System and method for providing unified transport and security protocols
a technology of unified transport and security protocols, applied in the direction of program control, unauthorized memory use protection, instruments, etc., can solve the problems that udp generally does not provide the reliability and ordering guarantees provided by protocols, and achieves superior security in internet protocol security, avoid packet loss, and reduce computational overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
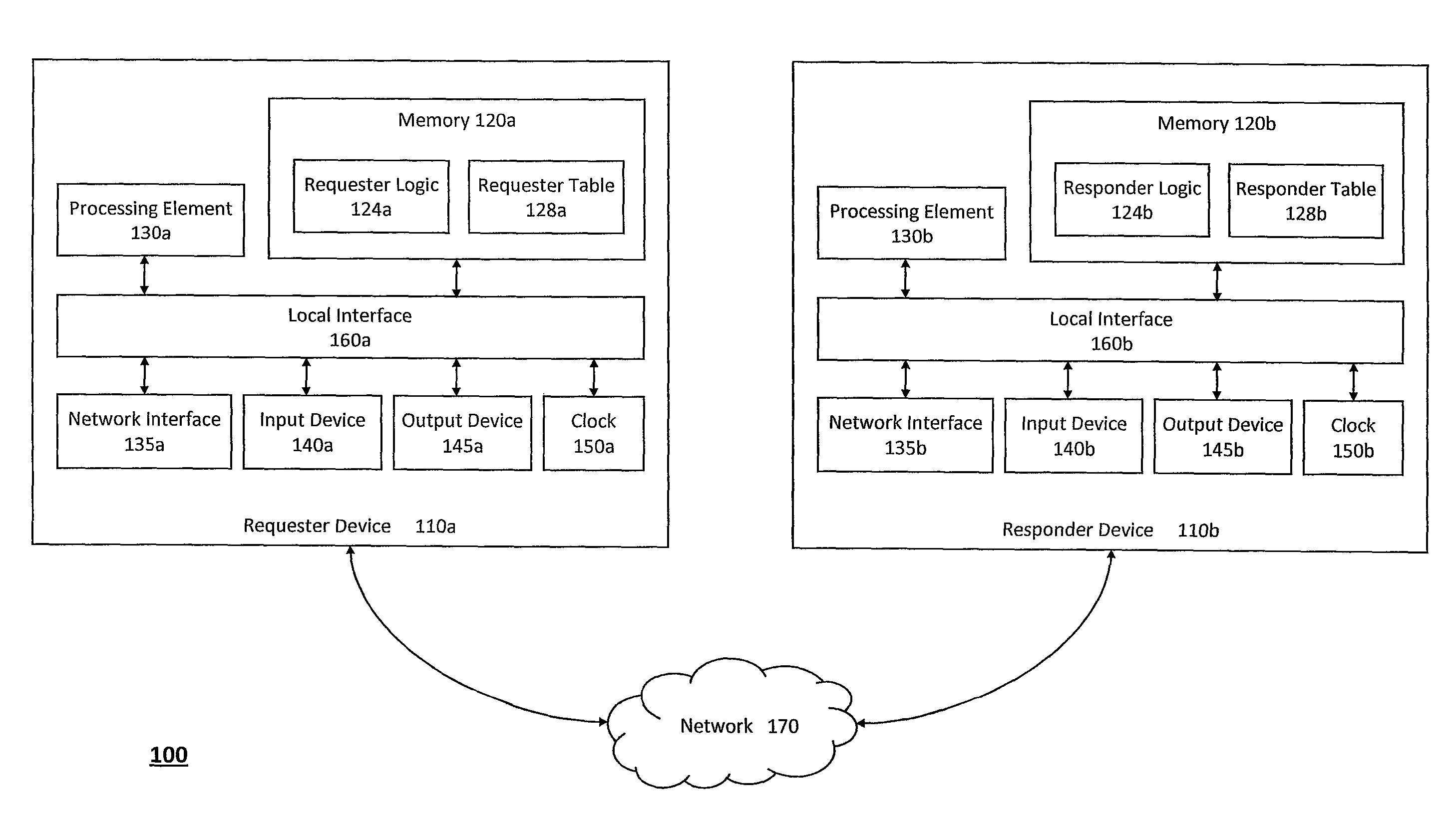
[0038]According to one aspect of the invention, FIG. 1 illustrates an exemplary system 100 for providing unified transport and security protocols to prevent denial of service attacks. In particular, the present disclosure generally pertains to a transport and security protocol that provides an identity based and privacy protected access control filter that can counter denial of service (DoS) and distributed denial of service (DDos) attacks. In one implementation, the transport and security protocol described in further detail herein may be considered stateless because the system 100 employing the transport and security protocol does not create a state for an authentication request unless the system 100 determines that the authentication request originates from a legitimate user. Moreover, the transport and security protocol can be considered stateless for both a client device and an authentication server because both the client device and the authentication server can use the transp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com