Embed and detection method for identifying water mark, its system and uses
A technology for authentication watermarking and authentication methods, applied in image data processing, instruments, image data processing, etc., can solve the problems of authentication failure, inability to resist lossy compression of digital images, and dependence on image compression formats.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] Below in conjunction with accompanying drawing, the present invention will be further described
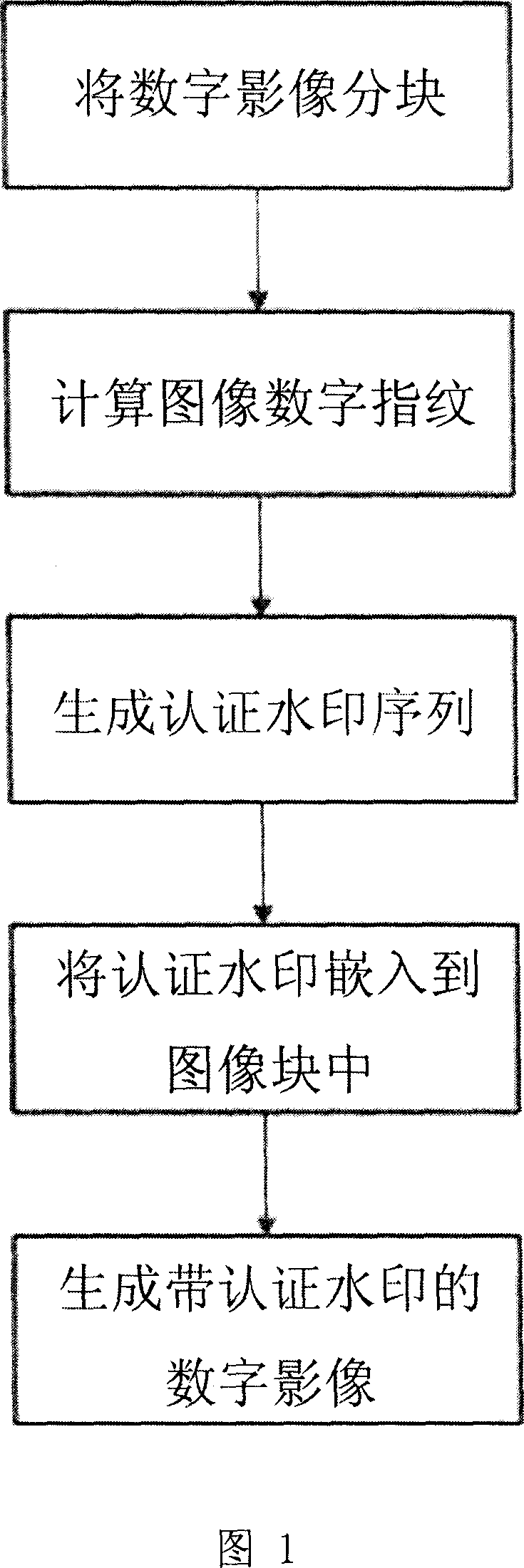
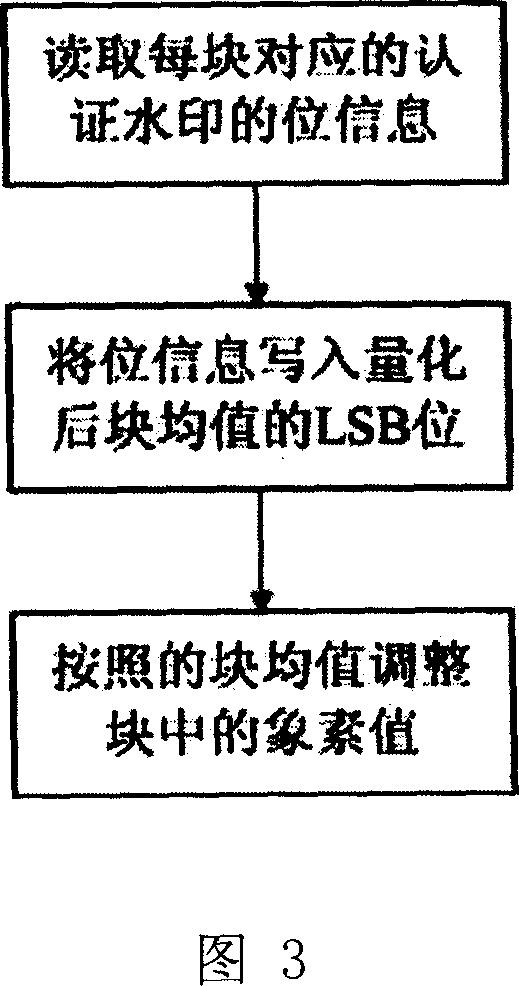
[0060] Figure 1 is a schematic diagram of the embedding process of the authentication method watermark. This process mainly involves two processes, namely, the calculation process of the digital fingerprint and the embedding process of the digital fingerprint. The specific implementation process is as follows: first divide the input digital image into blocks, calculate the digital fingerprint of the image, generate the authentication watermark sequence, and then embed the information of the authentication watermark into the image block to generate the digital image with the authentication watermark.
