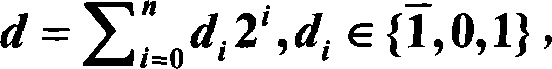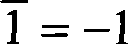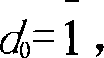Elliptic curve anti-bypass attack method based on randomizing multiplication with symbol scalar
A technology of randomizing strips and elliptic curves, applied in the field of information security, can solve problems such as intermediate states, limited intermediate states, and intermediate state collision attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The embodiments of the present invention are described in detail below: the present embodiment is implemented under the premise of the technical solution of the present invention, and detailed implementation and specific operation process are provided, but the protection scope of the present invention is not limited to the following implementation example.
[0019] Assume that the embodiment intends to perform elliptic curve encryption processing on the plaintext M using the key k. According to the elliptic curve cryptosystem, the plaintext M is first converted into a point Q on a certain elliptic curve, and then the point representation of the ciphertext on the same elliptic curve is obtained by calculating the scalar multiplication P=kQ of the points on the elliptic curve. Under the whole invention realization process:
[0020] 1. First represent the key k in randomized BSD form. Suppose the binary representation of the key k is k = ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com