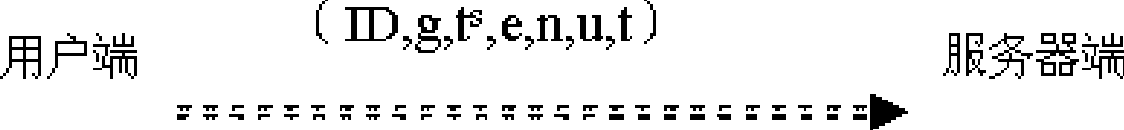One-time password authentication method
A password authentication and one-time technology, which is applied in the direction of user identity/authority verification, etc., can solve the problems of difficult one-time encryption, troublesome keys, and inability to obtain ciphertext, etc., to achieve the reduction of computational complexity and the improvement of security performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
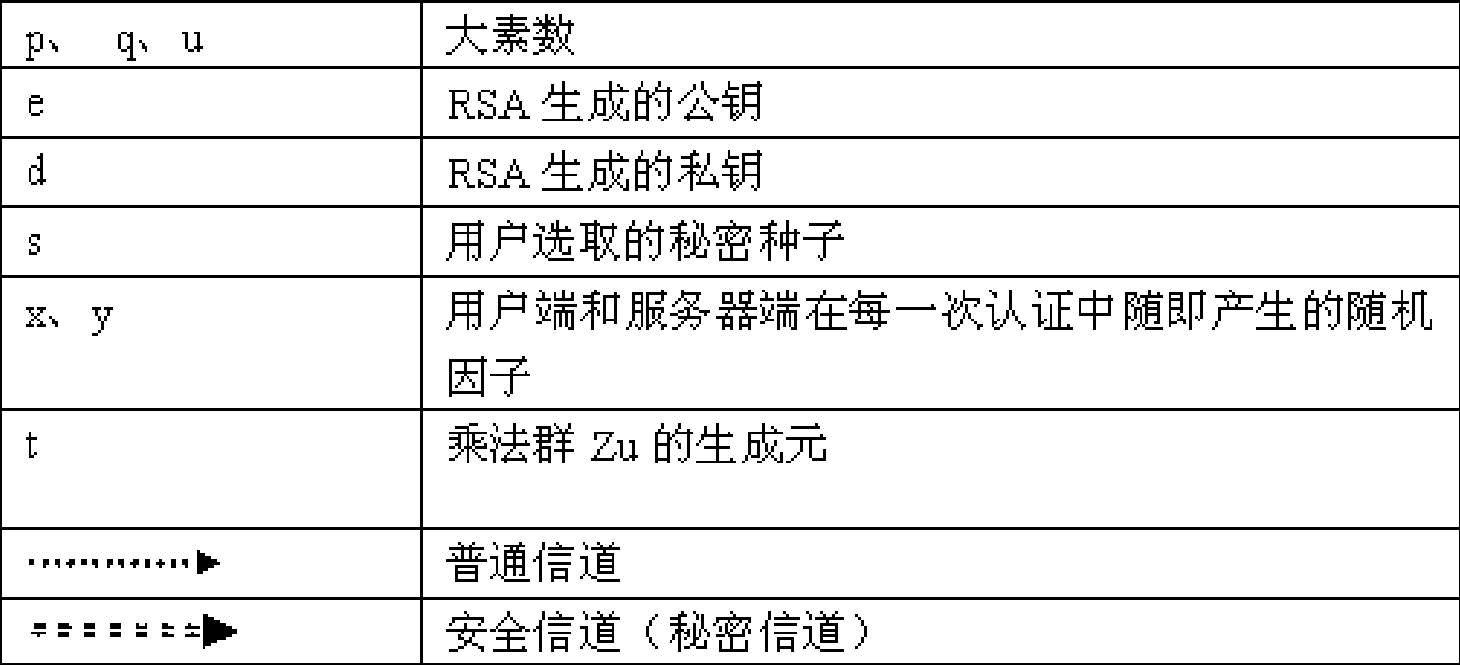
[0019] The symbol that embodiment adopts is as shown in the table:
[0020]
[0021] The main steps of the authentication method are as follows:
[0022] A. Registration phase (Registration)
[0023] (1) Generate a key pair e, d based on the RSA algorithm;
[0024] a) The client randomly selects two large prime numbers p and q, calculates n=pq, ¢(n)=(p-1)(q-1), and p, q, ¢(n) are kept secret by the user;
[0025] b) Select public key e: 1
[0026] c) Find the private key d: make de=1mod ¢(n), and the d user keeps it secret;
[0027] Then there are: any g∈Z n , g is Z n A primitive element of g with g ed =g modn established.
[0028] (2) Generate the authentication basis t based on the discrete logarithm problem on the finite field;
[0029] a) The client generates another large prime number u, t∈Z u is a primitive element;
[0030] b) Randomly select your own secret seed s (1≤s≤u-1), and the s user keeps it secret;
[0031] c) Calcu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com