Communication system
a communication system and communication system technology, applied in the field of communication systems, can solve the problems of inability to deny the possibility of leaking the password to a third party, the difficulty of determining and the difficulty of establishing whether or not a communicating party is an authentic party
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
embodiment 1
[0115] [Embodiment 1]
[0116] This embodiment explains in detail the re-write operation of the reference living body information stored in the authentication apparatus by using the authentication apparatus.
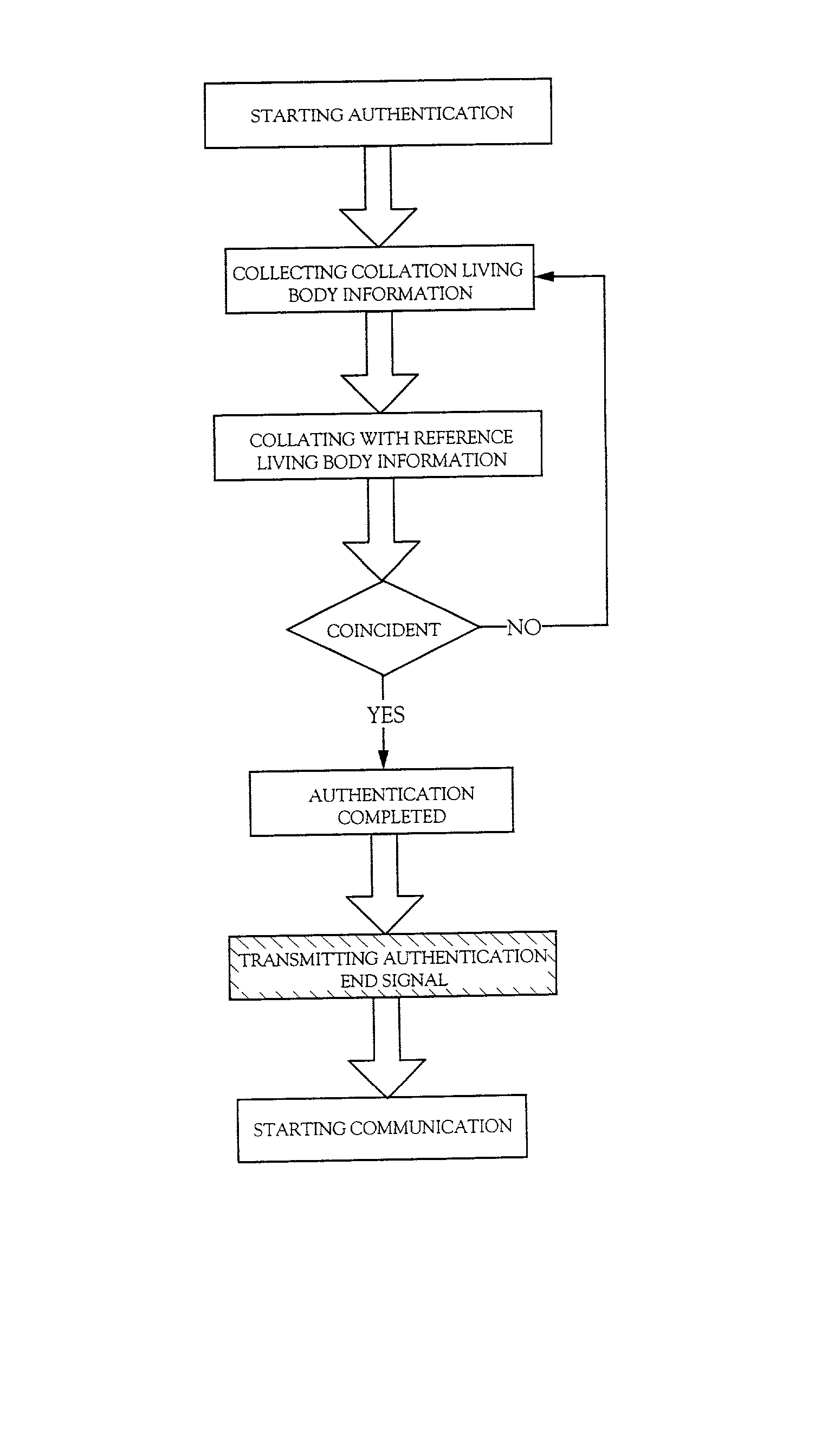
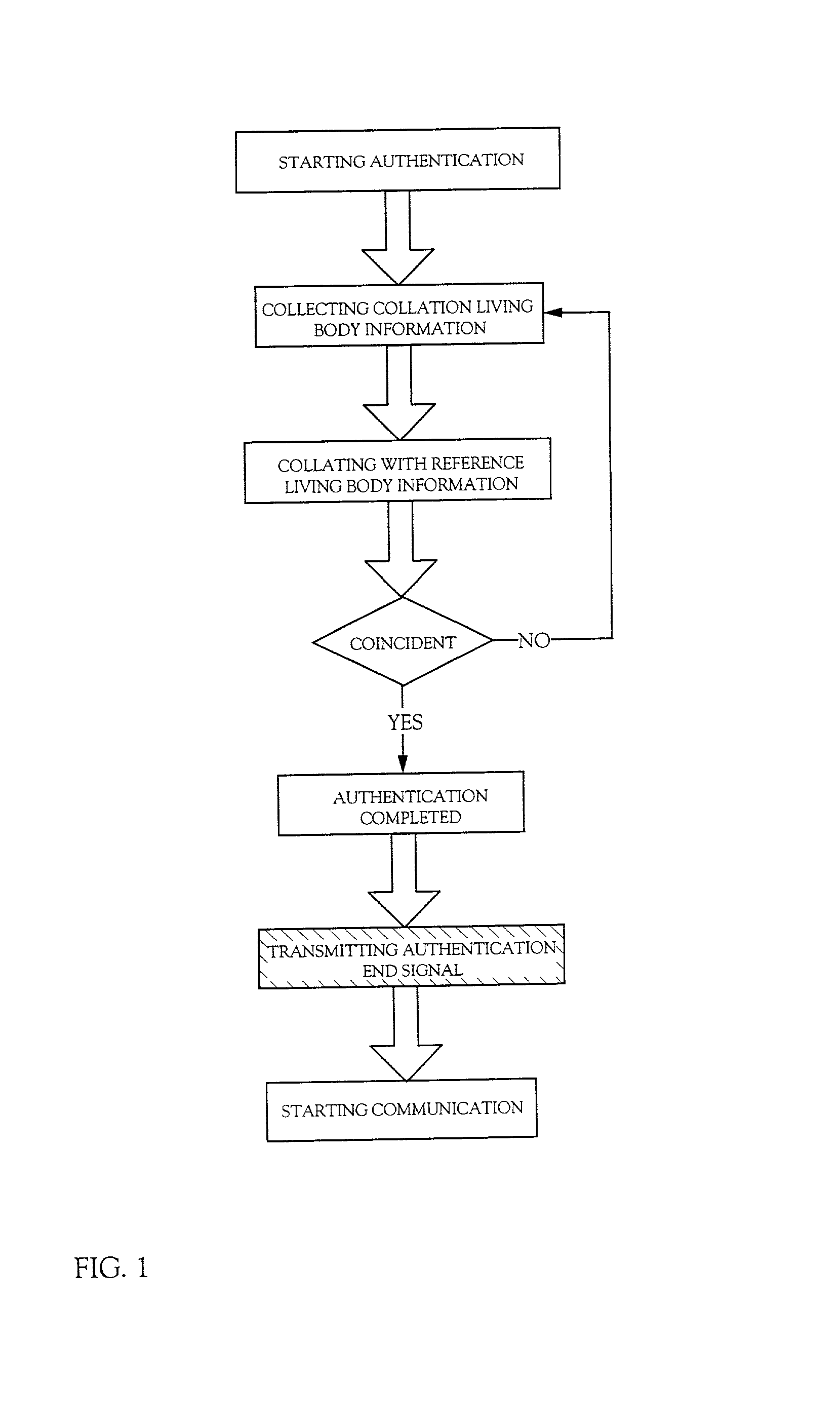
[0117] FIG. 6 shows a flow of the re-write operation of the reference living body information in this example. First, authentication is conducted to authenticate the user as an authentic person. Incidentally, the detailed explanation of authentication has already been given and is hereby omitted.
[0118] As authentication is completed and the user and the mating party (or the manager) start communication, the re-write operation is started. The user transmits the password necessary for re-writing the living body information as the data to the mating party.
[0119] The re-write operation of the reference living body information cannot be conducted when collation of the password does not prove coincident. In this case, the mating party (or the manager) notifies the user that the password i...
embodiment 2
[0125] [Embodiment 2]
[0126] The construction of the authentication apparatus used in the present invention and its operation will be explained next.
[0127] FIG. 7 is a block diagram of the authentication apparatus according to this embodiment. The authentication apparatus of this embodiment includes an antenna 601, a transmission / reception circuit 602, a signal processing circuit 603 for compressing / expanding signals and encoding them, a microcomputer 604 for control, a flash memory 605, operation keys 606, and so forth. The authentication apparatus further includes a sensor 611 and a collation circuit part 612.
