Rapid and verifiable network configuration repair
a network configuration and repair technology, applied in the field of computer architecture and computer security, can solve the problems of network configuration still largely manual, time-consuming and error-prone process, network outages, etc., and achieve the effect of reducing the difficulty for human reason about distributed network configuration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
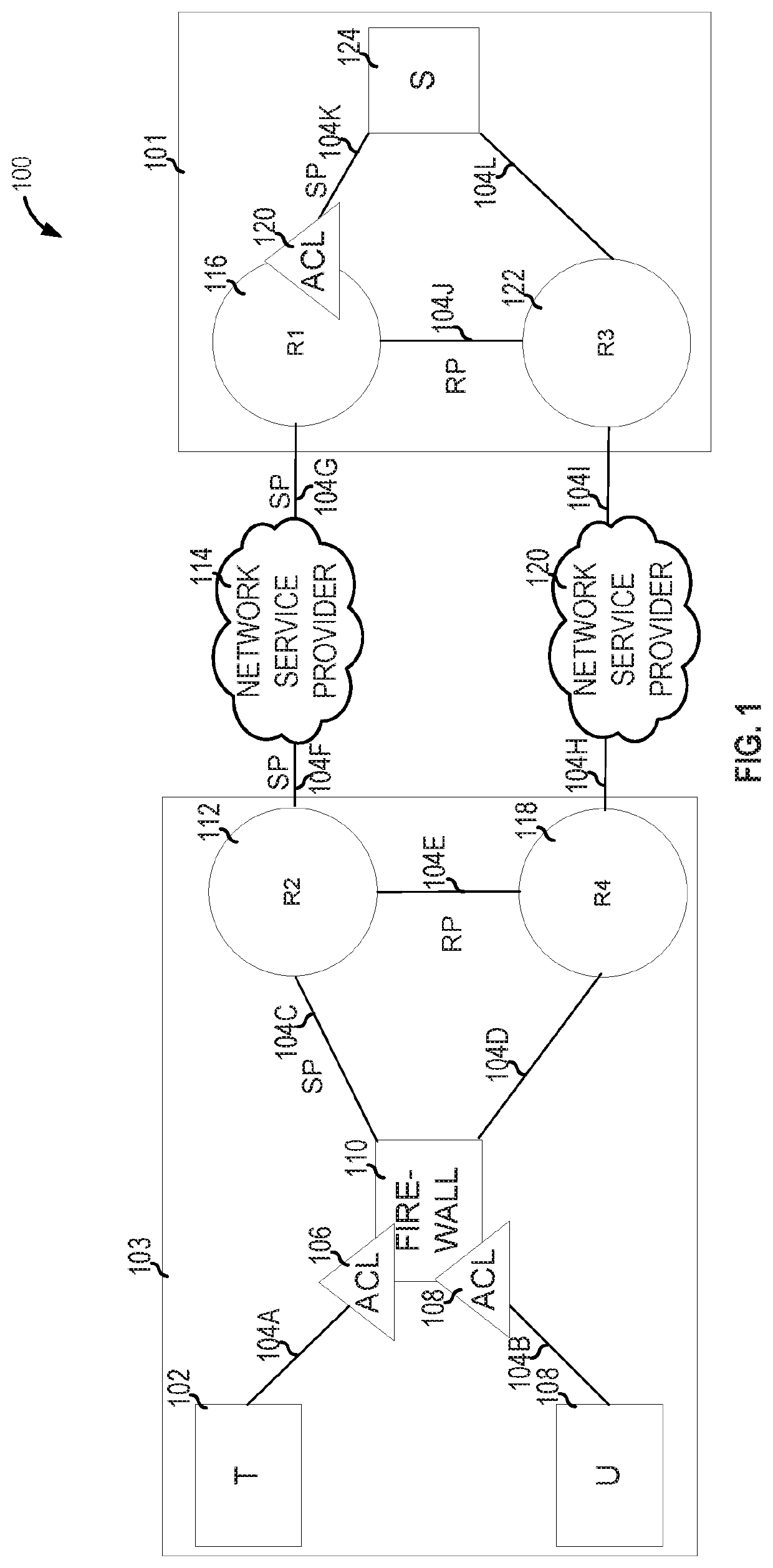
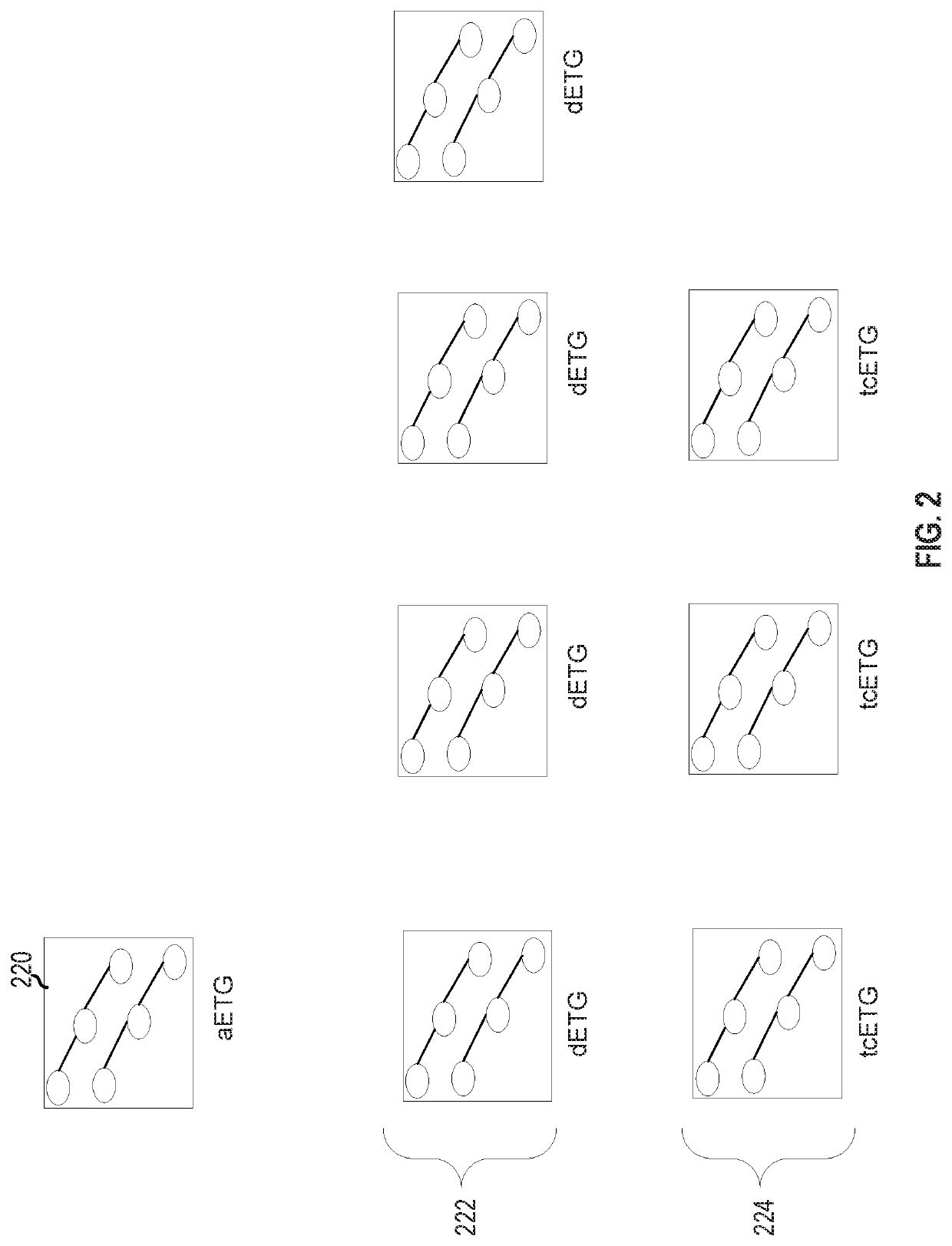
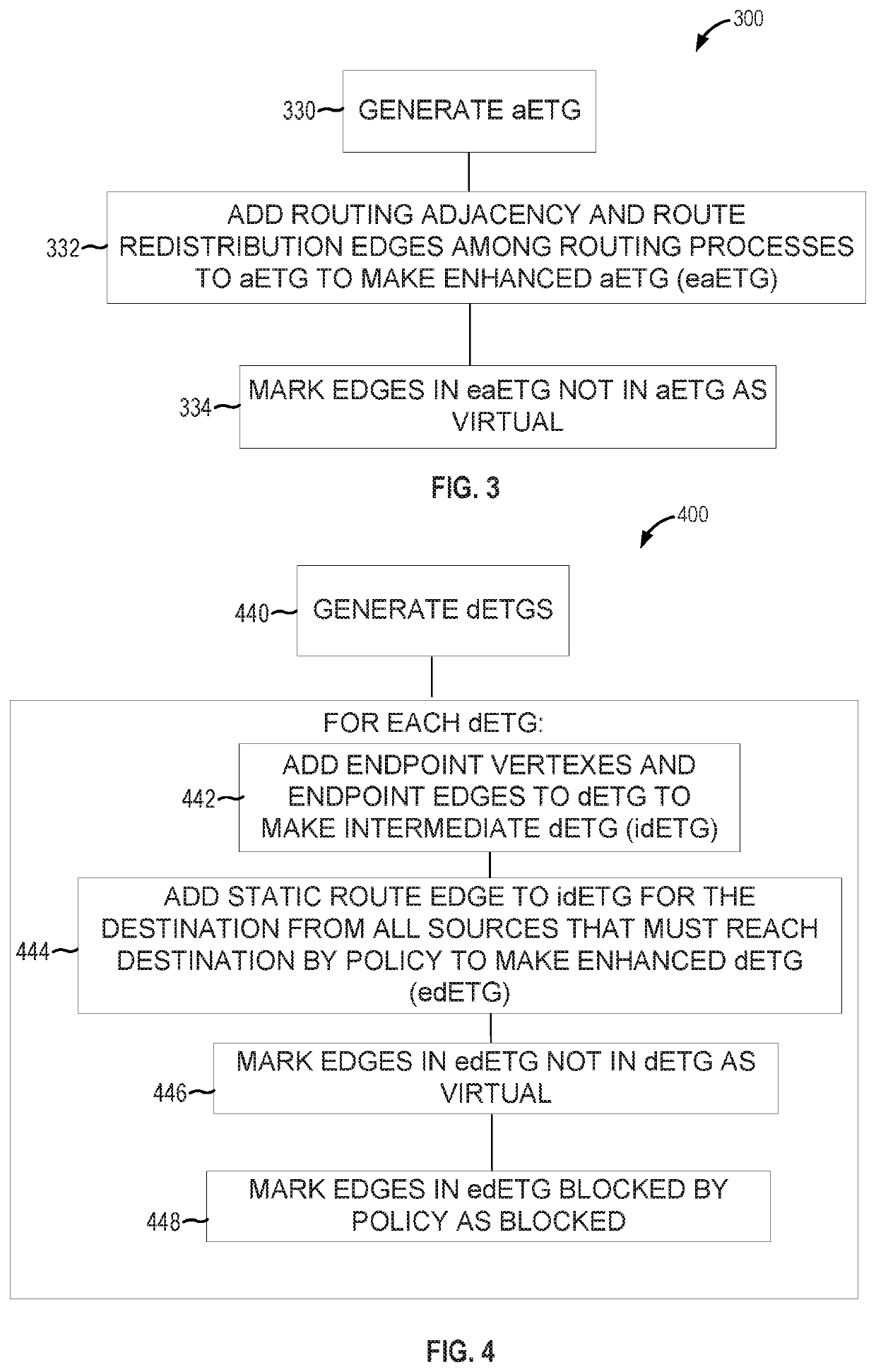
[0115 includes a network configuration repair apparatus, the apparatus comprising memory with policies, extended topology graphs (ETGs) including an all ETG (aETG), and destination ETGs (dETGs) for each policy destination in the policies, stored thereon, and processing circuitry configured to add a