Detection method and system for protocol format exception
A protocol format, anomaly detection technology, applied in transmission systems, digital transmission systems, instruments, etc., can solve problems such as lack, and achieve the effect of convenient expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
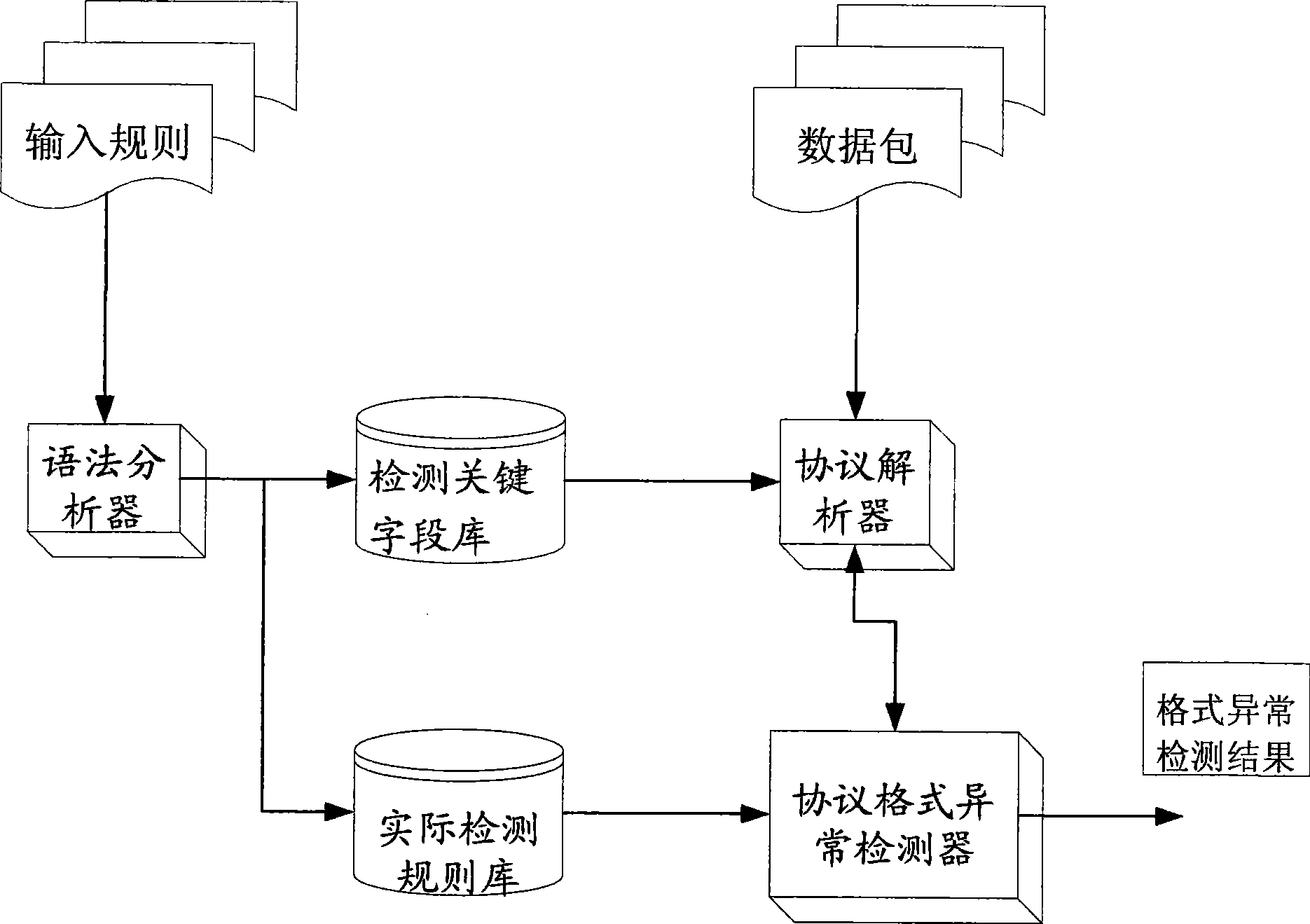
[0020] This embodiment is the basic mode of the protocol format anomaly detection method, and the system used is such as figure 1 shown. Including detection key field library, actual detection rule library, syntax analyzer, protocol parser, protocol format anomaly detector, the operation process is as follows figure 2 Shown:
[0021] ① Steps to establish the key field library for detection. The establishment of the detection key field library includes the formulation of the initial rule grammar, the verification of the grammar explanation, and the extraction and storage of key fields. For the protocol field targeted by some attacks, the unified pattern of the attack is found, and the combination of the attacked protocol field and the attack pattern is input as the initial rule. The detection rules that are initially set are the initial rules. Then call the lexical analyzer to perform grammatical analysis on the initial rule, and perform lexical segmentation on the input s...
