Method and system for managing confidential information
a confidential information and management method technology, applied in the field of managing confidential information, can solve the problems of exposing the organization to legal sanctions and liabilities, severe financial damage, and constant information leakage, and achieve the effect of efficient digital information management, audit and control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
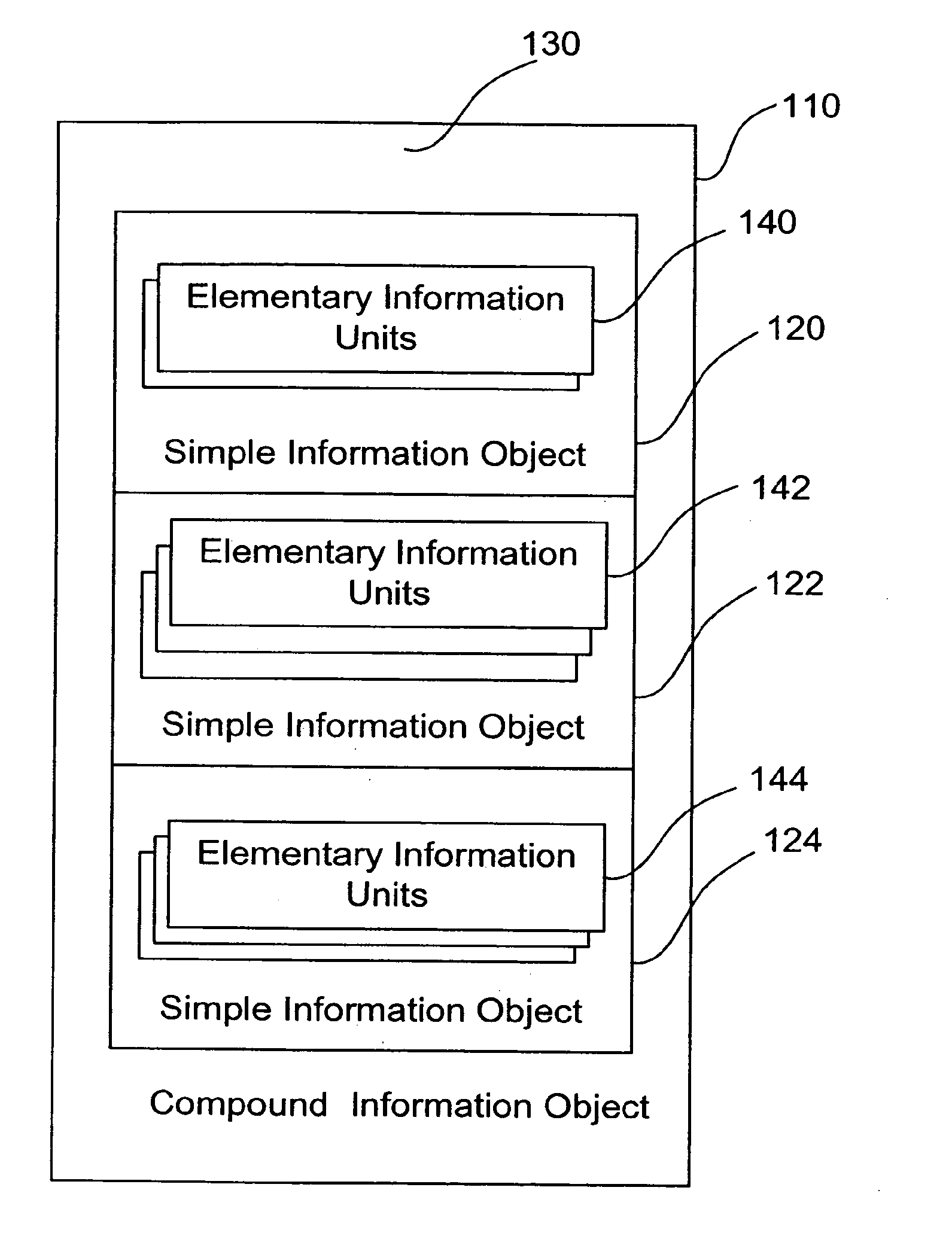
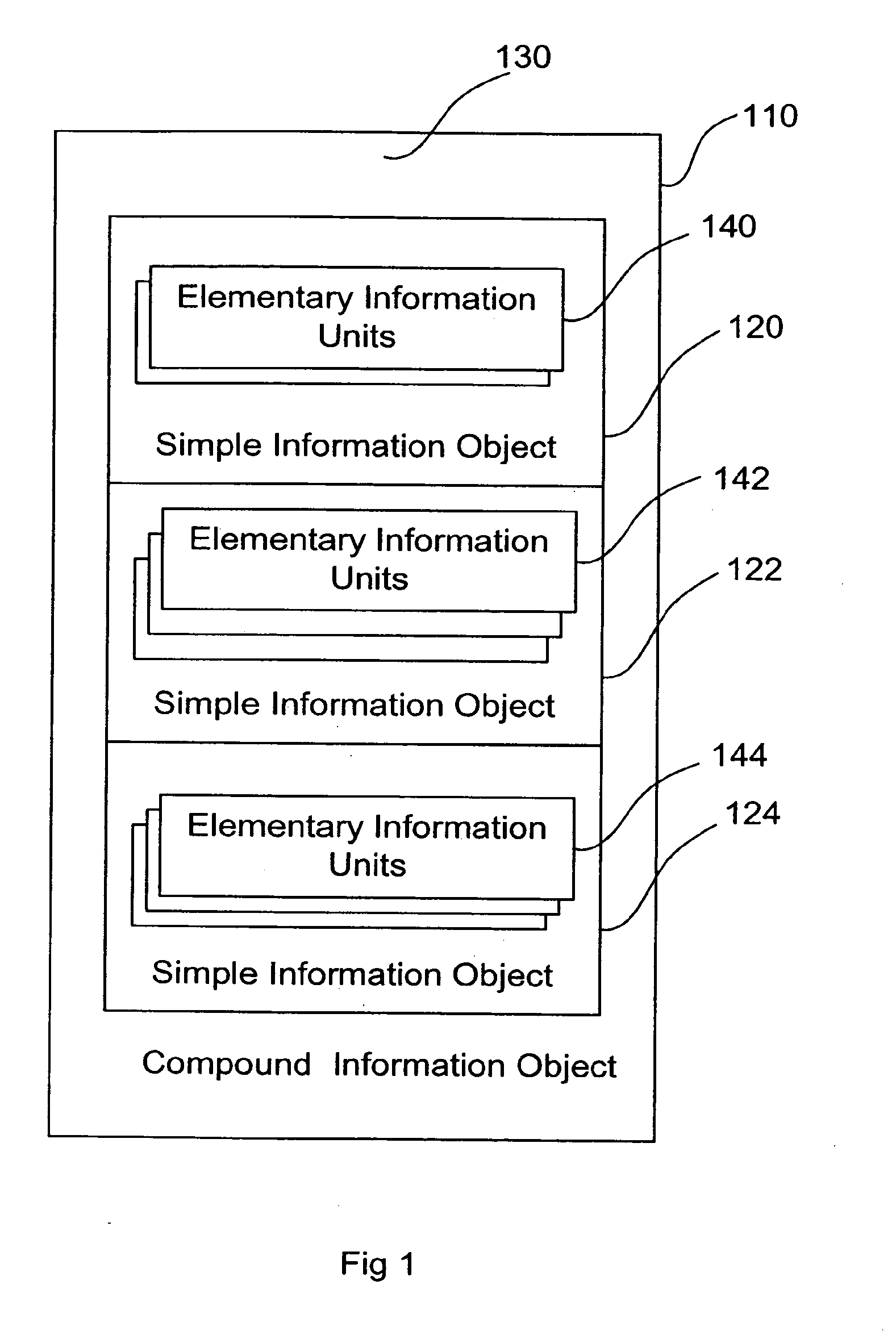
