Remote authentication and transaction signatures
a transaction signature and remote authentication technology, applied in public key infrastructure trust models, instruments, data processing applications, etc., can solve the problems of complex public key infrastructure, insufficient static passwords, and high cost when compared to competing security technologies, and achieve the effect of reducing the cost of public key infrastructure, and increasing the complexity of public key infrastructur
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
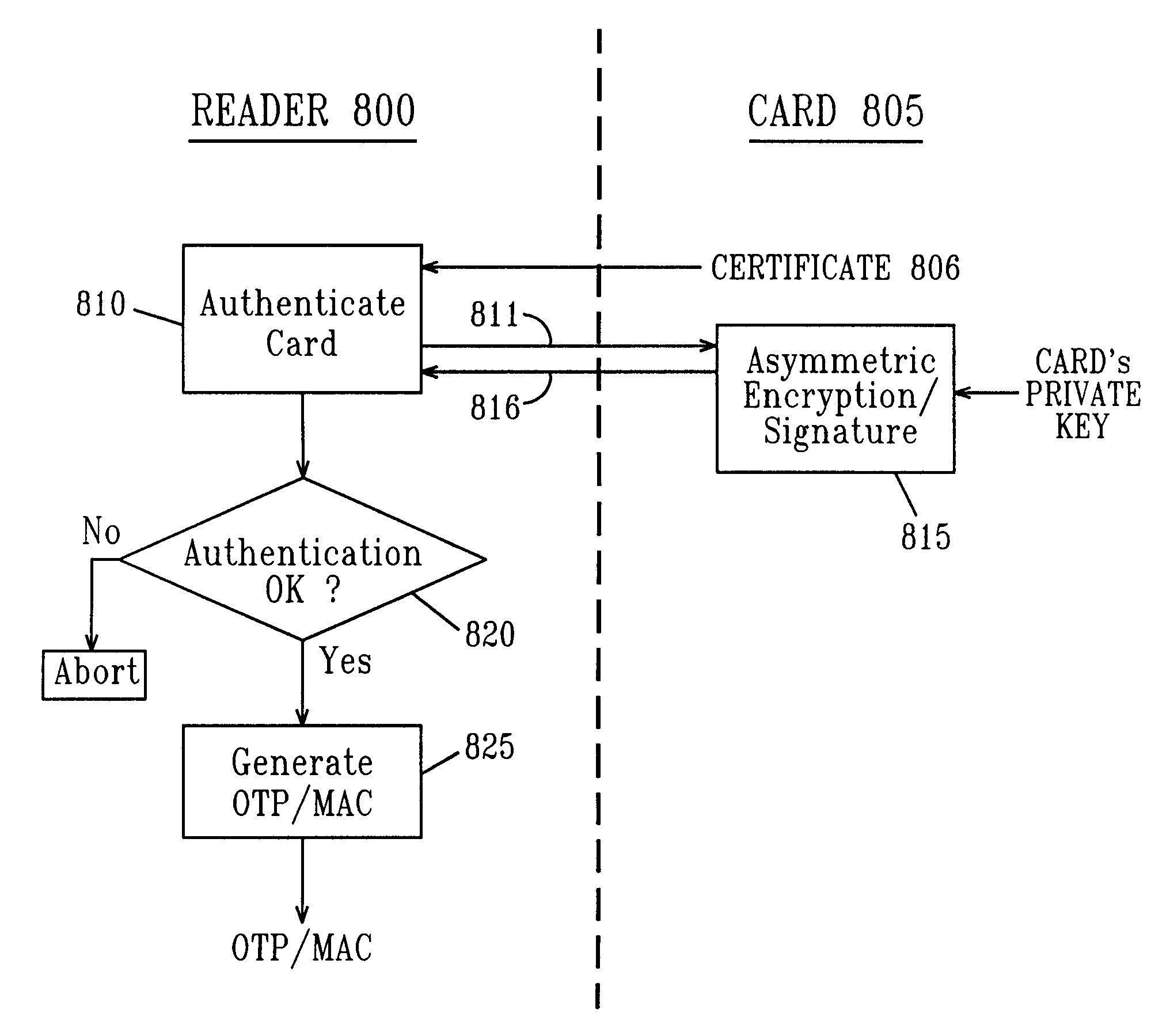
[0129]Important components of embodiments of the invention are illustrated in FIG. 12 as including a smart card reader 20 (or simply reader) and an authentication server 30 (or simply server).