routing adjacency or route redistribution edge to a router of the aETG to generate an enhanced aETG (eaETG), add, for each dETG of the dETGs, static route edges to the destination of the dETG to generate an enhanced dETG (edETG), determine, for each of the edETGs, all simple paths from all sources to the destination of the edETG, determine an set of paths (pathset) over the determined simple paths that satisfies the policies, and translate the edge additions and / or removals in the eaETG and in the edETGs to one or more of an addition and / or removal of a routing adjacency, routing filter, or static routes based on the determined pathset.
[0116]In Example 2, Example 1 further includes, where...
example 11
[0125 includes a computer-implemented method for network configuration repair, the method comprising adding a routing adjacency or route redistribution edge to a router of an all extended topology graph (ETG) (aETG) to generate an enhanced aETG (eaETG), adding, for each destination ETG (dETG) of dETGs, static route edges to a destination of the dETG to generate an enhanced dETG (edETG), determining, for each of the edETGs, all simple paths from all sources to the destination of the edETG, determining a set of paths (pathset) over the determined simple paths that satisfies the policies, and translating the edge additions and / or removals in the eaETG and in the edETGs to one or more of an addition and / or removal of a routing adjacency, routing filter, or static route based on the determined pathset.
[0126]In Example 12, Example 11 further includes marking as virtual the added routing adjacency or route redistribution edge of the eaETG.
[0127]In Example 13, Example 12 further includes ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com