Illegal wireless traffic signal source locating method
A technology of source location and location method, applied in wireless communication, radio/inductive link selection and arrangement, service based on location information, etc. Capture difficulties and other problems to achieve the effect of solving precise positioning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] Below in conjunction with accompanying drawing the present invention is introduced in further detail:
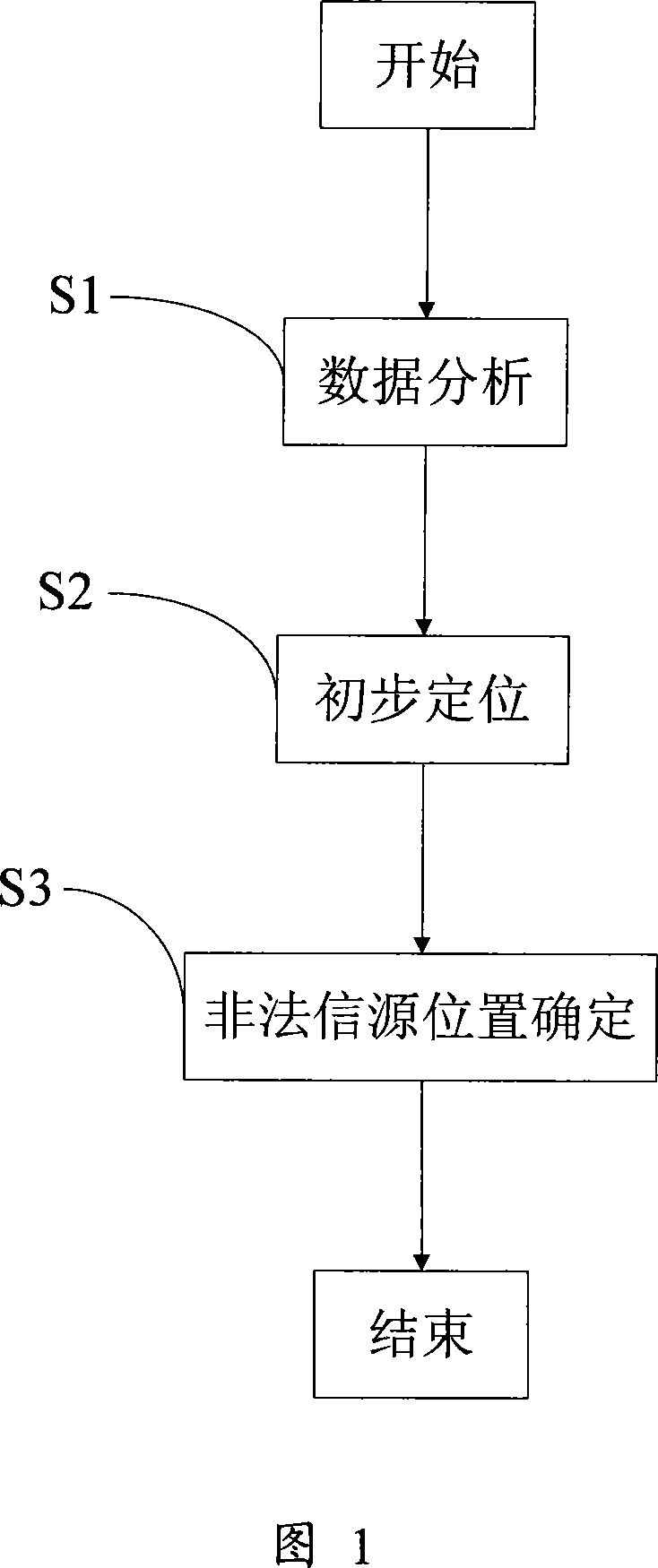
[0014] As shown in Figure 1, a kind of illegal wireless traffic signal source location method of the present invention comprises the following steps:
[0015] S1: Data analysis, preliminary determination of illegal traffic source numbers;
