Auditing method for personal consumption credit
A credit and consumer-end technology, applied in data processing applications, commerce, instruments, etc., can solve problems such as insufficient security and easy to be stolen by hackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
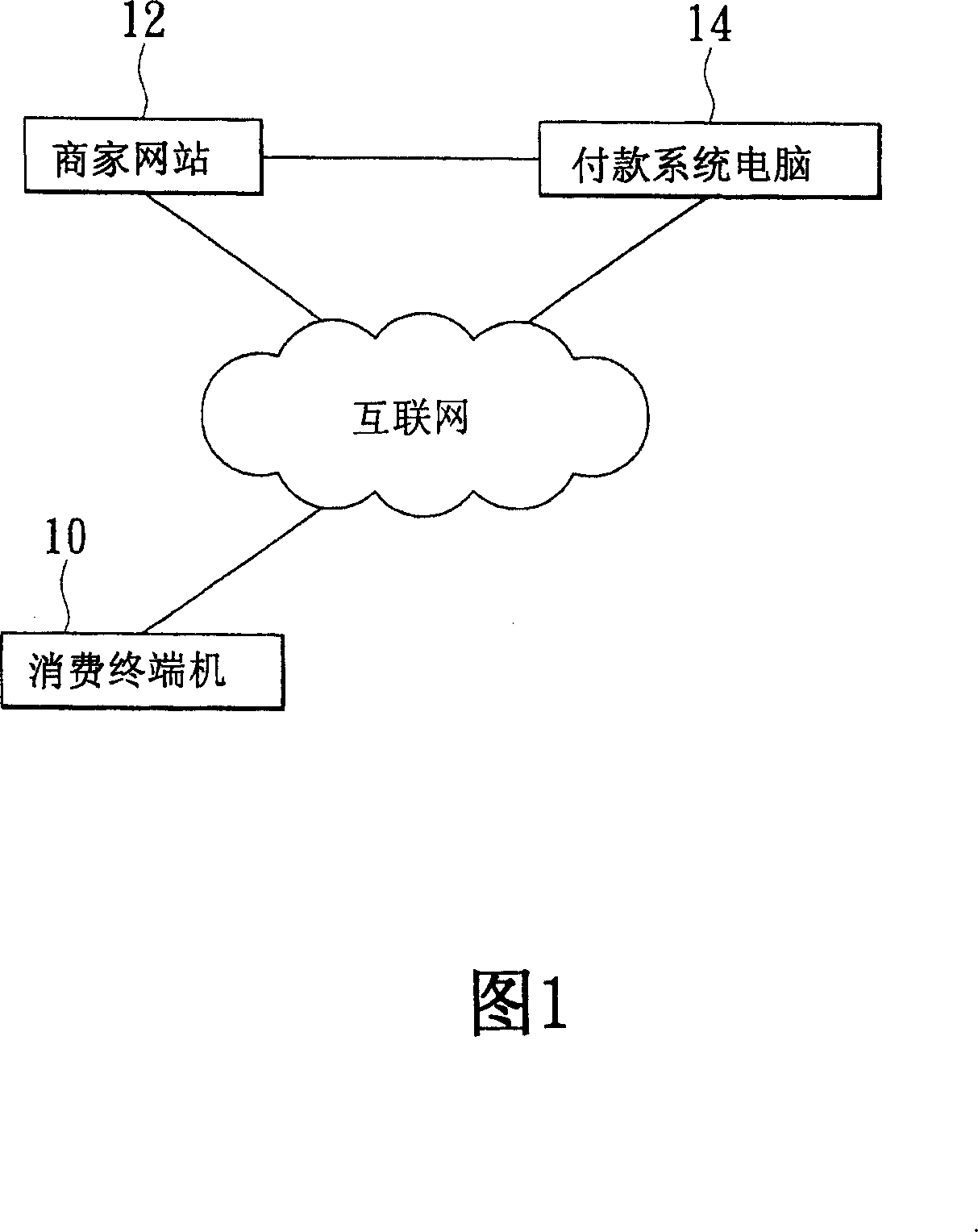
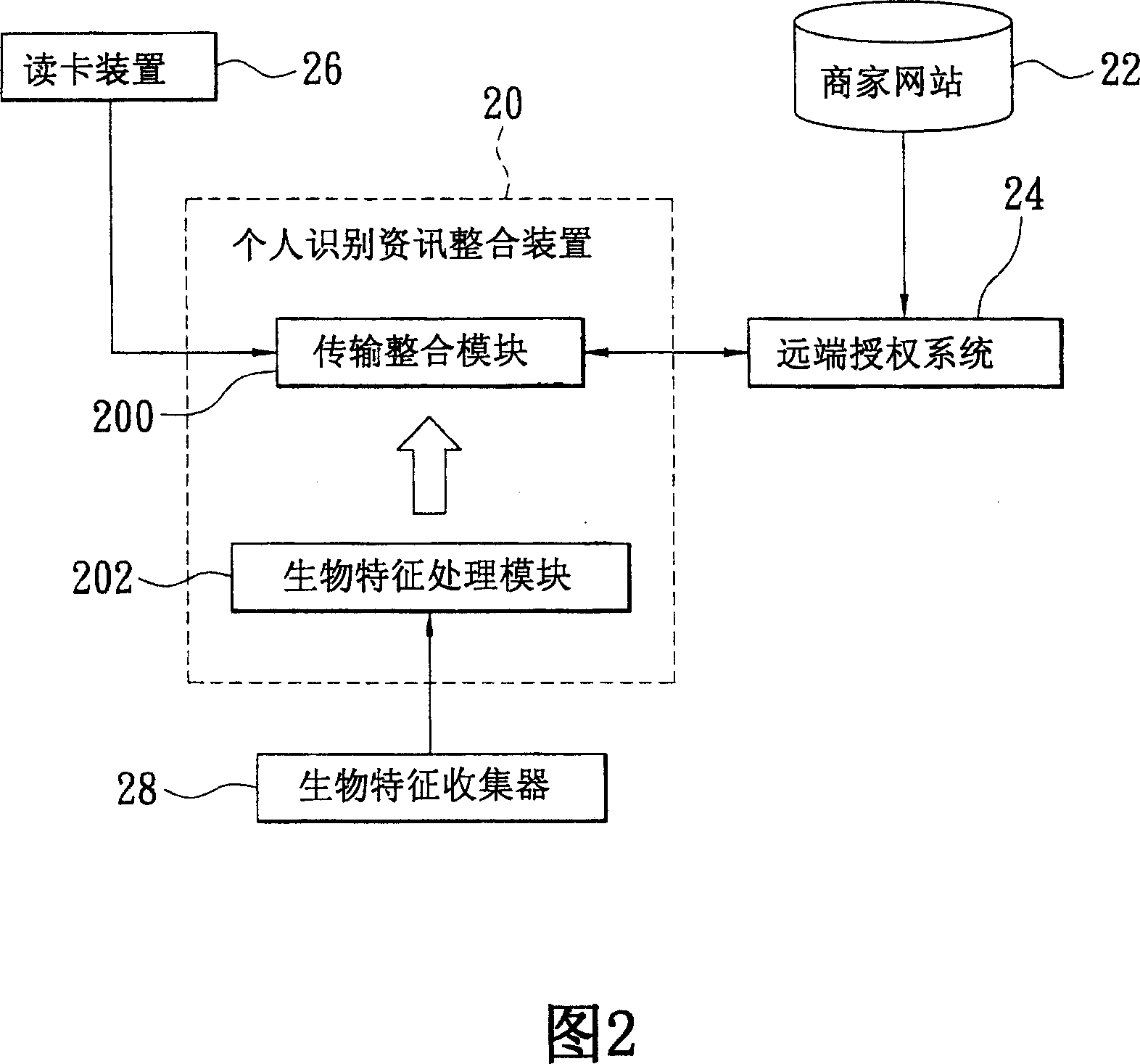
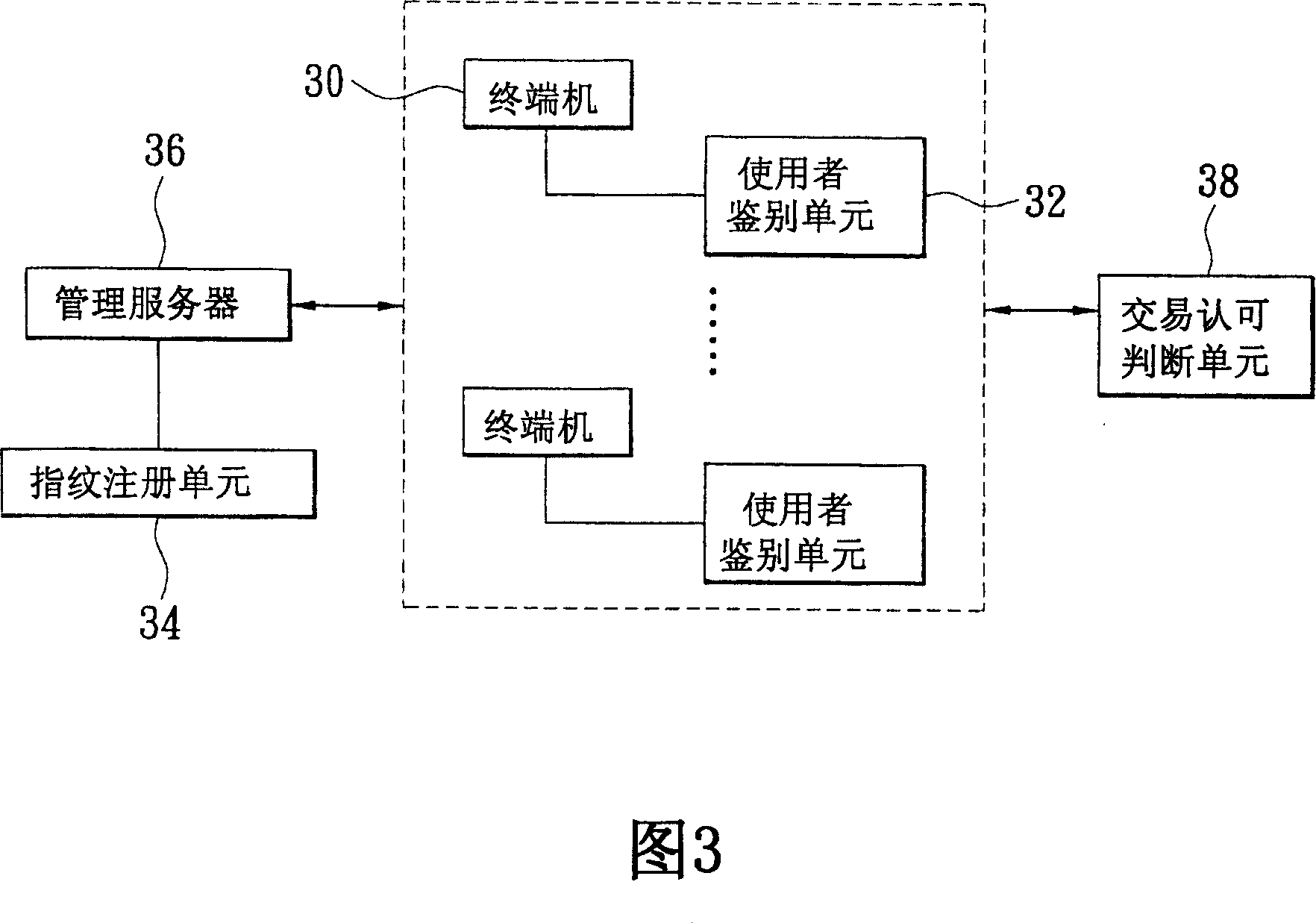
[0035] Please refer to FIG. 4 for a schematic diagram of the system architecture of the present invention. This is the review and consumption relationship between the authorization end, the consumption end, and the user. The user 40 must first go to the authorization end 44 to perform pre-recording actions (including logging in personal data and personal identity authentication. data), the pre-recorded action user 40 utilizes a camera device at the authorization end 44 to capture dynamic audio-visual data and static pictures and store them in a central server (not shown) of the authorization end 44. When wanting to consume, the consumer terminal 42 can send the identity information provided by the user 40 to the central server through the network to find out the matching user 40 information, and the central server will transmit the dynamic video and audio data stored in advance by the user 40 to the central server. Return to the consumption terminal 42, so that the consumption ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com