Embodiment 2
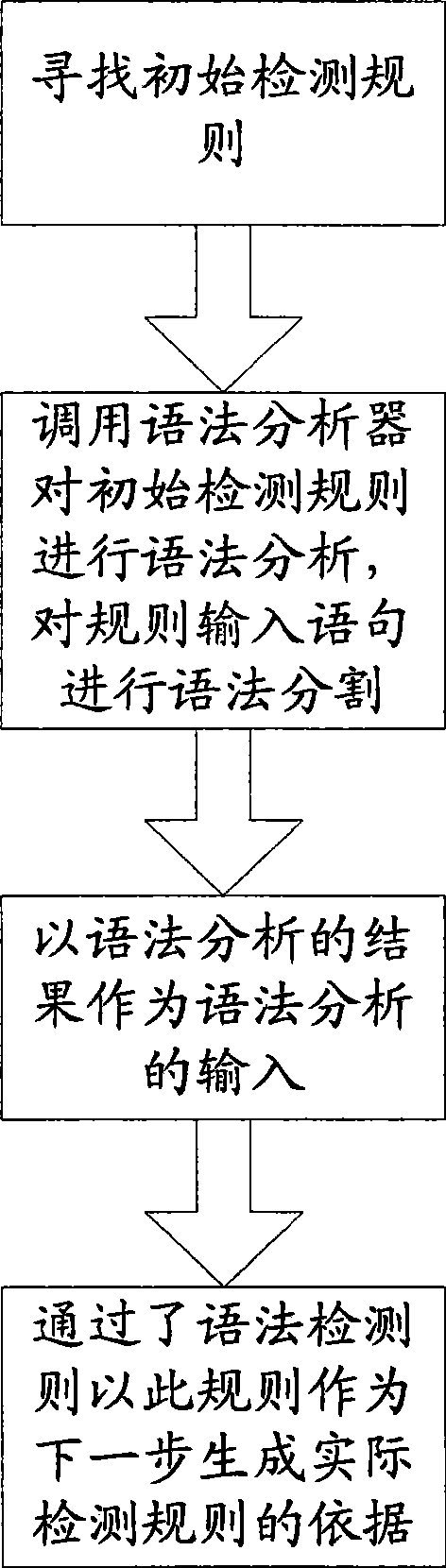
[0026] This embodiment is an optimal scheme for formulating initial input rule syntax in the step of establishing the detection key field library in the first embodiment. Run the process as image 3 shown.
[0027] ① For the protocol field targeted by some attacks, look for the unified pattern of the attack, and combine the attacked protocol field and the attack pattern as the input of the rule, which is a substep of the initial rule.
[0028] ② Invoke the syntax analyzer to perform syntax analysis on the initial detection rules, and carry out the sub-step of syntax segmentation on the input sentences of the rules.
[0029] ③Using the result of grammatical analysis as the input of grammatical analysis, so as to judge whether the input rule conforms to the preset grammatical rule sub-step.
[0030] ④ If the grammar test is passed, it means that the rule conforms to the preset grammar rule, then use this rule as the basis sub-step for generating the actual test rule in the nex...
Embodiment 3
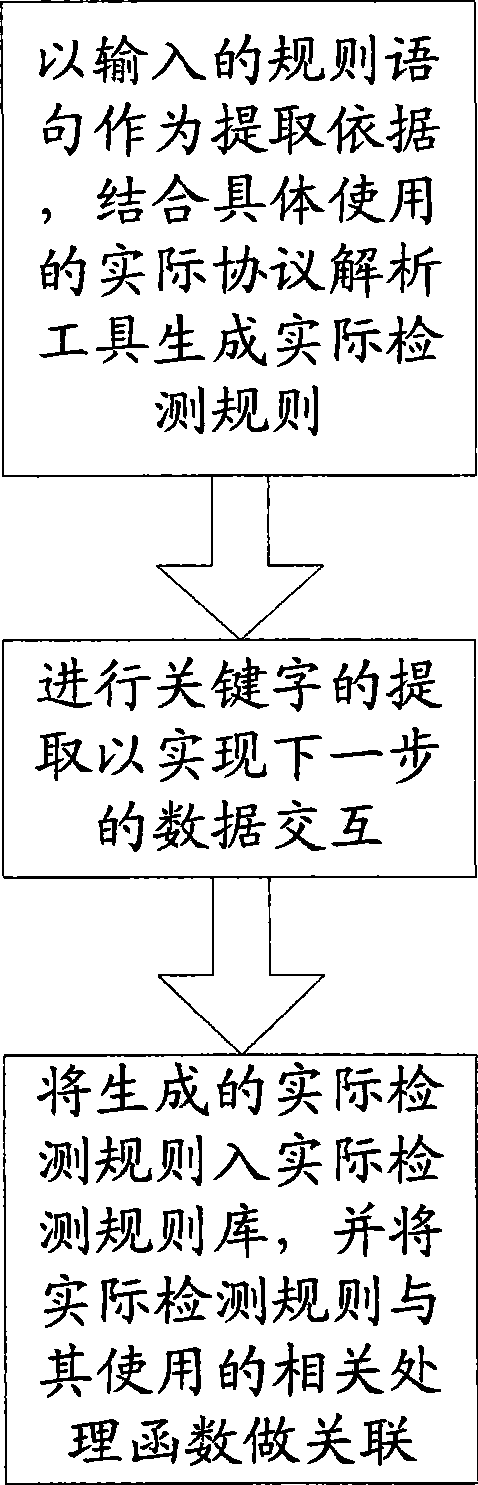
[0034]This embodiment is an optimal solution of the step of establishing the actual detection rule base in the first embodiment. Run the process as Figure 4 shown
[0035] ① The sub-step of generating the actual detection rules based on the syntax-checked input rule statement combined with the actual protocol analysis tool used.
[0036] ②Extract keywords to realize the sub-step of data interaction in the next step.
[0037] ③ Put the generated actual detection rules into the actual detection rule base, and associate the actual detection rules with the relevant processing functions used.
[0038] The keyword extraction method relies on the formulation of the initial rule input grammar, which can automatically match the position of the key field in the detection rule, and accurately extract the corresponding key field that needs to be detected for format anomalies.
[0039] After obtaining the output result of the yacc syntax detection, it is necessary to combine a specific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com