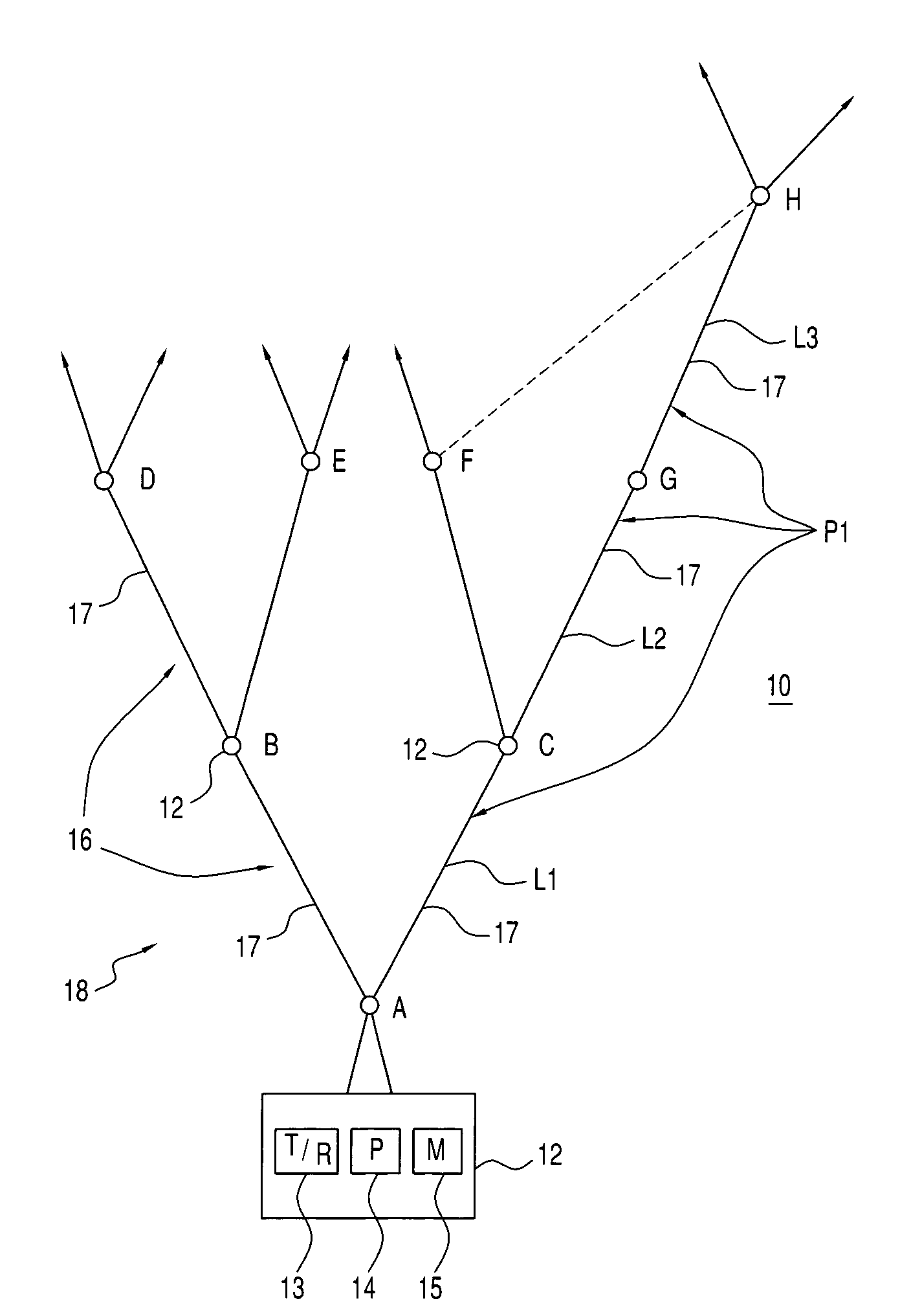
Independent-tree ad hoc multicast routing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
[0049]E1=Set of all edges in a graph G and I is the family of subsets of E satisfying the condition that none of them contains a circuit of the graph. Hence independent subsets of this graph are all subsets of trees on this graph.