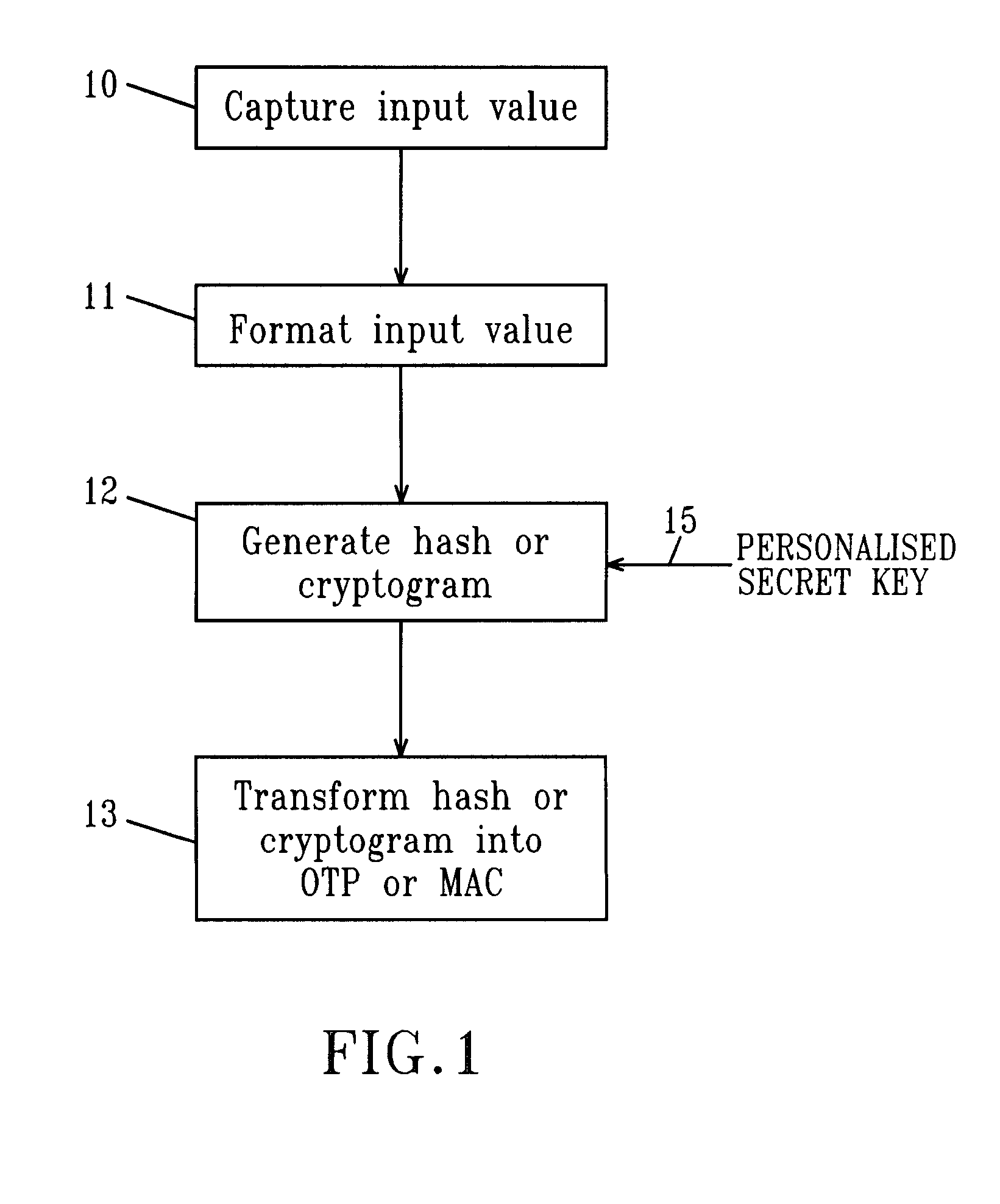
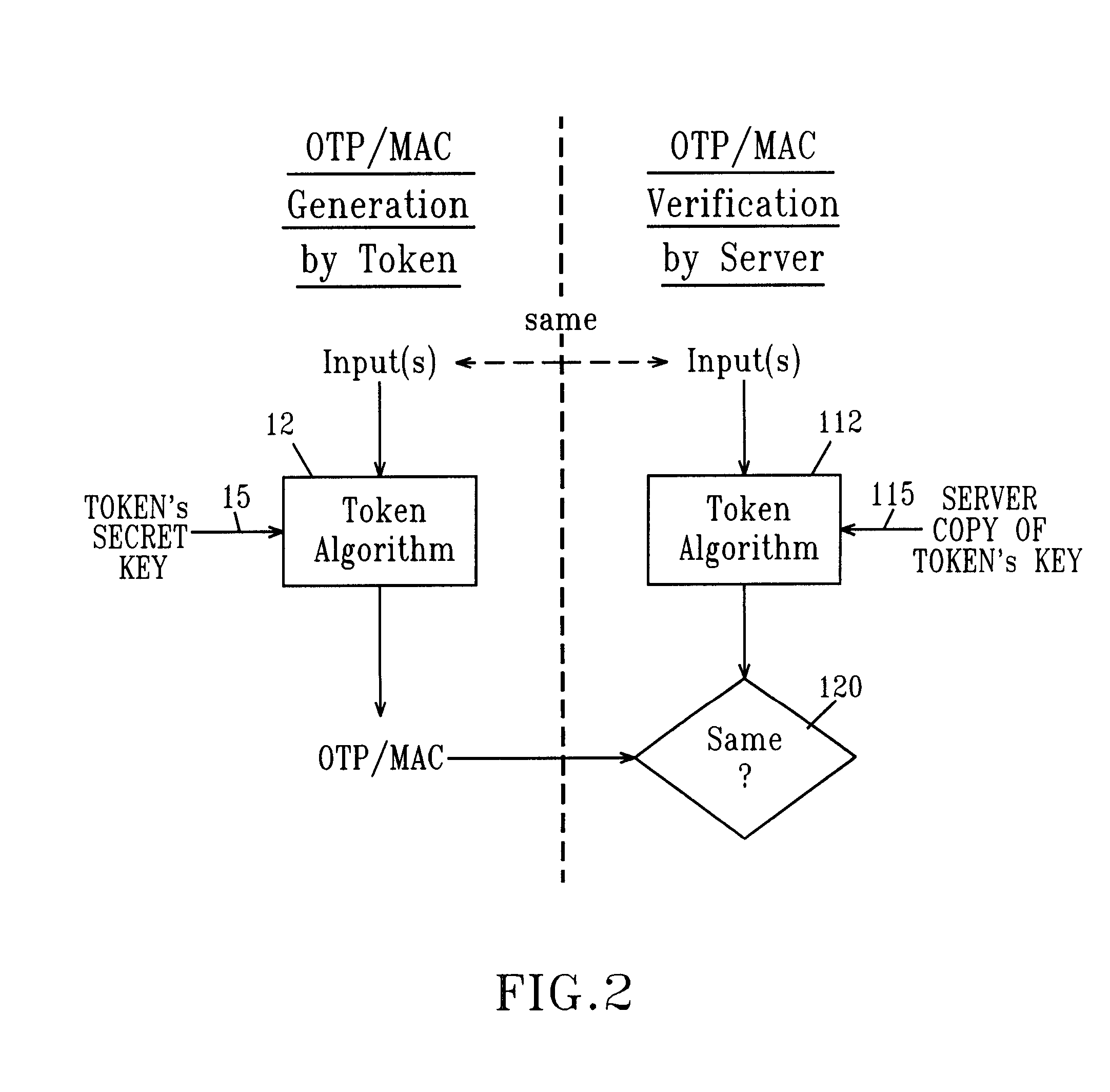
[0130]At a minimum the reader 20 includes an interface 28 to accept a smart card and a power supply 27. Some readers also include one or more user operable buttons or keys; this is represented in FIG. 12 by the keyboard 25. As used herein a user inserts a smart card into the smart card interface 28. As a consequence of some operation carried out by the reader 20, information is generated by the reader. That information may be a One-Time Password (OTP). If transaction data is input to the reader the information which is generated may include a signature such as a MAC. The output information may be presented on a display, such as the display 26. Alternatively the reader may be digitally connected to a network. In that event the information may be presented to another entity also connected to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com