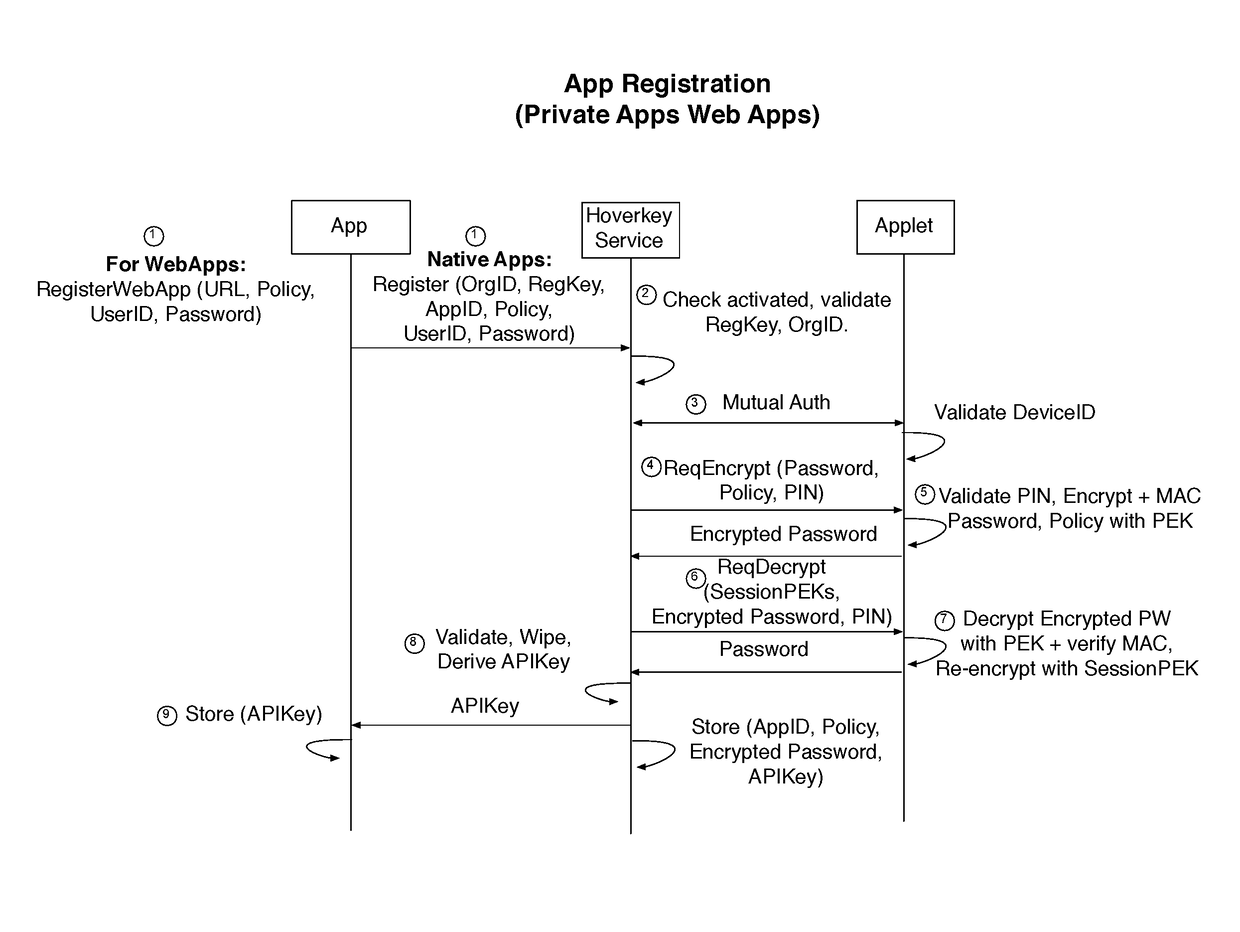
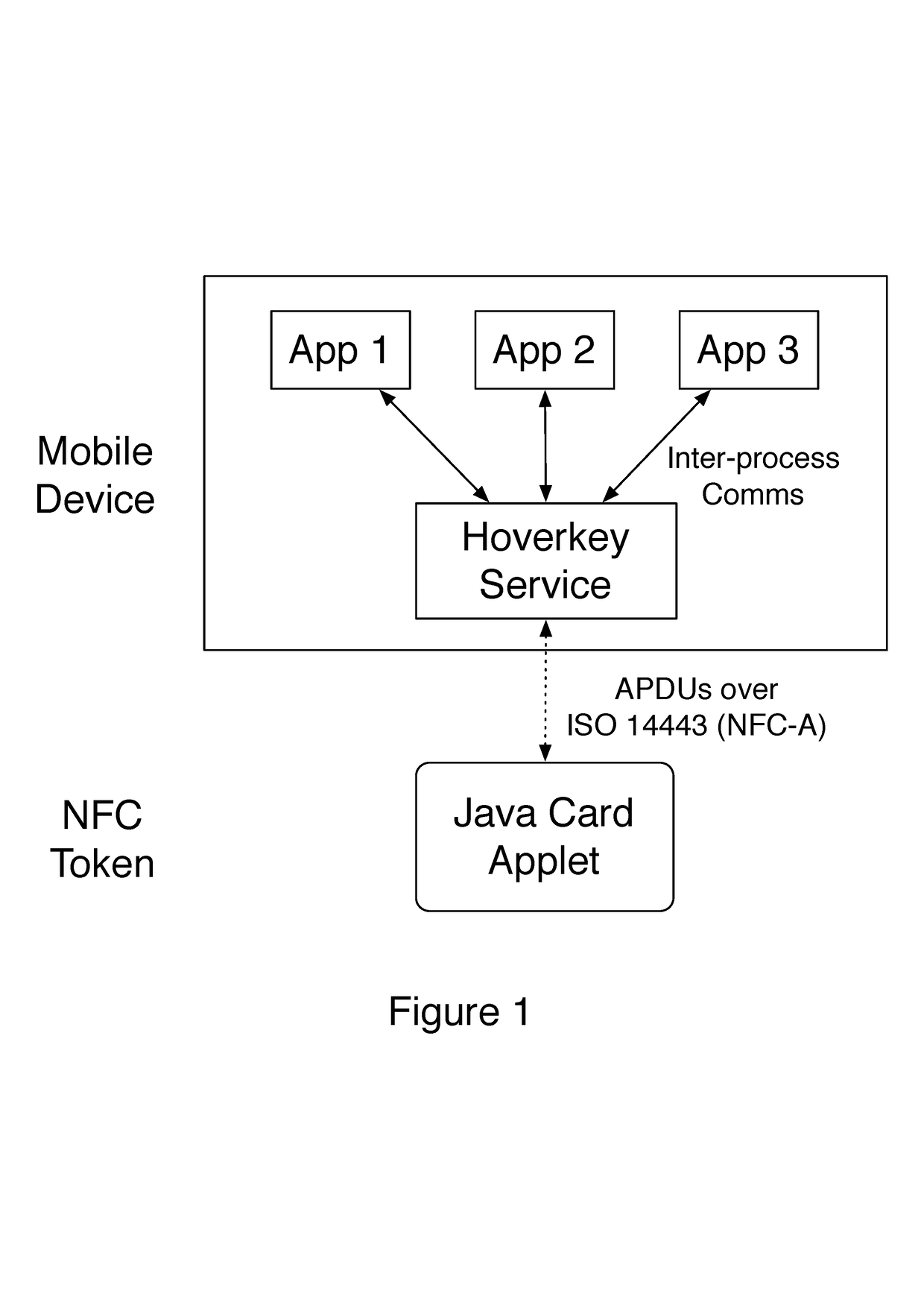
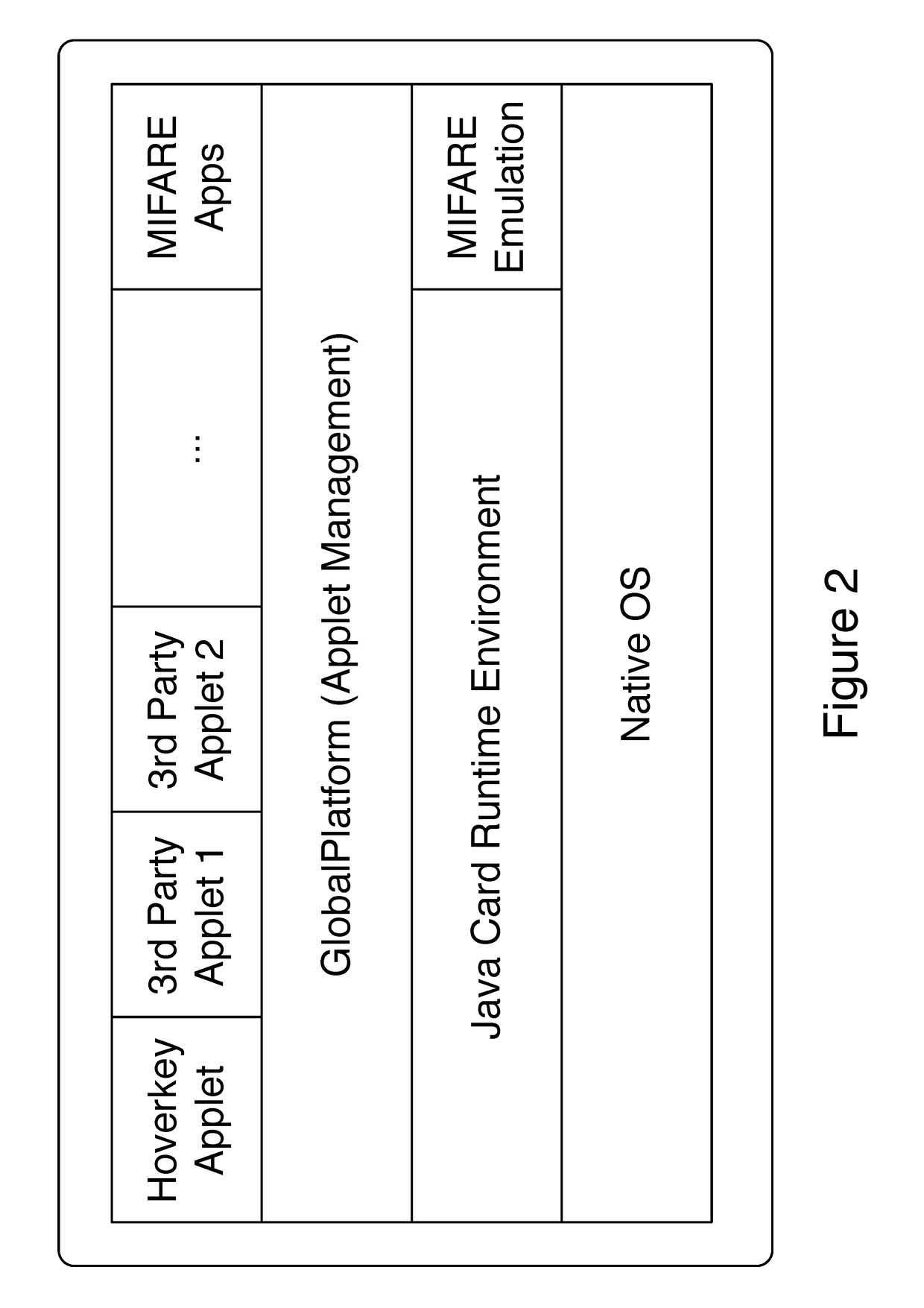
Method and system of conducting a cryptocurrency payment via a mobile device using a contactless token to store and protect a user's secret key
a mobile device and user technology, applied in the field of method and system of authenticating users, can solve the problems of long and difficult to predict passwords, many problems, and long passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
: Digital Signature: function=digital signing function, plain authorization=private signing key; parameter=hash of message; output=digital signature on message hash[0039]Example 2: Key Derivation: function=HMAC-based key derivation function; plain authorization=key derivation master secret; parameters=session random numbers, output length; output=key derived from master secret[0040]Example 3: Re-encryption: function=encryption function; plain authorization=encryption key; parameter=(another) encryption key; output=the plain authorization encrypted with a different key[0041]Example 4: One-Time Passcode (OTP): function=hash-based passcode generation function; plain authorization=OTP secret key; parameter=current counter value; output=passcode computed from counter
[0042]The authorization may comprise a password, PIN or cryptographic key.
[0043]The unlock response may be transmitted to the mobile device under the protection of an encryption key, such as a session key.
[0044]The token may ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com