Garbage recovery mobile communication terminal of Java virtual machine and recovery method thereof
A technology of mobile communication terminal and java virtual machine, which is applied in the field of mobile communication terminals for garbage collection, can solve problems such as inability to control the timing of garbage collection, and achieve the effect of ensuring accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical features of the present invention will be described in detail below in conjunction with the embodiments and accompanying drawings.
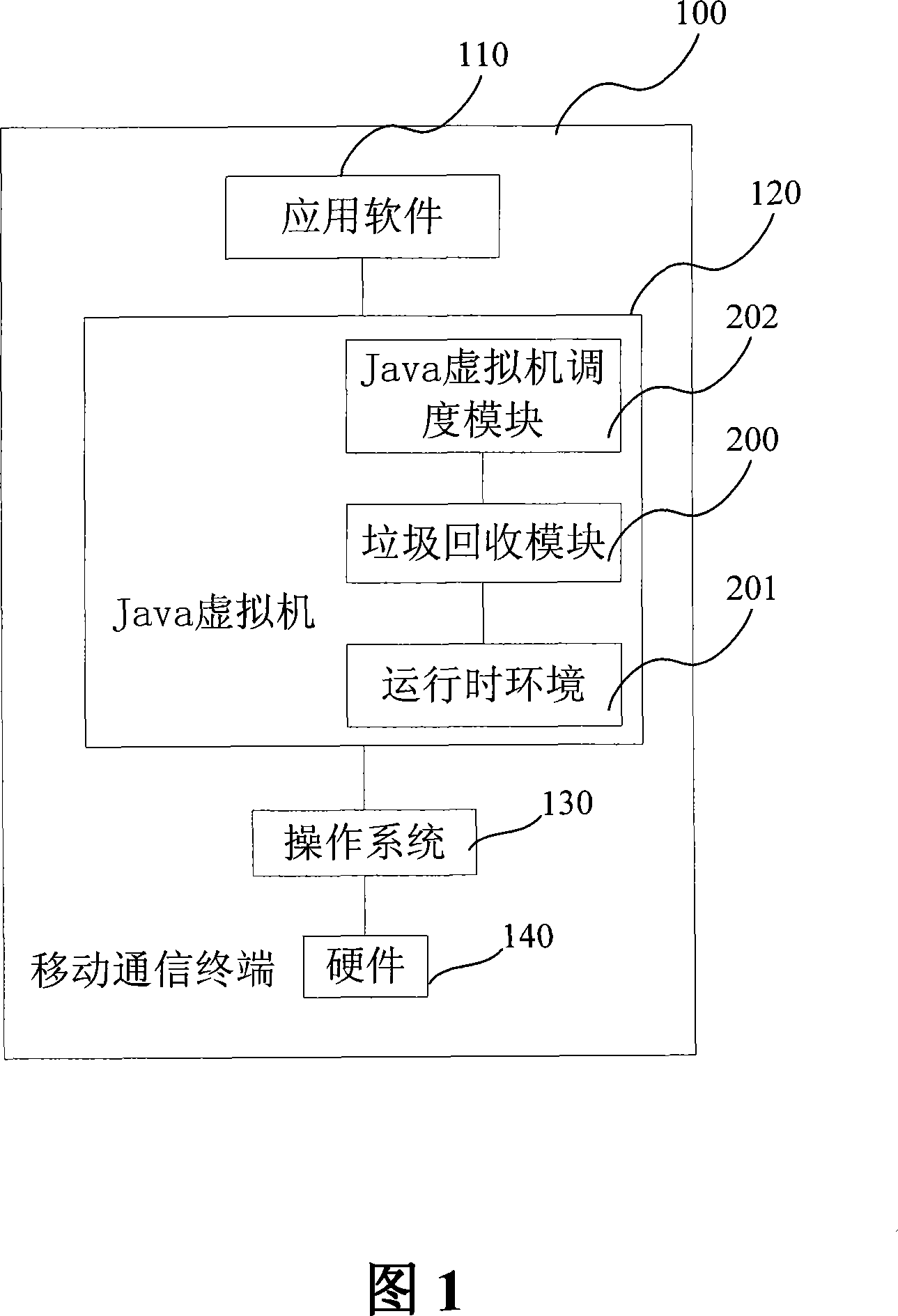
[0042] As shown in Figure 1, it is a schematic diagram of the overall structure of the present invention.