example 2
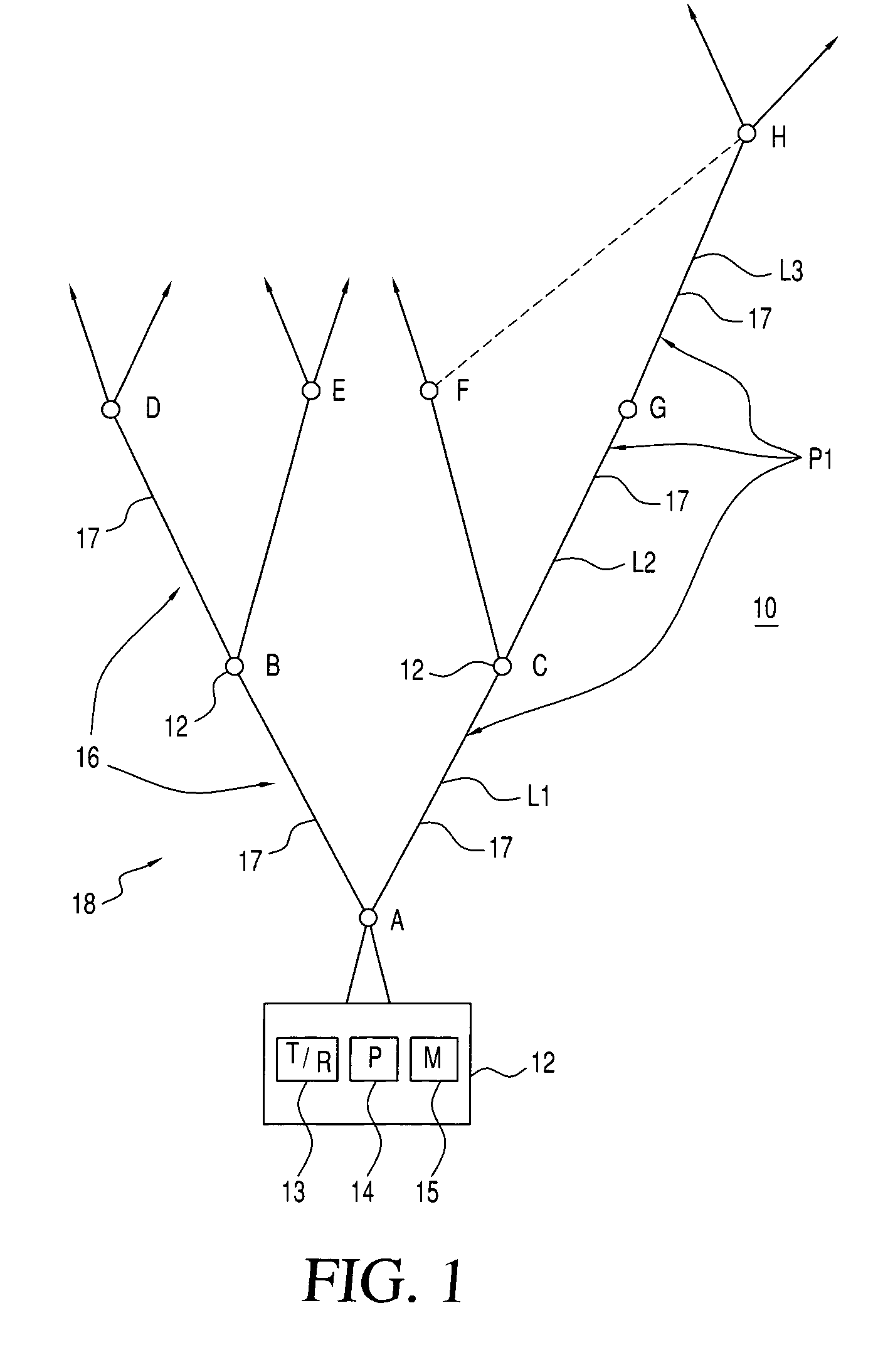
[0050]E=Set of all edges in graphs G and G′ (see FIG. 2) where G′ is a copy of G (edge e′1 is a copy of e1 and so on). Two matroids which can be defined on this set are:
[0051]M1=(E, I1) where an “independent” set is a union of subsets of trees of G and G′. For example, an independent set in the collection I1, could be {e1, e2, e3, e4, e′5, e′6, e′7, e′2} and a set which would not belong to I2 would be {e1, e2, e7, e′8} since it has a circuit in it.}
[0052]M2=(E, I2) where an “independent” set is one which does not have both copies of any of the edges. An example of an independent set in I2 would be {e1, e′3, e′7} and a set which would not belong to I2 would be {e1, e′3, e′1} since it contains both copies of e1.
[0053]Hence if a subset of E belongs to both Matroids defined above, it will have to be a union of 2 trees, one in G and the other in G′. Moreover, the copy of an edge that belongs to the tree in G should not belong to the tree in G′. This observation indicates that when 2 edge...
example
[0069]Consider the graph G in FIG. 2. The problem is to find two disjoint spanning trees. First, it needs to be verified that this is possible. This is easily done by trying different combinations of 4 edges each; four edges are needed to form a tree for a graph with 4 nodes. One example would be {e1, e3, e5, e7} and {e2, e4, e6, e8}.