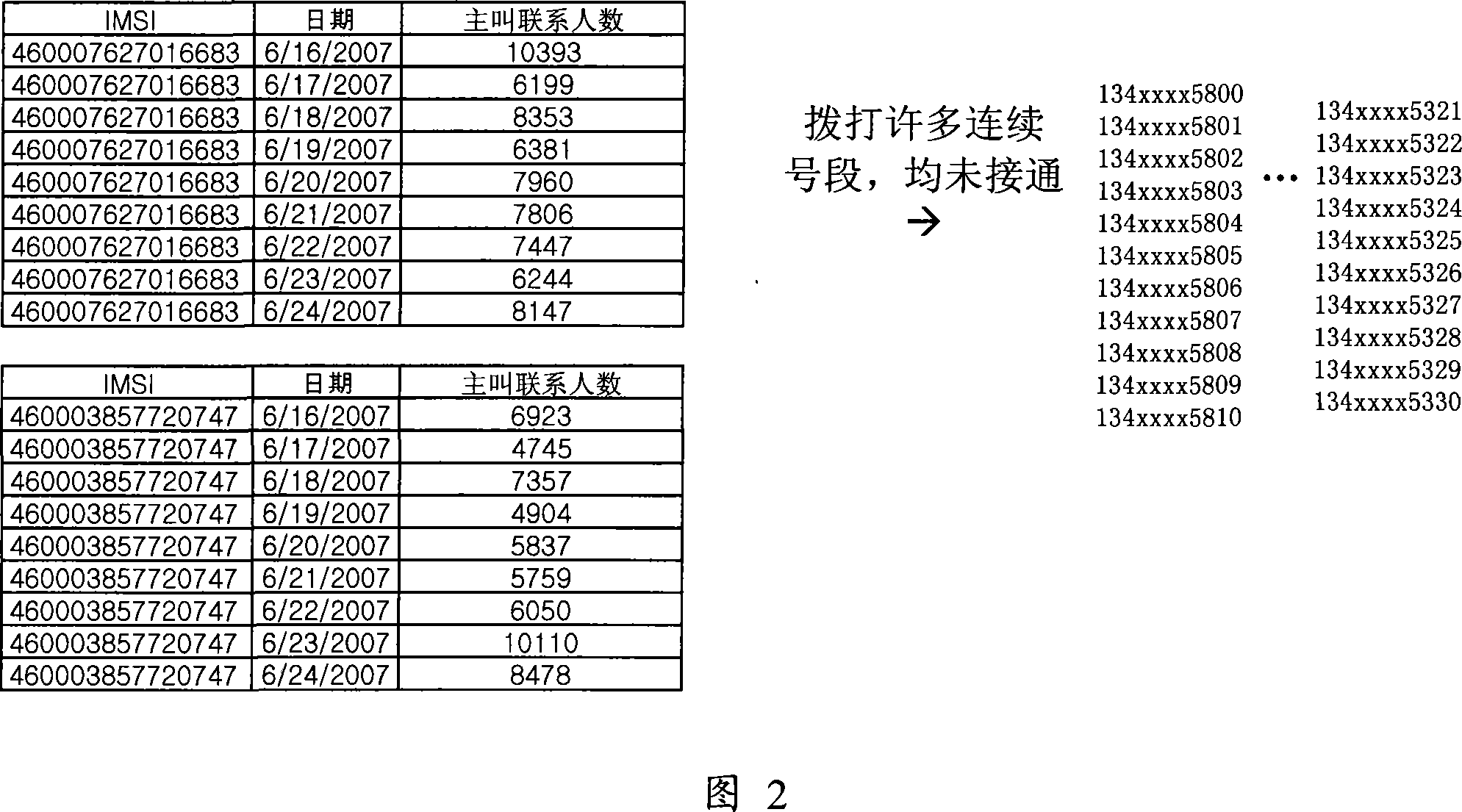
[0016] Through user feedback or the network monitoring system to find out whether there is illegal traffic on the existing network, the network monitoring system will pay attention to the cell with a significant increase in call congestion, for example, the traffic volume of the CELL cell in the entire network at night from 2:00 to 4:00 Sorting is carried out to select the cells whose average busy-hour traffic volume is >10ERL. After observation and analysis, the source of illegal traffic often has the characteristics of "the dialed telephone number is regular and can be followed, which is manifested as "continuously adding "1" to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com