Malware and exploit campaign detection system and method
a detection system and campaign technology, applied in the field of malware and exploit campaign detection system and method, can solve the problem of limiting the country of origin of the ip address
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
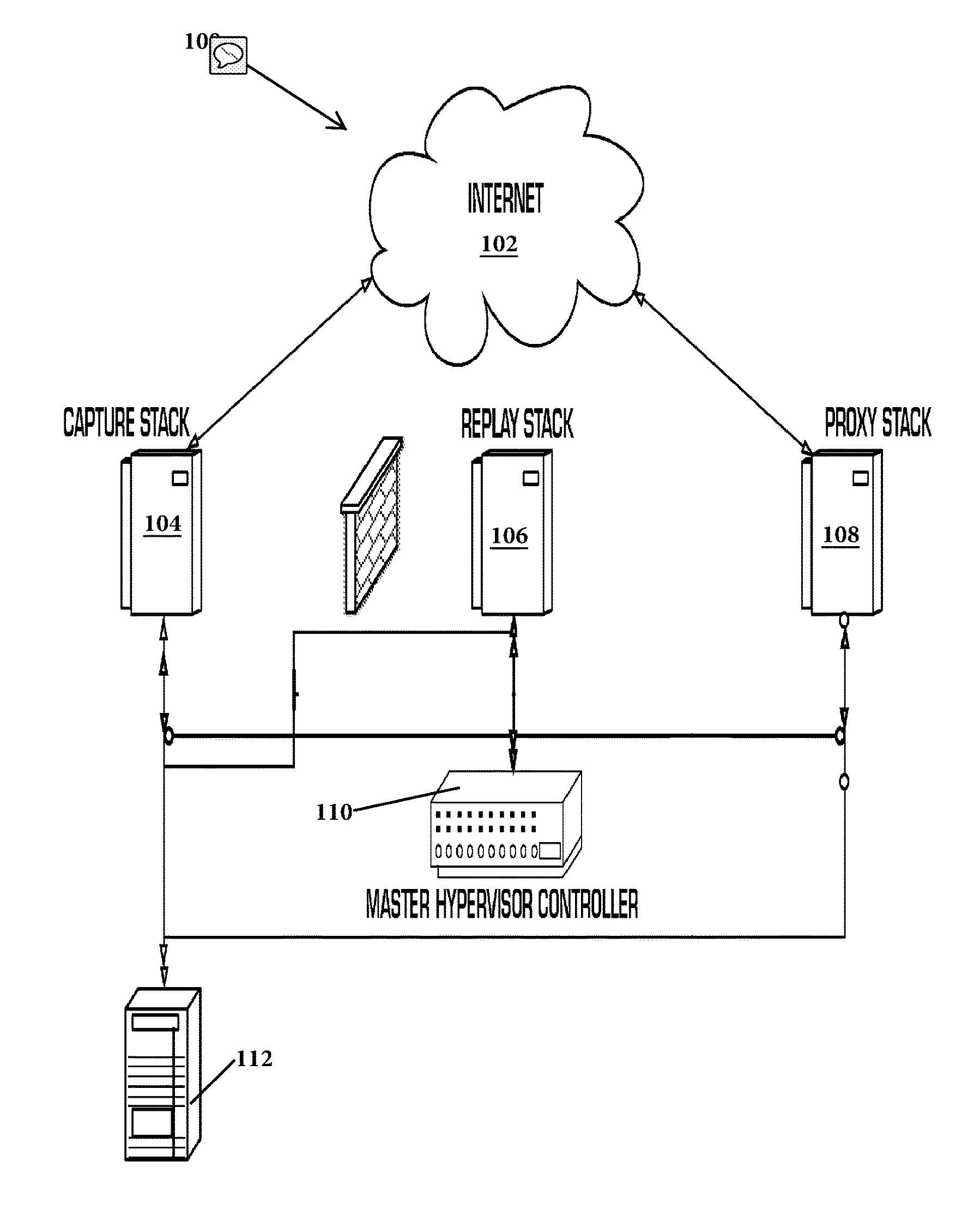
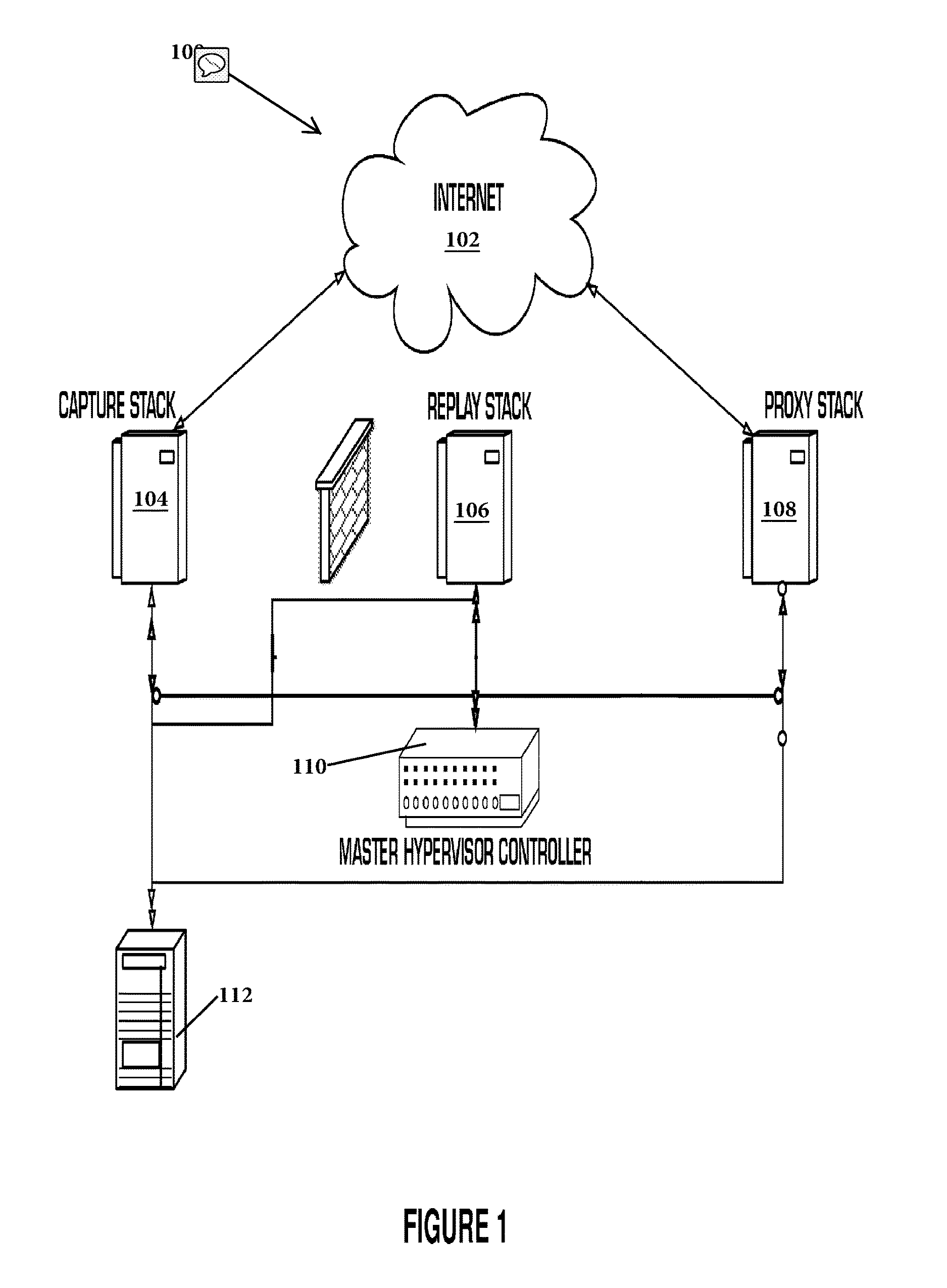
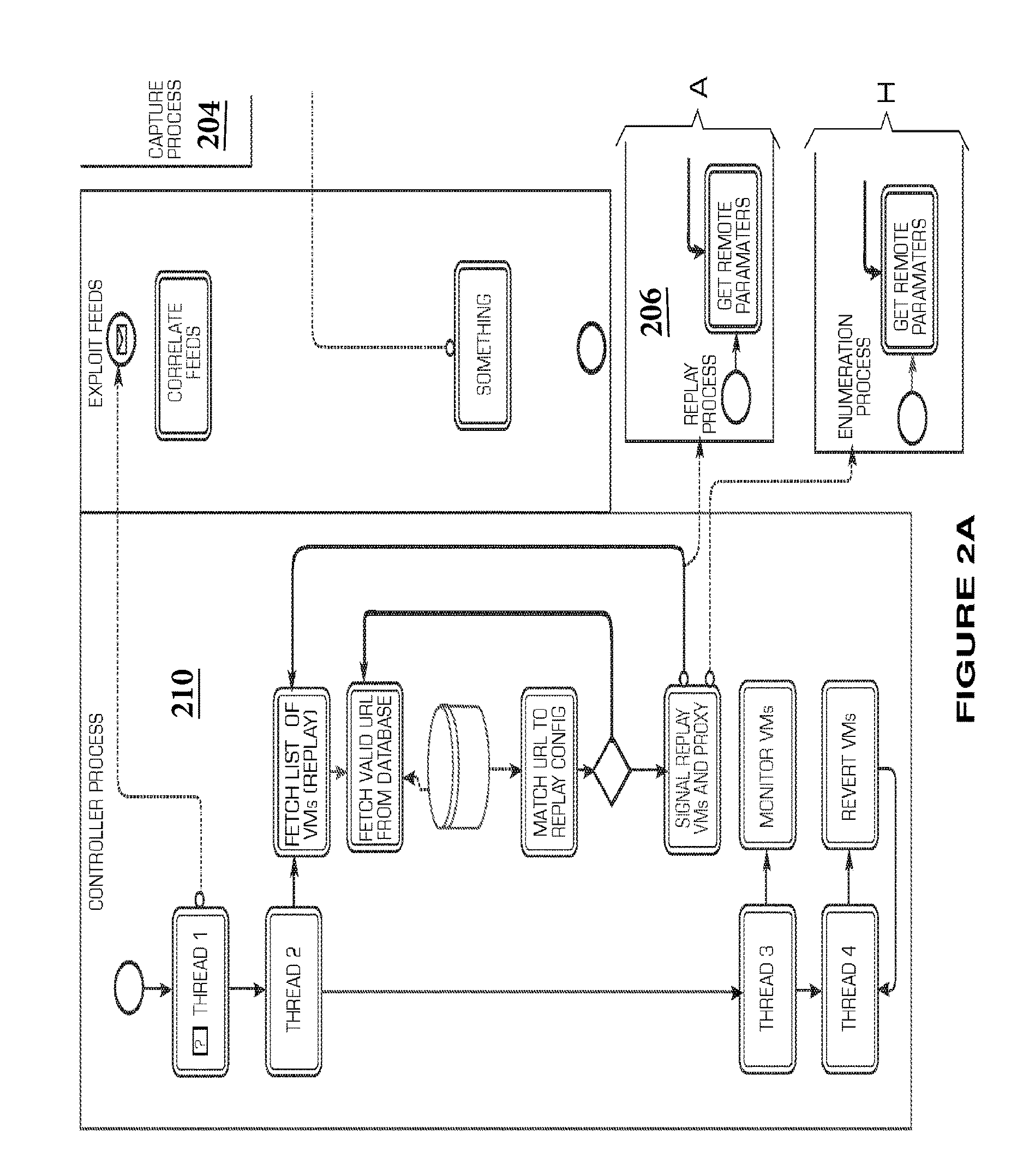
[0017]The system and method for malware and exploit campaign detection (known as BaitNET) is designed to seek out, detect, itemize, and retest active URLs serving drive-by exploits. BaitNET is a multi-leveled application operating within the kernel and user layers of the operating system that make it unique when compared to similar technologies utilized to detect and prevent malware.
[0018]Note that the distinction is important—malware is the payload that is delivered by an exploit. There are literally hundreds of thousands of malware samples in the wild, and it is a trivial matter to obfuscate these or morph them into something new. In contrast, there are only a few hundred active exploits in the wild at any given point in time—the exploit is the mechanism whereby the threat actor compromises the system in order to deliver and execute the malware. By identifying and blocking exploits, BaitNET moves further up the kill chain from traditional malware protection products and provides m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com