[0070]The effectiveness of arriving at a pair of disjoint trees using the Matroid Intersection Algorithm can be seen by going through the process for this simple graph. Suppose one starts by building just a tree T1 first and then removing links of T1 from the set of edges and then trying to build another tree T2. The following two sets would be obtained (see FIG. 4):[0071]T1={e1, e2, e3, e4}[0072]T2={e5, e6, e7}
[0073]Adding e′8 to T2 will create a circuit and hence is not acceptable. Now one would like to move some edges from T1 to T2 and add some new ones to T1, so that it still remains a tree.
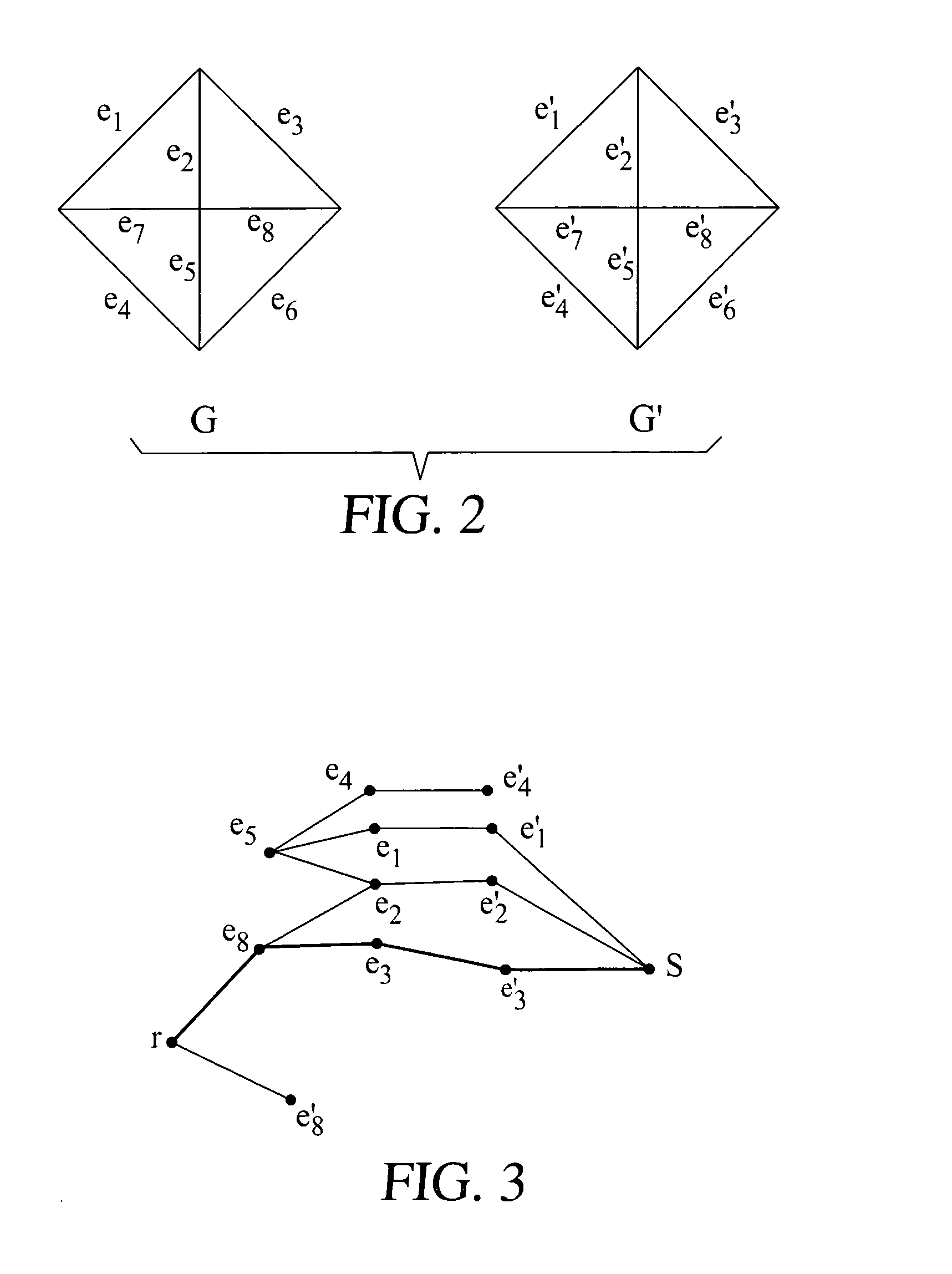
[0074]Constructing an auxiliary digraph G′ (see FIG. 3) hel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com