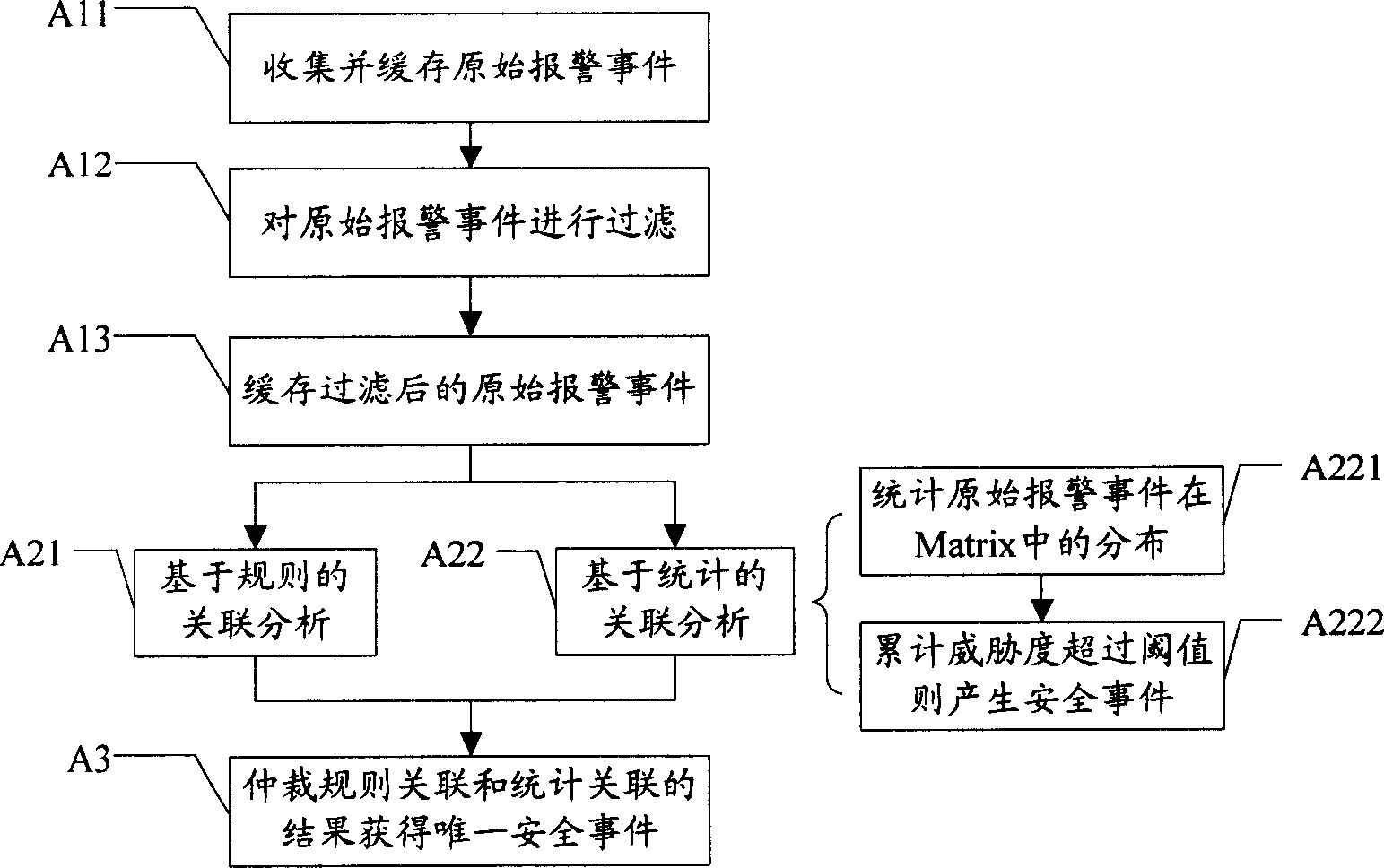
[0042] Embodiment 1, a security event correlation analysis method, the process is as follows figure 1 shown, including:
[0043]A1. Collect original alarm events; original alarm events come from various security devices or management programs, such as firewalls, IDS, antivirus software, system logs, etc. The collection of original alarm events can be centralized or distributed systems. In order to facilitate the processing of subsequent processes, it is better to cache and filter the collected raw alarm events, including:
[0044] A11. Cache the collected original alarm events; usually, the original alarm events can be stored in the form of event queues in chronological order;
[0045] A12. Filter the original alarm events according to the preset filtering rules; this step performs simple processing on the original alarm events, such as removing errors and duplicate alarms, or using some simple rules to make the collection of alarm information have a certain purpose or tende...
Embodiment 2
[0073] Embodiment 2, a security event correlation analysis method, the process is as follows Figure 4 shown, including:
[0074] B1. Collect original alarm events;
[0075] B21. Perform rule-based correlation analysis on the original alarm event;
[0076] B22. Perform statistical-based correlation analysis on the original alarm events;
[0077] B3. Arbitrate the security events generated by rule association and statistical association respectively to obtain a unique security event;
[0078] The specific execution method of the above steps is the same as the corresponding steps in the first embodiment. The difference between this embodiment and the first embodiment is that after the statistical correlation of the original alarm event is performed in step B22 and a security event is generated, the security event is also used. The association rules applicable in the rule association analysis can be obtained by the data mining of the data mining, and the following methods can ...
