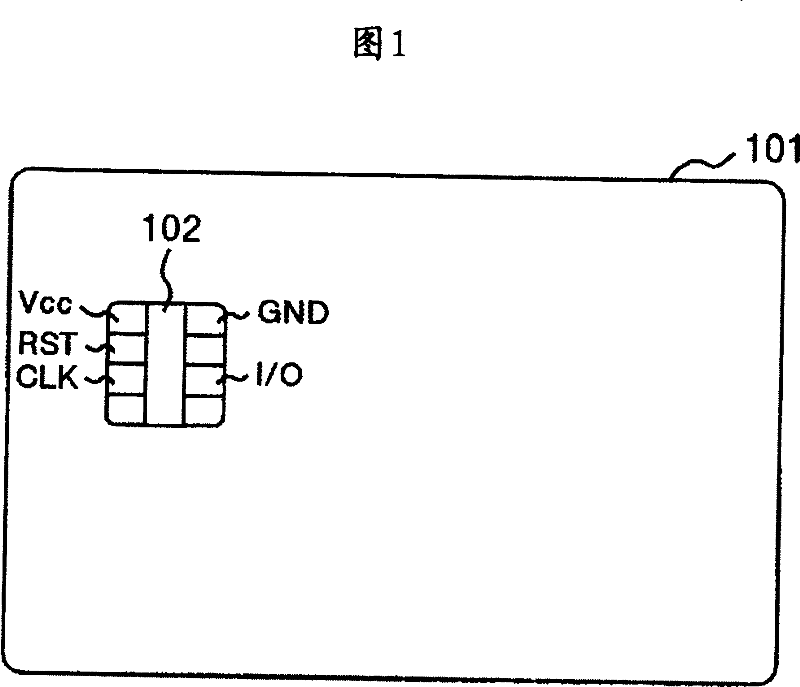
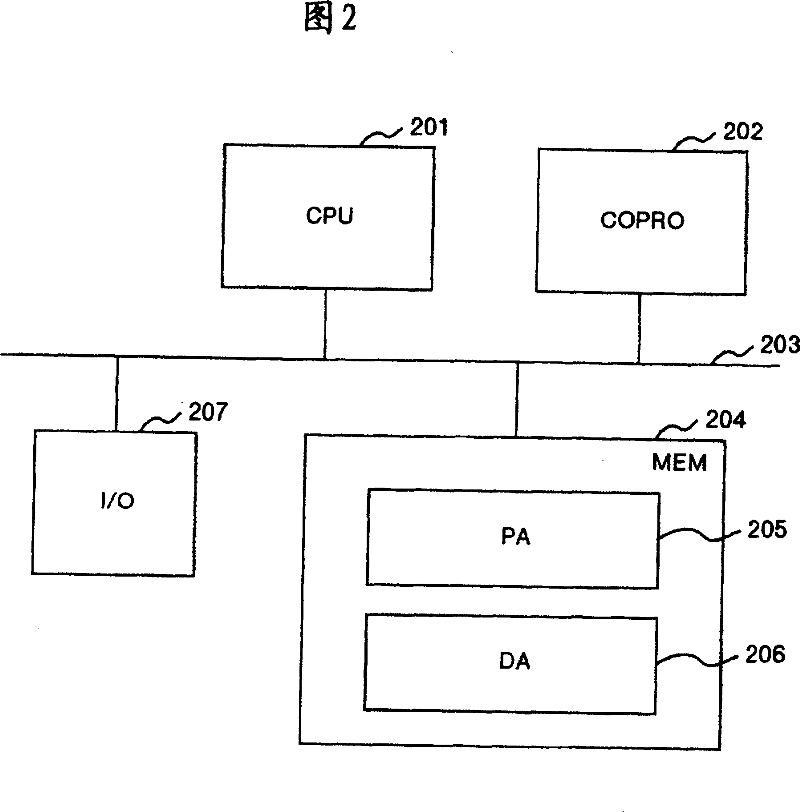
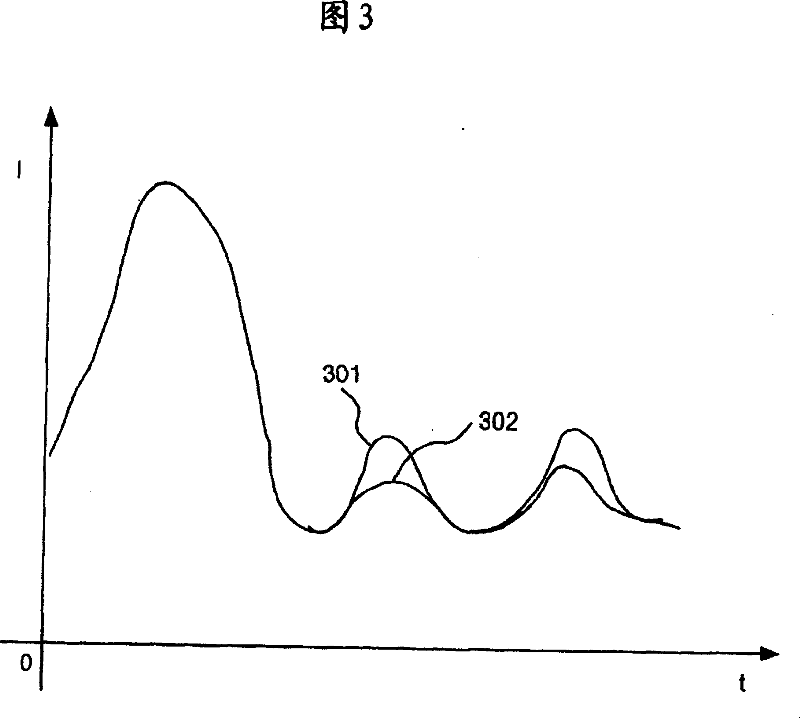
Information processing unit
一种信息处理装置、生成装置的技术,应用在安全通信装置、电数字数据处理、用编码识别卡或信贷卡片的启动等方向,能够解决相关性低、分析攻击困难等问题,达到提高攻击、提高抵抗的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0130] First, an embodiment of mapping a physical address according to (Formula 1) and its operation will be described using FIGS. 4, 5, and 6. FIG.
[0131] First, show the simplest M=2 m An embodiment of the occasion of the form of (2 to the m power).
[0132] The embodiment of the present invention shown in FIG. 4 is composed of the following parts. That is to say, its structure includes a buffer 401 for program counting, a random number generator 402, a buffer 403 for random numbers, an adder 404, and storage 2 m - Buffer (PC) 405 of I=M-1 (m 1s are arranged in parallel in binary representation), circuit 406 for calculating logical product (logical AND), physical address buffer 407, and whether the position of the program counter is determined to be in the specified area The decision circuit 408 , the selector 409 , the zero buffer 410 , the start address buffer 411 , the subtractor 412 and the end address buffer 413 . Here, the value 0 is stored in the zero buffer. Si...
Embodiment 2
[0144] The following describes an embodiment in which the simplest scrambling effect in the correspondence between physical addresses and logical addresses is high. Assume that the number of bits of the address is n. Usually, memory differs by the high order bits of the address. In this embodiment, for the sake of simplicity, it is assumed that the entire RAM area is an area in which the most significant bit is 1. That is, the RAM area has 2 n-1 Bit-sized regions.
[0145] This embodiment consists of the following parts. That is, a buffer 701 for program counting, a random number generator 702, a buffer 703 for random numbers, a judging circuit 704 for judging whether the position of the program counter is in a specified area, a selector 705, a zero buffer 706, and a circuit for calculating an exclusive OR value circuit 707 and physical address buffer 708 . Here, the value 0 is stored in the zero buffer. Since this is a fixed value, it doesn't need to be a register, for ...
Embodiment 3
[0150] In the present invention, security can be further improved by using a combination of configuration data and a technique of changing the address to a certain value. For example, it can be considered that by applying the method of the present invention to the area that becomes the target of DPA attack in RAM, for the part that becomes the target of the attack method that directly observes and extracts internal information without using statistical methods, the data is allocated so that the address As long as the change is fixed, a wider range of internal data can be safely processed, and security can be improved.
[0151] This embodiment, for example, is as follows.
[0152] Currently, the address of the RAM area is from C000 to CFFF in hexadecimal notation. Next, in the extended example of M shown in Embodiment 1 above, an information processing apparatus applied to the area from C900 to CFFF will be considered. Under this condition, consider the following procedure. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com