Electronic authentication method and electronic authentication system
A verification system and electronic technology, applied in the field of illegal activities, can solve problems such as inability to ensure, inconvenient, and inability to determine the legitimacy of access to various devices, and achieve the effect of eliminating access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] Hereinafter, the best mode for carrying out the invention (hereinafter, referred to as an embodiment) will be described in detail with reference to the accompanying drawings.
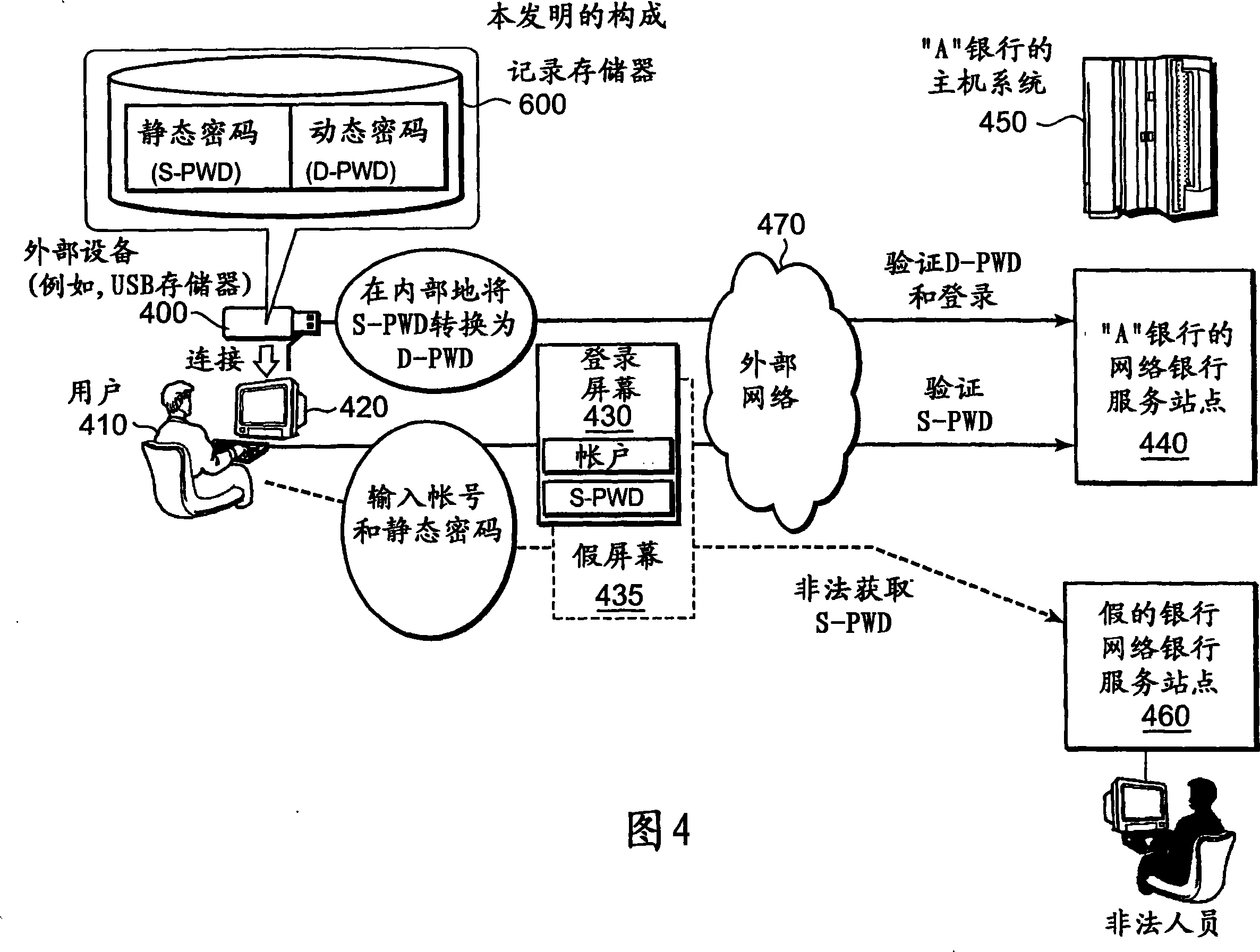
[0057] FIG. 4 illustrates the relationship among physical devices, users, and actions performed by unauthorized persons in an authentication method according to an embodiment of the present invention.
[0058] As shown in FIG. 4 , the usage example of the online banking service used by the user 410 includes: an external device 400 owned by the user, a communication terminal 420 to which the external device 400 is attached, and a communication terminal 420 communicatively connected via an external network 470 to the host computer 450 of Bank "A". User 410 may access host computer 450 from "A" bank's Internet banking site 440 . The external device 400 includes a recording memory 600 . The recording memory 600 is a nonvolatile memory unit. The external device 400 may also include an arithmetic un...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com