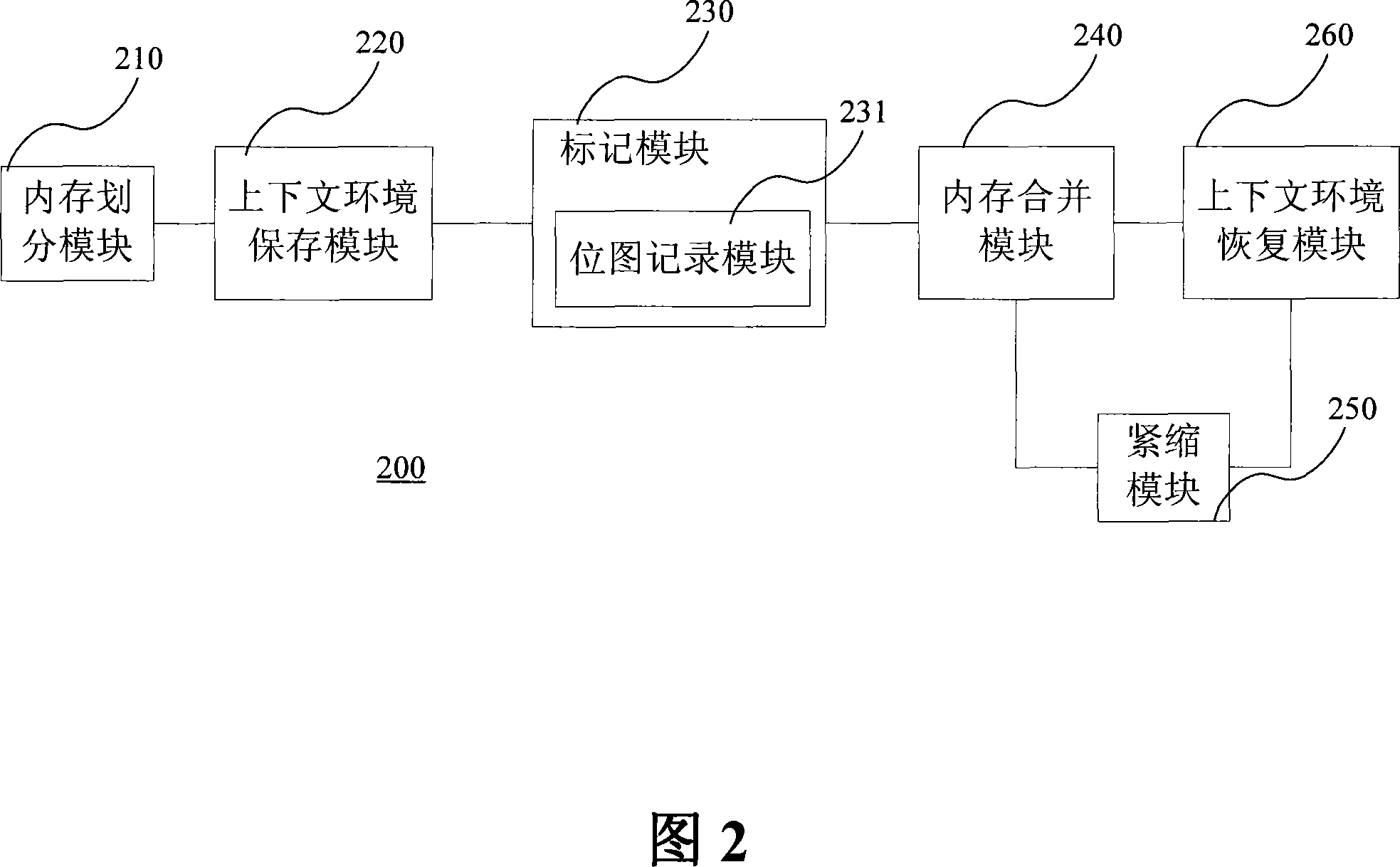
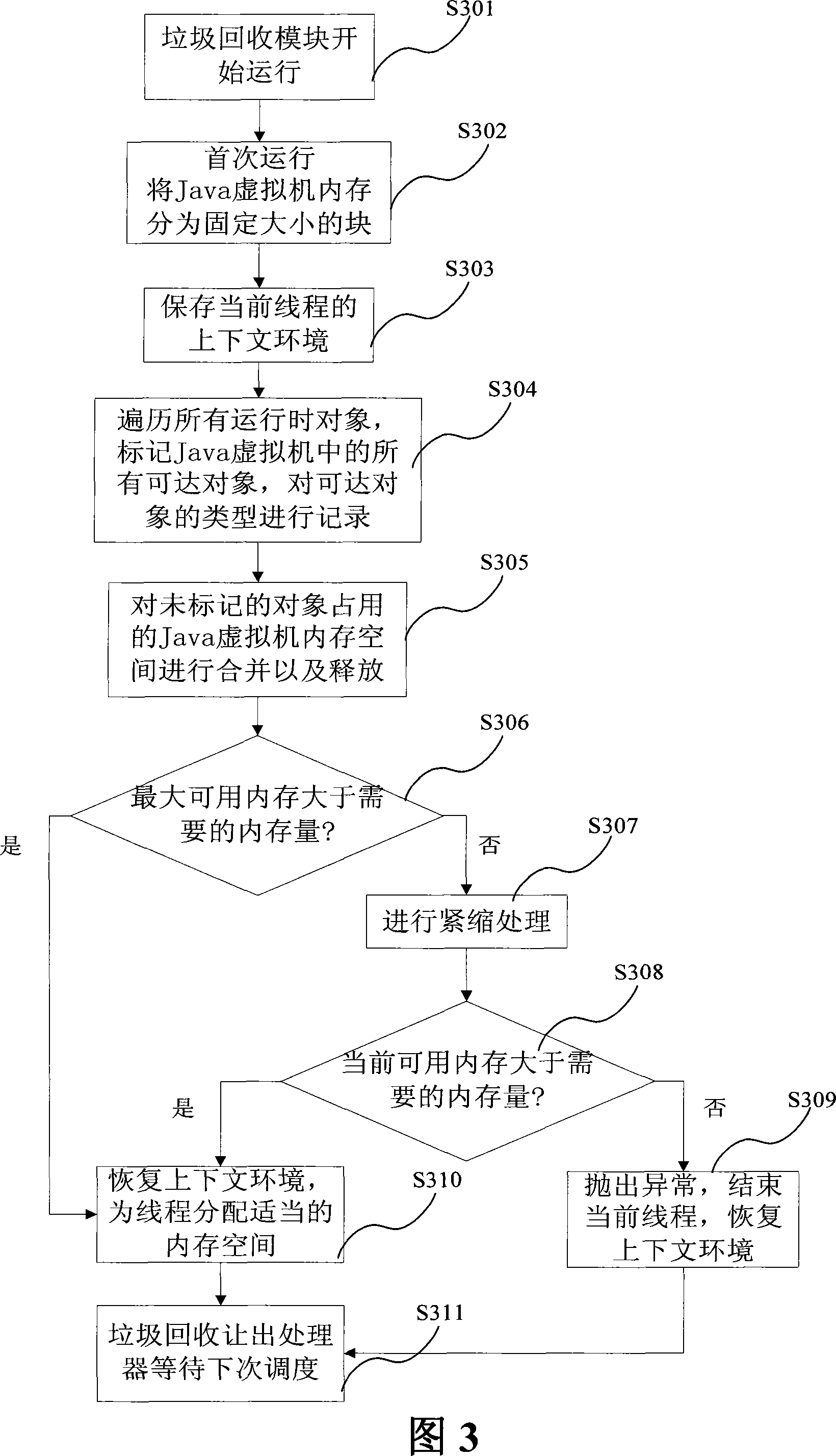
[0043] In the mobile communication terminal 100 , the operating system 130 runs on the hardware 140 , and the Java virtual machine 120 performs related operations based on the operating system 130 to provide a running platform for each application software 110 . The mobile communication terminal 100 includes a mobile phone, a PDA, and the like. The Java virtual machine 120 includes various functional modules such as a garbage collection module 200 , a runtime environment 201 , and a Java virtual machine scheduling module 202 . The garbage collection module 200 will perform garbage collection operations on the runtime environment 201 . The runtime environment 201 refers to the method area, heap, execution stack and reg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com