Embodiment 3
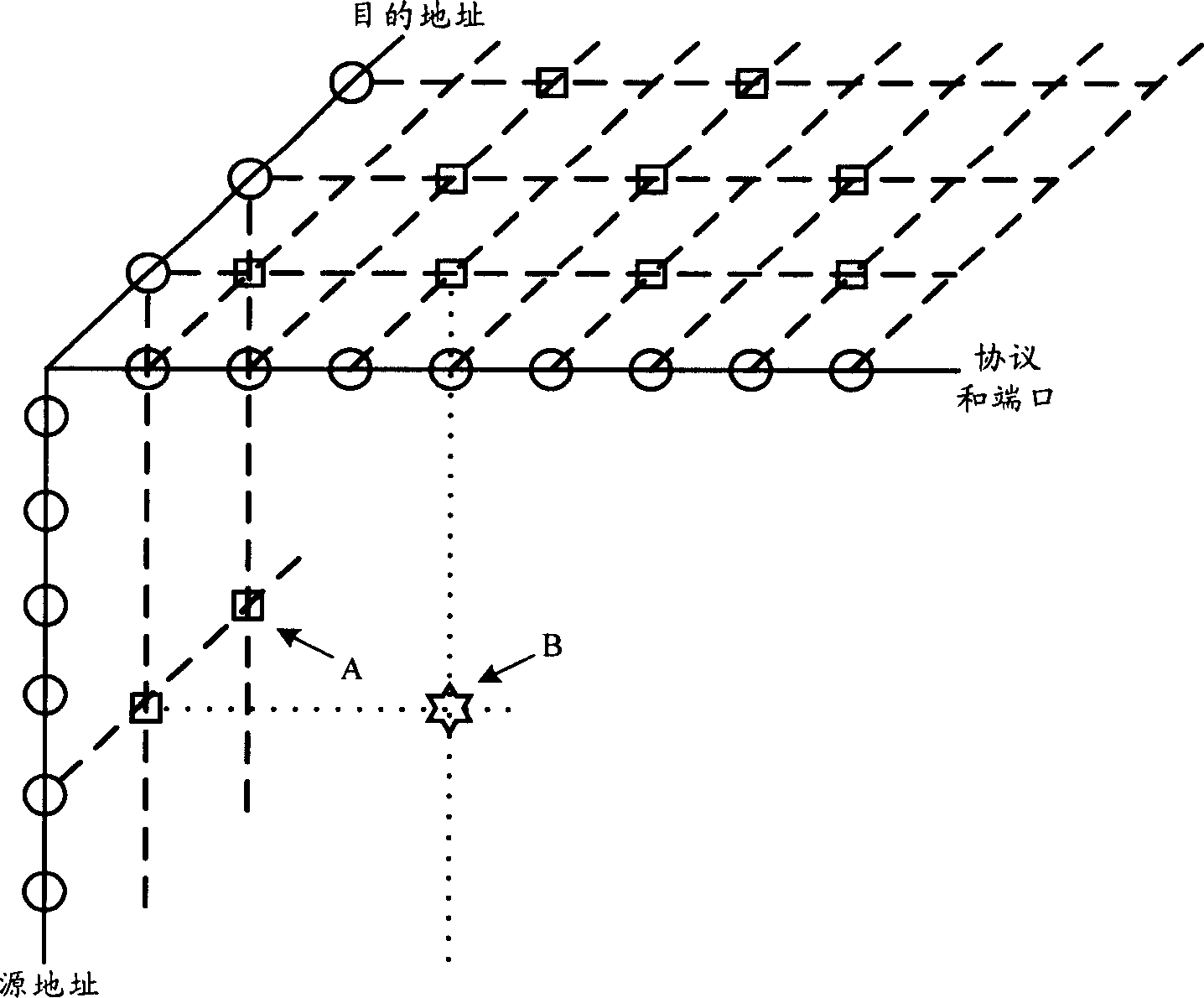
[0087] Embodiment 3, a security event correlation analysis system, such as Figure 5 As shown, it includes an event queue module 11, a rule association module 12, a statistics association module 13, a structure analysis module 14, and an event filtering module 15;
[0088] The event queue module 11 collects the original alarm events, and provides the original alarm events to the rule association module 12 and the statistics association module 13 respectively;
[0089] The event filtering module 15 filters the original alarm events collected by the event queue module 11 according to the preset filtering rules, and deletes the original alarm events that satisfy the filtering rules from the event queue;
[0090] The rule association module 12 performs pattern matching on the original alarm event according to a preset association rule, and generates a security event according to the matching result;
[0091] The statistical correlation module 13 counts the attribute-based distrib...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com