Stream media hidden communication method based on hierarchical model
A covert communication and layered model technology, applied in the field of streaming media information hiding, can solve the problems of lack of data transmission integrity, inconvenient covert communication system interoperability, and application support of covert communication systems are not considered.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0164] The network address of the user 1 terminal is set to 192.168.1.2, the network address of the user 2 terminal is set to 192.168.1.3, and the voice compression coding method is selected as G.711u.
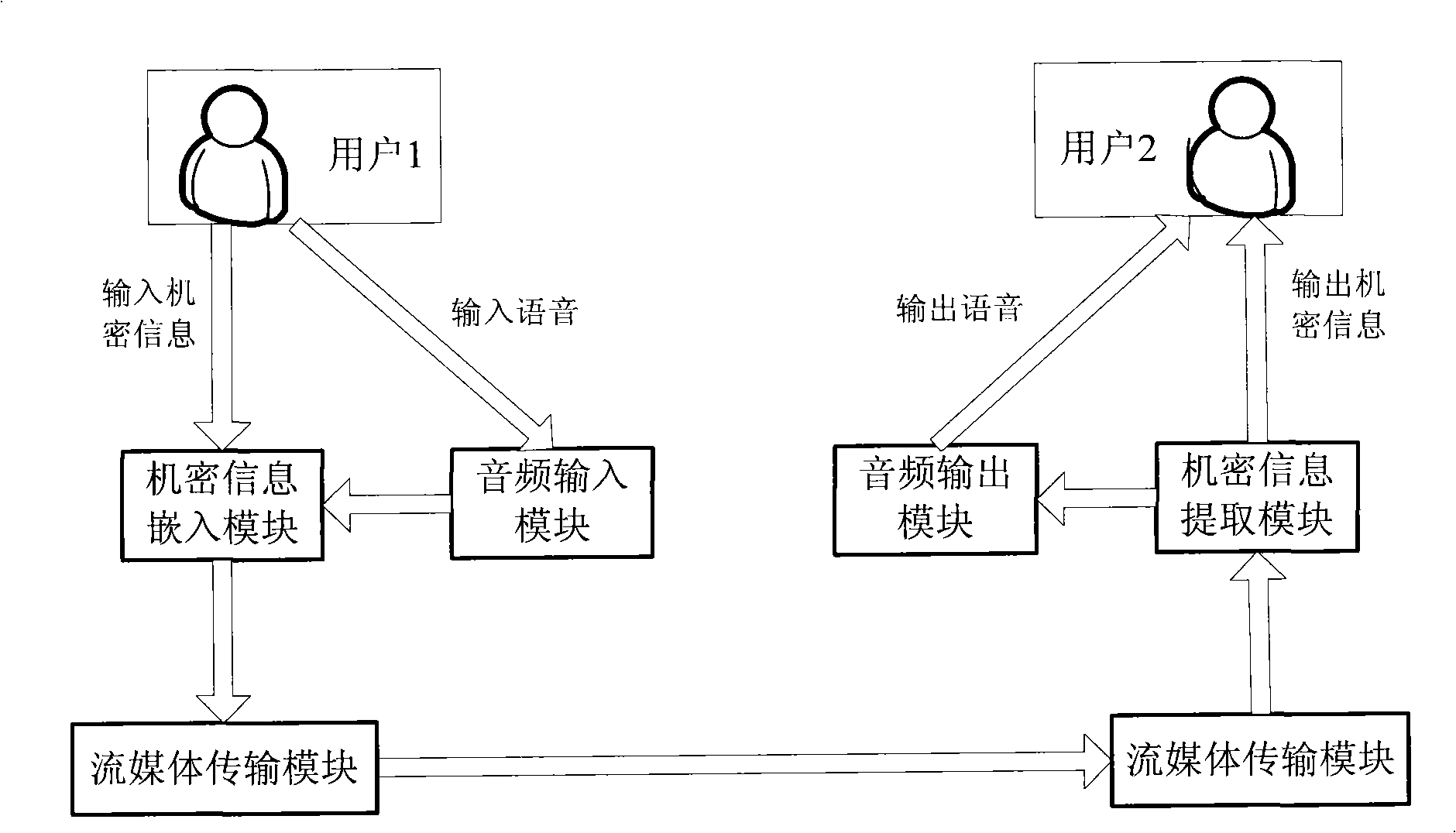
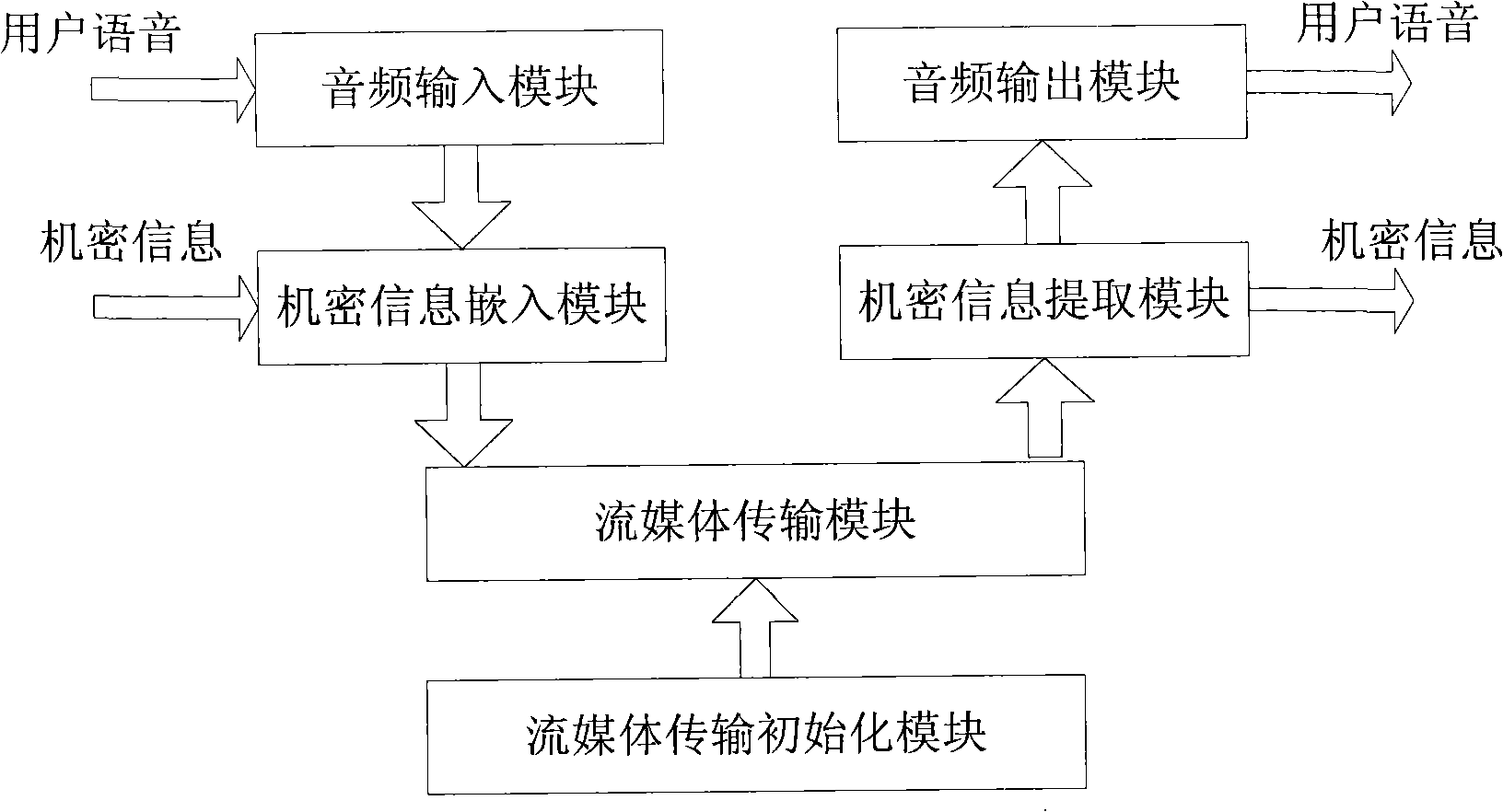
[0165] User 1 inputs the network address of destination terminal user 2 on the system interface, and sends a stream media transmission request to user 2. After user 2 receives the streaming media transmission request from user 1, user 2 agrees to streaming media transmission, and sends a consent request to user 1. After user 1 receives the message from user 2 agreeing to streaming media transmission, it will reply a confirmation message to user 2. At the same time, the microphone of user 1 terminal starts to collect voice, and compresses the collected voice data into G.711 coded files. The encoded file is encapsulated into an RTP data packet and sent to the destination end user 2 through the network. After receiving the confirmation message from user 1, user 2 also starts to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com