Safe network trading method
An online transaction and transaction technology, applied in the field of financial services, can solve the problems of limiting the scope of online transactions for customers, restricting the development of online transactions, and being difficult for customers to adopt, etc., to achieve the effect of wide transaction scope, easy promotion and development.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0015] A secure network transaction method, which consists of: transaction preparation, transaction authorization and transaction implementation, the transaction preparation, transaction authorization and transaction implementation are presented in a relationship and have an effect on the overall result, and the transaction preparation: the process mainly completes Bind the customer's bank account with the customer's mobile phone number. The customer can go to the bank counter or through the Internet to bind the customer's bank account and the customer's mobile phone number. At the same time, the customer must reserve an identity verification password to confirm the sender of the mobile phone message In order to simplify operations, prevent mistakes, and reduce management costs, it is best for a mobile phone to correspond to a bank account in a bank;
[0016] The above-mentioned transaction authorization: This process is mainly to allow customers to independently complete the r...
Embodiment 2
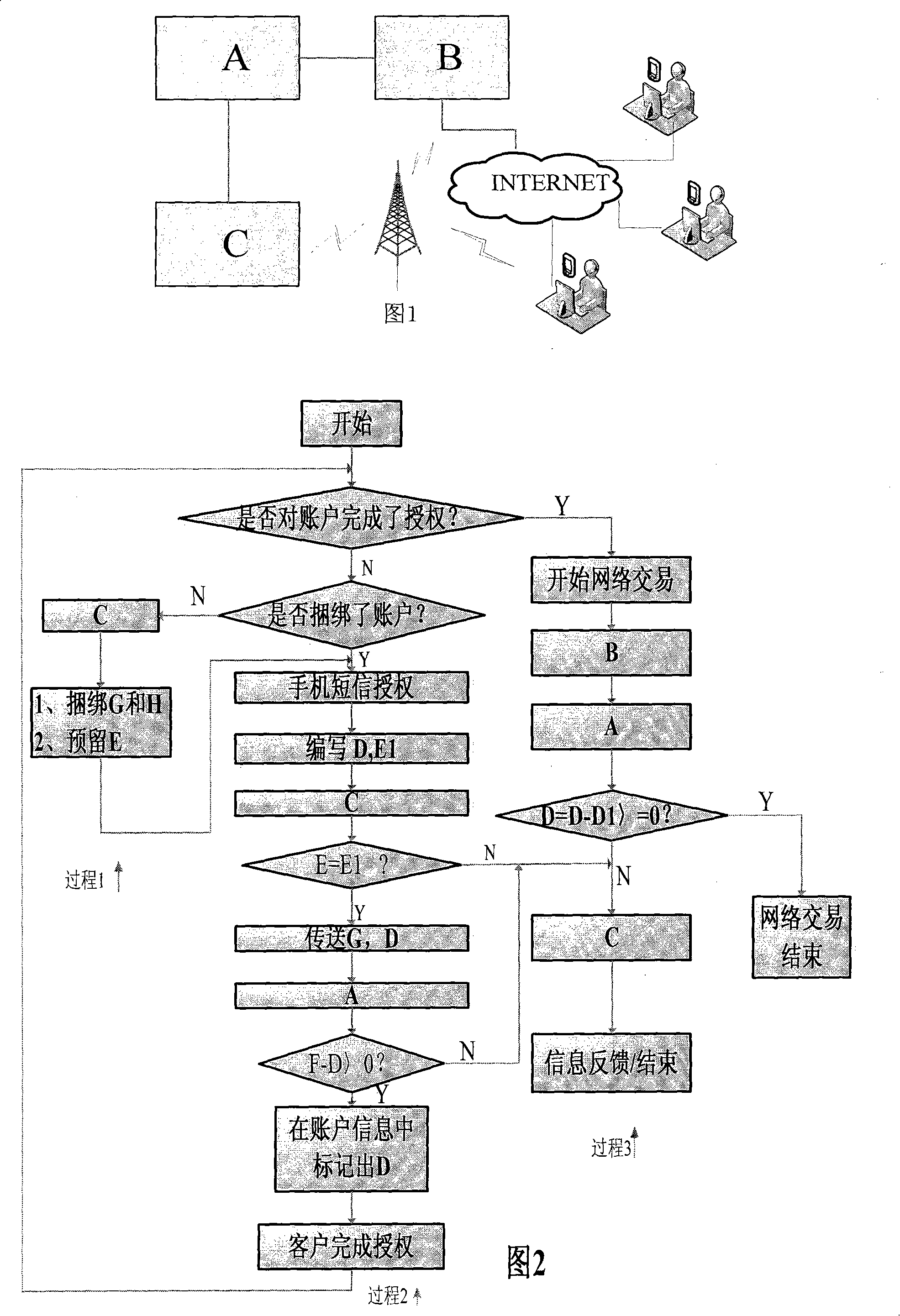
[0020] The safe network transaction method described in embodiment 1, Fig. 2 is the connection schematic diagram of each relevant system platform of the present invention, A is the bank's existing comprehensive business system, only completes the maximum amount of network transaction to the account and carries out registration, monitoring and restriction B is the existing network trading platform of the bank, which does not change in the present invention; C is then a short message service platform made up of a server, software for managing customer data, local area network interface and wireless connection / transmitting module, and it has completed Two functions, one is to complete the binding of the customer account with the customer's mobile phone number, and the other is to complete the functions of receiving customer information, transmitting information and sending information. A is connected to B and C through the bank's internal LAN, and one end of B is also connected to...
Embodiment 3
[0022] For the secure network transaction method described in Embodiment 1, FIG. 1 is an operation flow chart of the present invention, marking the execution flow of the present invention.
[0023] Transaction preparation: the customer goes to the bank counter or binds the mobile phone number H and the online transaction account G on the SMS service platform C through the Internet. At the same time, in order to ensure the security of the transaction, the customer needs to provide a 6-8 E is also reserved in the short message service platform C, and the customer's mobile phone number H, online transaction account G and mobile phone identity verification password E form an interrelated data information chain.
[0024] Transaction authorization: before conducting online transactions, the customer first sends the authorization amount D and E1 to C through the mobile phone. E1 is the identity verification password during the transaction. C first completes the ratio of E and E1 accor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com