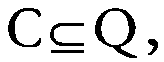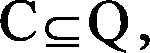Network intrude detecting method based on inherent subsequence mode decomposition
A network intrusion detection and pattern decomposition technology, which is applied in the field of network intrusion detection, can solve problems such as practical difficulties, large amount of calculation, and complicated NativeAPI calling process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0085] The present invention is further described below in conjunction with embodiment.
[0086] 1. Network data acquisition and preprocessing
[0087] This program uses WINCAP to intercept network data packets. WINPCAP is a third-party software driver package applied to Windows platform for data packet capture and network analysis. It provides Windows applications with the ability to access the bottom layer of the network. The main idea comes from the Unix system. The famous BSD packet capture framework. The basic architecture of WINPCAP consists of three modules.
[0088] 1. NPF (Network Packet Filter) is the core component of the WINPCAP architecture. It works at the core level of the system and is used to filter data packets and add information such as time stamps and data packet lengths to the packets. NPF directly obtains the data packet from the data link layer through NDIS, and forwards it to the application layer program without modification. NPF also allows users ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com