Credible safety computer
A safe computer and safe technology, applied in the computer field, can solve the problems of functional limitations, emergency destruction of key data without integration, low coupling degree, etc., to achieve the effect of increasing difficulty and solving real-time encrypted storage problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
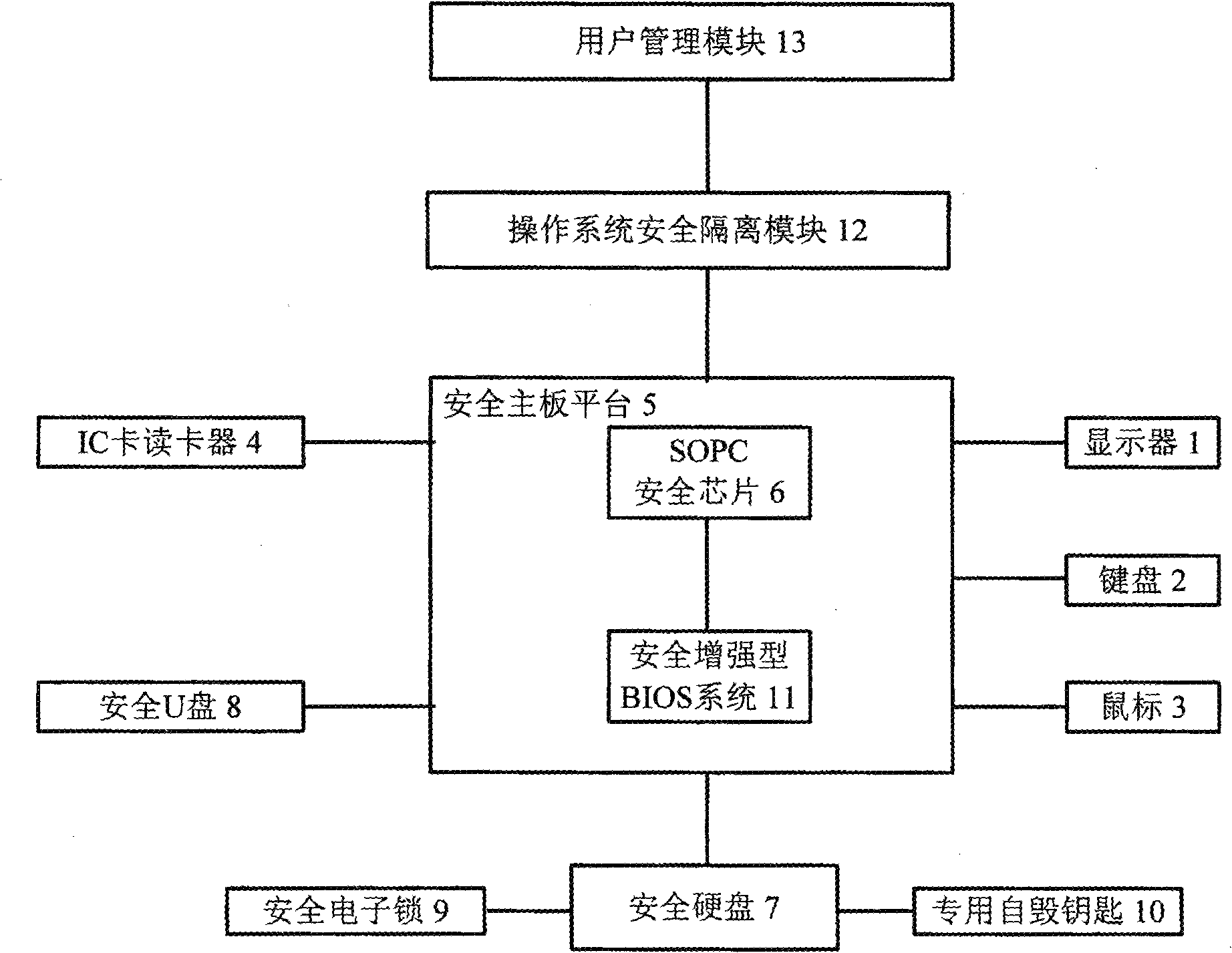
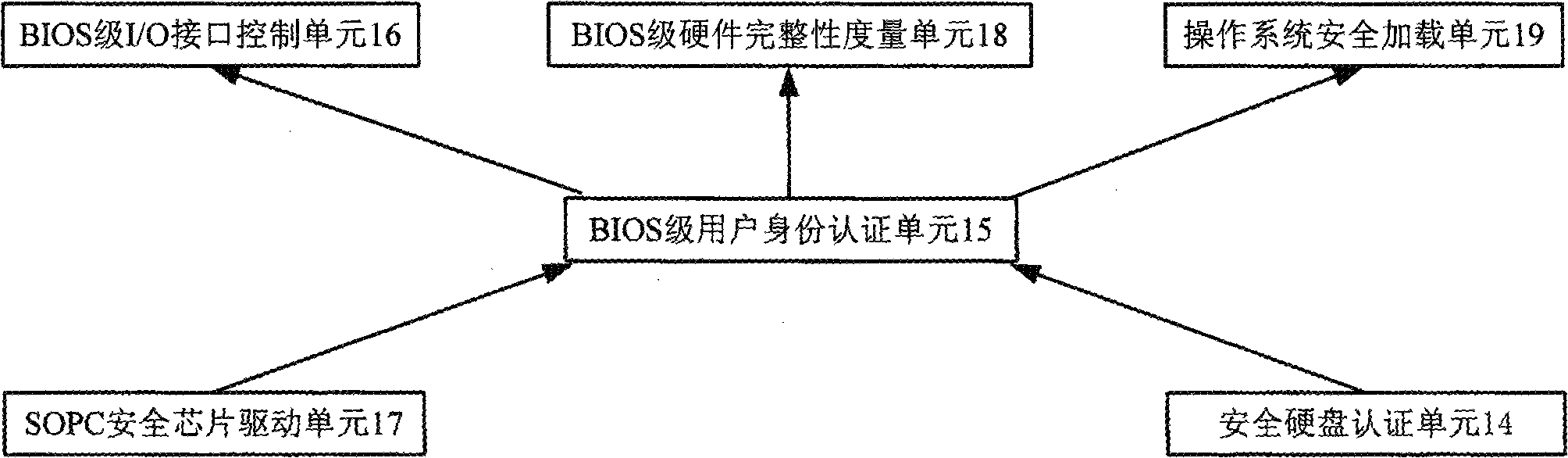
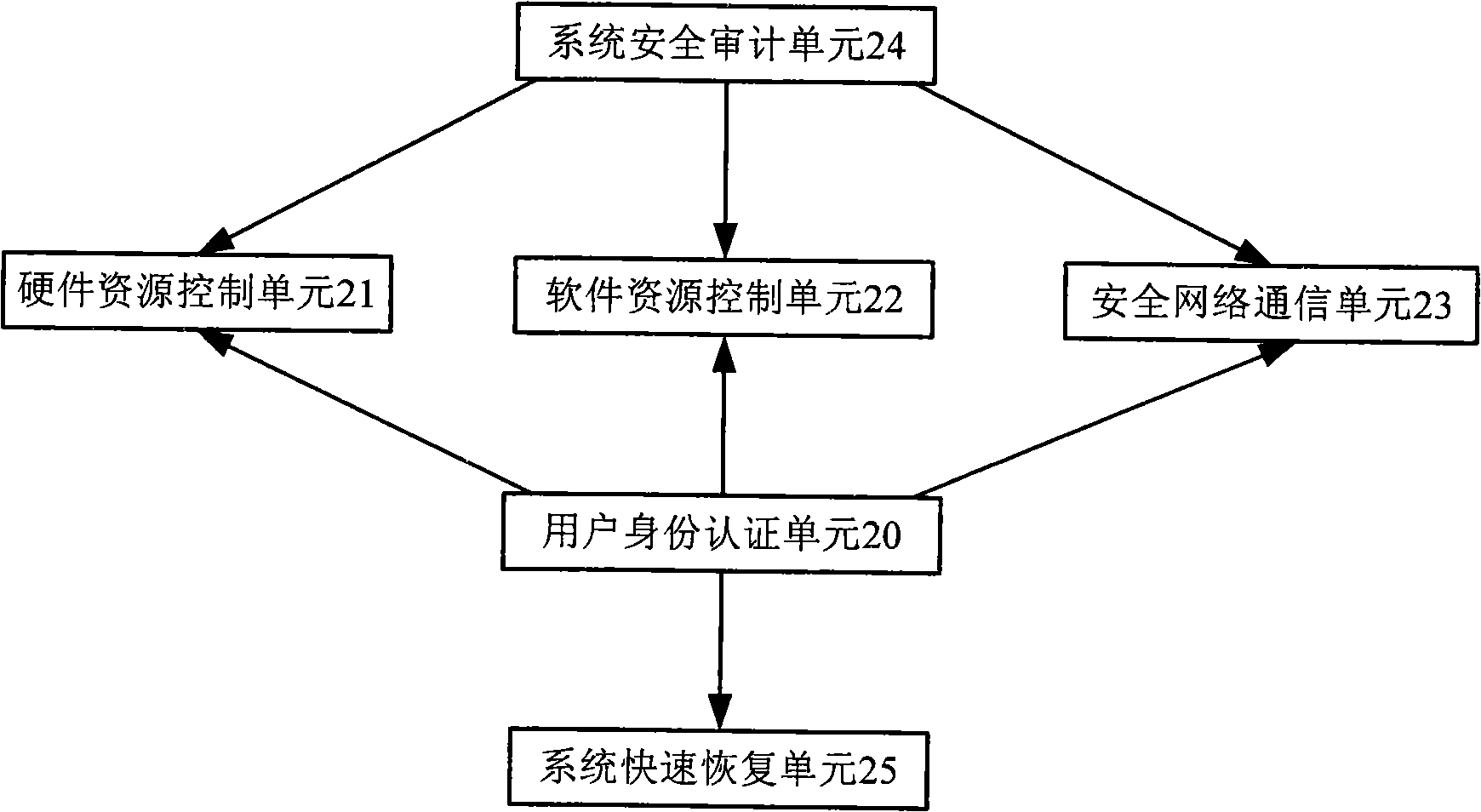
[0019] A credible and secure computer, including a monitor 1, a keyboard 2, a mouse 3, an IC card reader 4, and a secure motherboard platform 5, a secure hard disk 7, a secure U disk 8, a secure electronic lock 9, and a special self-destruction key 10 , operating system safety isolation module 12 and user management module 13, wherein the safety motherboard platform 5 includes SOPC security chip 6 and safety enhanced BIOS system 11, and safety enhanced BIOS system 11 includes safe hard disk authentication unit 14, BIOS level user identity authentication unit 15. BIOS level I / O interface control unit 16, SOPC security chip drive unit 17, BIOS level hardware integrity measurement unit 18 and operating system security loading unit 19, operating system security isolation module 12 includes user identity authentication unit 20, hardware resources A control unit 21 , a software resource control unit 22 , a safety network communication unit 23 and a system quick recovery unit 25 .
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com