Integrity checking method in document transmission
A technology for integrity verification and file transfer, which is applied in the field of verification in file transfer, can solve the problems of affecting transmission speed, consuming large resources, network congestion, etc., to reduce bandwidth and resource occupancy, reduce equipment pressure, and ensure full effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
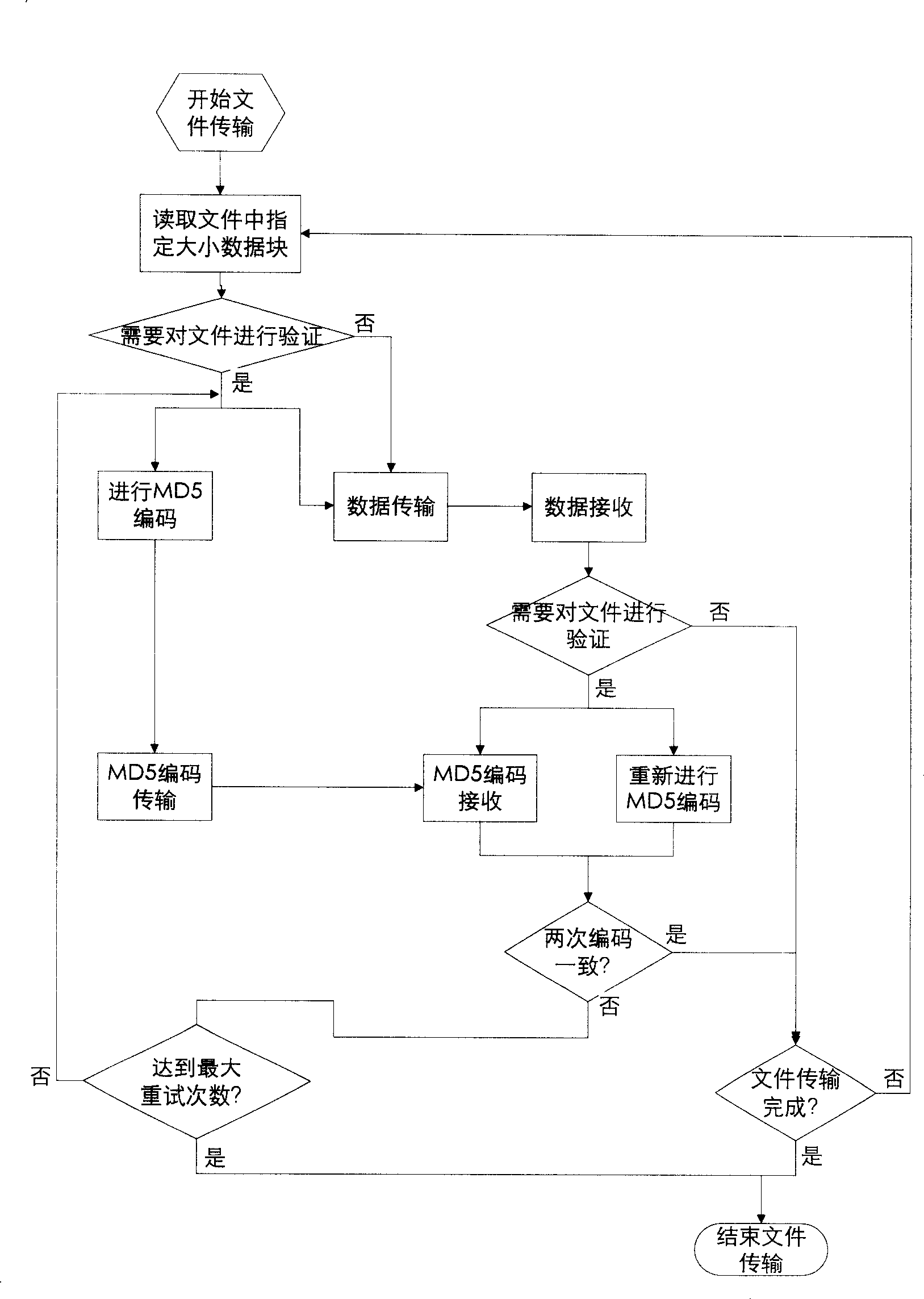
[0022] In the transmission process, under normal circumstances, the work that the server end of this embodiment (i.e. the data sending end) needs to do is as follows: read the content of the local physical file to the memory; use the specified integrity algorithm to calculate the data in the memory A message digest of the data; send the data and the data message digest to the network.
[0023] The client of this embodiment (ie, the data receiving end) needs to do the following work: accept data transmission from the network; use a specified integrity algorithm to verify the received data; write the verified data into a local physical file.
[0024] In this embodiment, the file first needs to be divided into blocks. For the size of each block of the file block, various elements of the network, summary, and hard disk should be considered at the same time. Generally speaking, the data size of the sub-file block is preferably an integer multiple of 256, and the data size of the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com