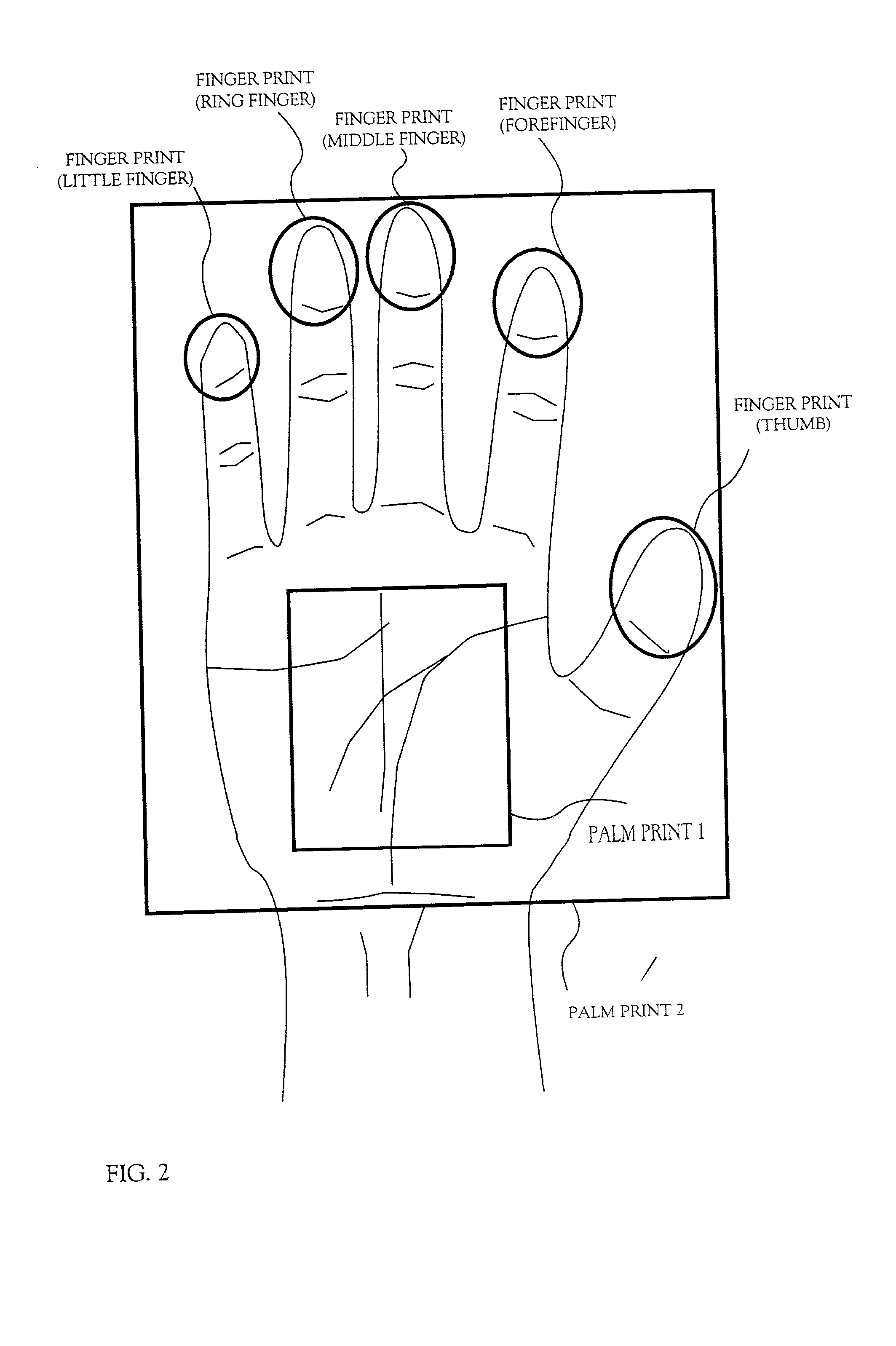
[0128] When the operation key 606 is operated, the microcomputer 604 for control controls the sensor 611 and lets it read the living body information of the user. Incidentally, this embodiment uses palm prints or fingerprints as the living body information. The living body information of the user read by the sensor 611 is inputted to the collation circuit part 612.
[0129] An A / ...
embodiment 3
[0133] [Embodiment 3]
[0134] Differences of the construction of the authentication apparatus used in this embodiment and its operation from Embodiment 1 will be explained.
[0135] FIG. 8 is a block diagram of the authentication apparatus of this embodiment. The authentication apparatus includes an antenna 501, a transmission / reception circuit 502, a signal processing circuit 503 for compressing / expanding and encoding signals, a microcomputer 504 for control, a flash memory 505 and operation keys 506. The authentication apparatus further includes a microphone 511, an amplifier 516 and a collation circuit part 512.
[0136] When the operation key 506 is operated, the microcomputer 504 for control controls the microphone 511 and lets it read the living body information of the user. Incidentally, this embodiment uses a voiceprint as the living body information. The living body information read by the microphone 511 is amplified by the amplifier 516 and is inputted to the collation circuit par...
PUM
| Property | Measurement | Unit |
|---|---|---|
| transmission | aaaaa | aaaaa |
| length | aaaaa | aaaaa |
| processing | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com