An organization structure and maintenance method of security context in media accessing control system
A medium access control, context technology, applied in security devices, key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0126] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
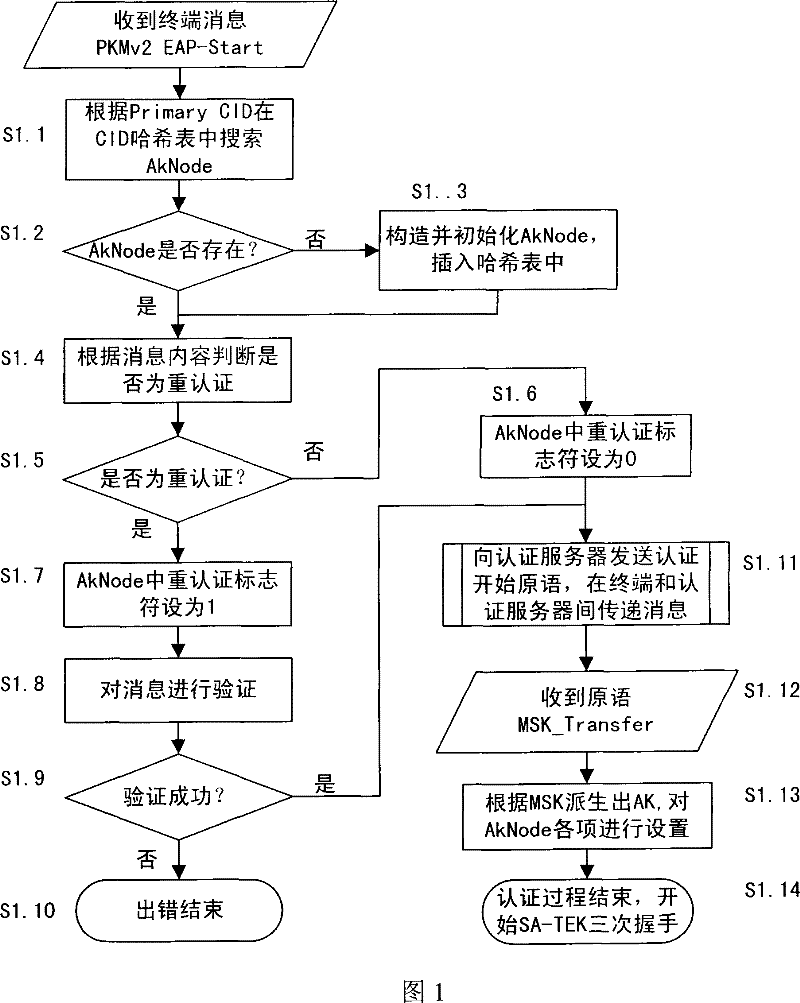
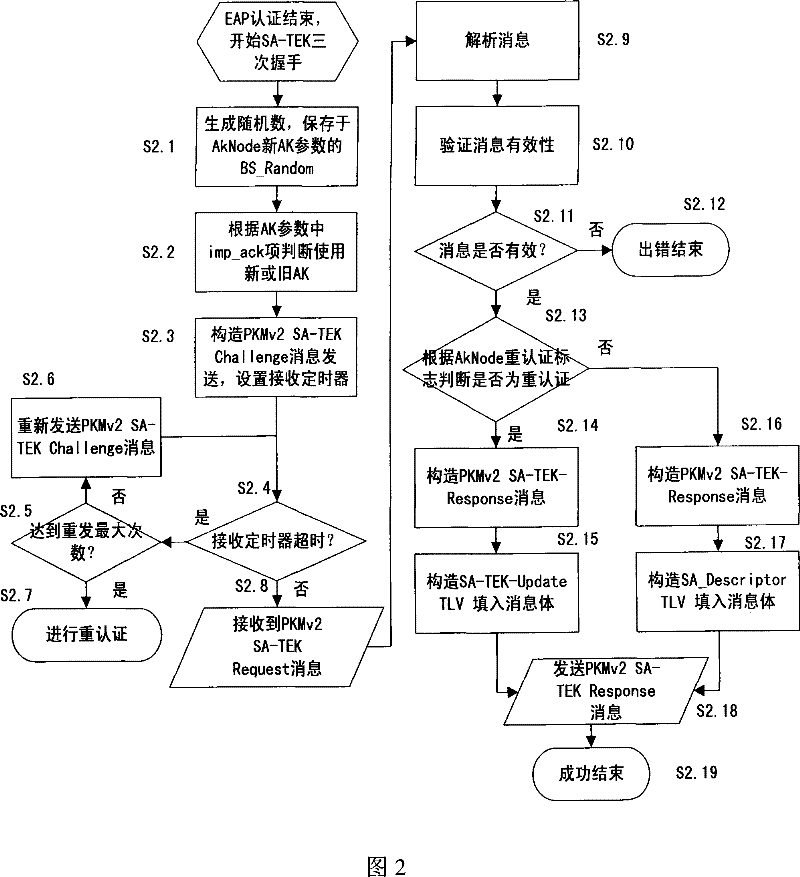
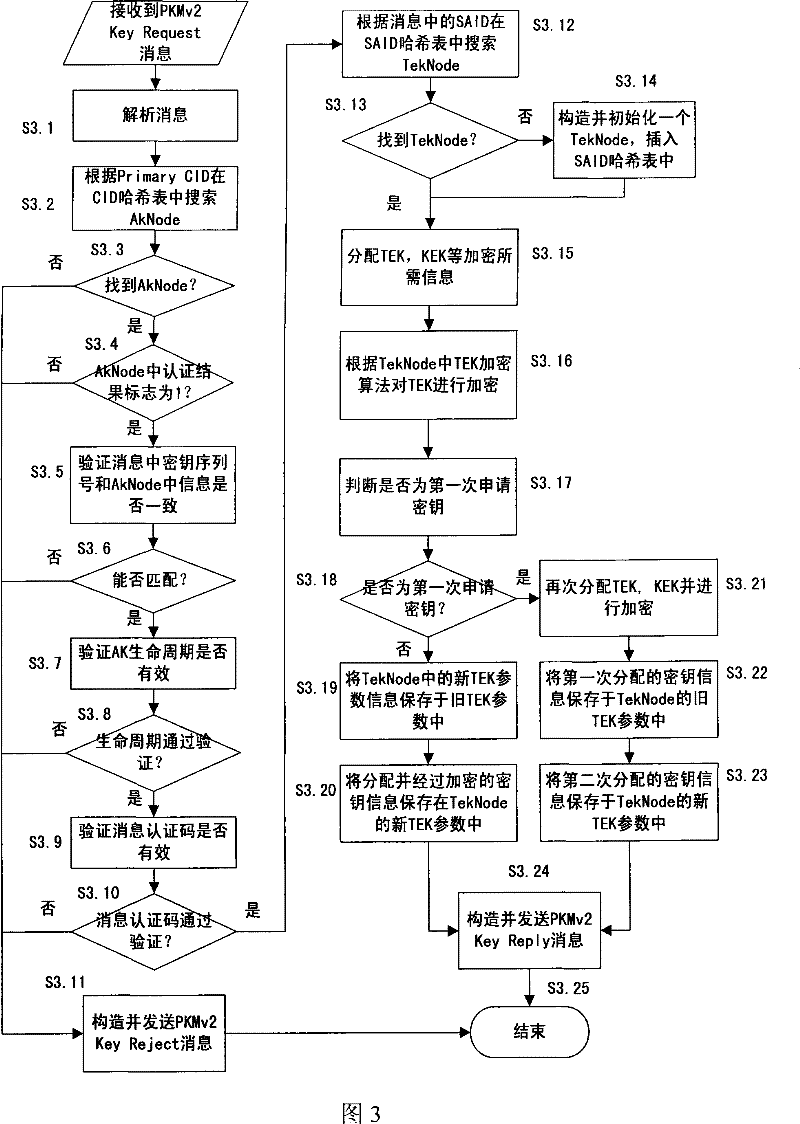
[0127] The security context corresponding to the terminal is divided into the authorization key (AK) context and the communication encryption key (TEK) context. The key context includes key value, key serial number, key life cycle and other information.
[0128] As an implementable manner, the organizational structure of the security context in the media access control system of the present invention includes:
[0129] A hash table of Connection IDs (CIDs) used to manage authorization key contexts.
[0130] Preferably, the connection identifier (CID) hash table is indexed by the main management connection identifier of the terminal, and its entry points to a queue composed of authorized key context nodes (AkNode), and the authorized key context node (AkNode ) to save the authorization key context, including the following information:...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com