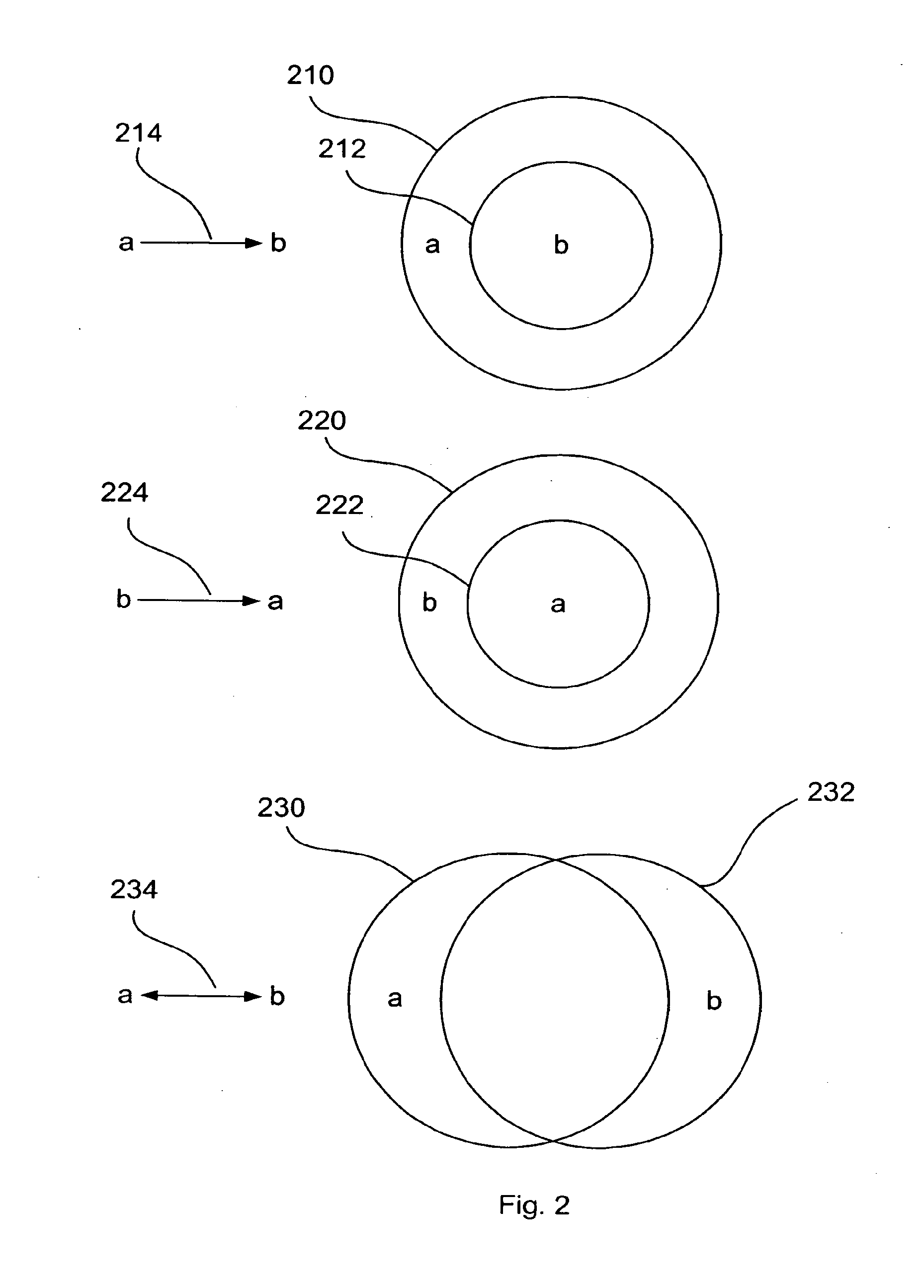
[0135]The present embodiments describe a method and system for managing confidential information. In particular, the present invention described methods for information tracking, identification, classification and management along the information lifecycle, utilizing a modular and abstract description of information.
[0136]According to embodiments, a system for information management and control is presented which uses modular and abstract descriptions of the information. The system allows for flexible and efficient policy management and enforcement, in which a policy can be defined with direct respect to the actual information content of the digital information items. The information content can be of various kinds: e.g., textual documents, numerical spreadsheets, audio and video files, pictures and images, drawings etc. The system can provide protection against information leakage independently of other information management systems.
[0137]Before explaining in detail preferred embo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com