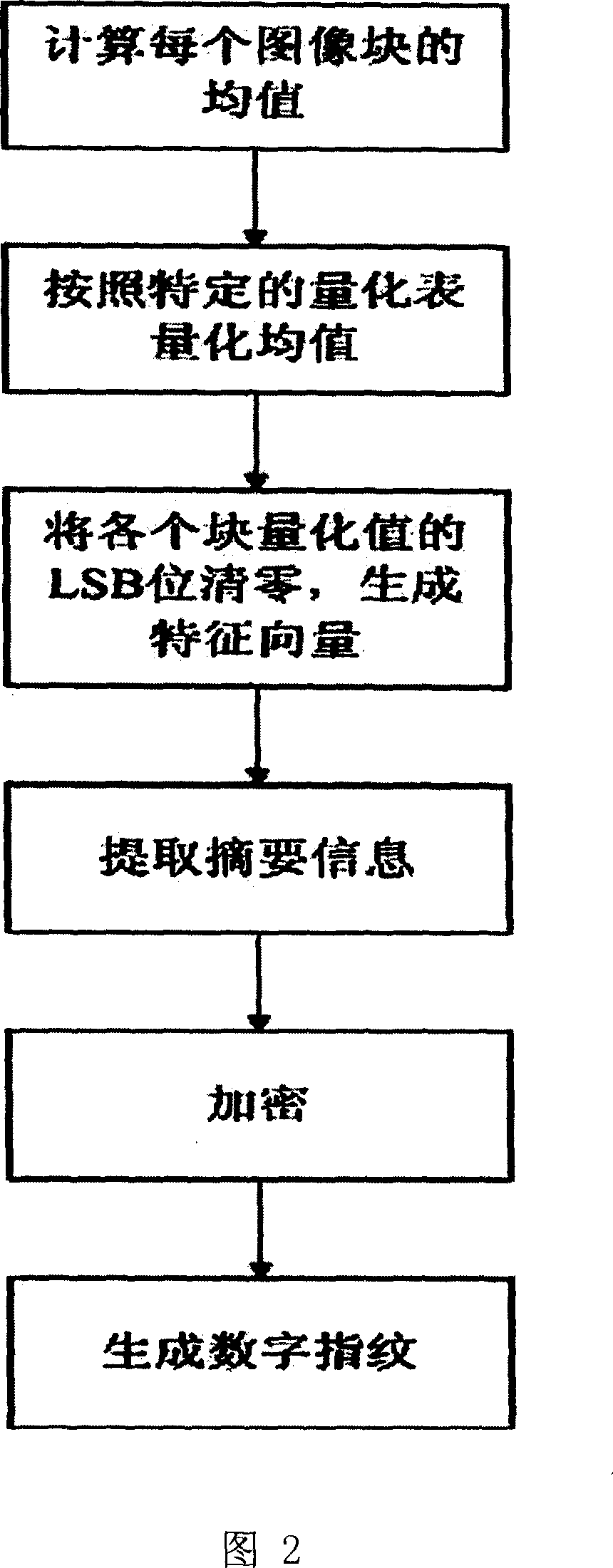
[0061] Fig. 2 shows the calculation process of the digital fingerprint in the embedding process of the authentication method watermark mentioned above. The specific implementation process includes: 1. Calculate the mean value of each image block; 2. Quantize the mean value ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com